Stateful firewalls monitor the full state of active connections, allowing them to make more informed decisions based on the context of traffic, which enhances security by tracking session information. Stateless firewalls, on the other hand, filter packets solely based on predefined rules without regard to connection states, offering faster processing but less comprehensive protection. Choosing between stateful and stateless firewalls depends on the balance between security needs and network performance requirements in a security pet environment.
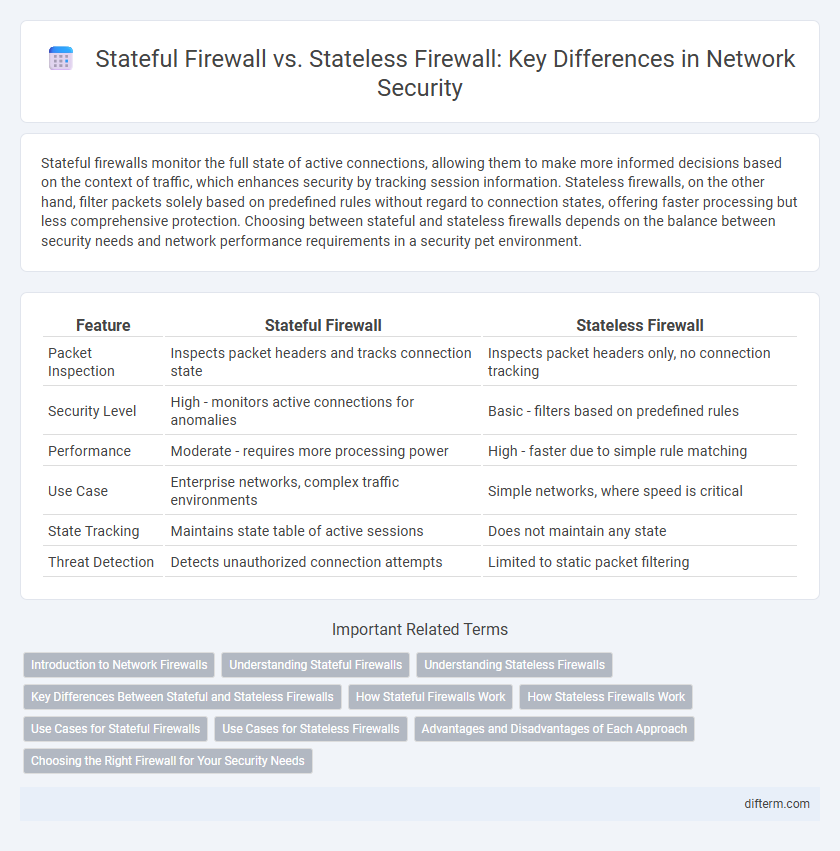
Table of Comparison
| Feature | Stateful Firewall | Stateless Firewall |
|---|---|---|
| Packet Inspection | Inspects packet headers and tracks connection state | Inspects packet headers only, no connection tracking |
| Security Level | High - monitors active connections for anomalies | Basic - filters based on predefined rules |
| Performance | Moderate - requires more processing power | High - faster due to simple rule matching |
| Use Case | Enterprise networks, complex traffic environments | Simple networks, where speed is critical |
| State Tracking | Maintains state table of active sessions | Does not maintain any state |
| Threat Detection | Detects unauthorized connection attempts | Limited to static packet filtering |
Introduction to Network Firewalls
Stateful firewalls monitor the state of active connections and make decisions based on the context of traffic, enabling more granular and dynamic security policies. Stateless firewalls filter packets individually based on predefined rules without considering the connection state, resulting in faster but less intelligent filtering. Understanding these differences is crucial for designing effective network security architectures that balance performance and protection.
Understanding Stateful Firewalls
Stateful firewalls monitor the full state of active network connections by tracking and analyzing packet attributes such as source and destination IP addresses, port numbers, and connection status. This enables them to make more intelligent decisions by allowing or blocking traffic based on the context of the entire communication session rather than individual packets alone. Their ability to maintain connection states enhances protection against unauthorized access, ensuring robust network security compared to stateless firewalls.
Understanding Stateless Firewalls
Stateless firewalls filter network traffic based on predefined rules such as IP addresses, ports, and protocols without maintaining any session information or context. This lack of state tracking allows for faster packet processing but makes stateless firewalls less effective against complex or multi-packet attacks. Understanding stateless firewalls is crucial for implementing basic perimeter security where speed and simplicity are prioritized over deep traffic inspection.
Key Differences Between Stateful and Stateless Firewalls
Stateful firewalls monitor the state of active connections and make decisions based on the context of traffic, while stateless firewalls filter packets purely based on predefined rules without considering connection states. Stateful firewalls maintain a session table to track all ongoing communications, enabling more precise control over inbound and outbound data flows compared to stateless firewalls that evaluate each packet individually. This fundamental difference impacts the effectiveness of threat detection, with stateful firewalls providing enhanced protection against complex attacks by recognizing patterns in network traffic.
How Stateful Firewalls Work
Stateful firewalls monitor the full state of active network connections by tracking packet sequences and connection states in a state table. They analyze both incoming and outgoing packets, allowing decisions based on context such as established sessions, IP addresses, and port numbers. This dynamic inspection enhances security by enabling the firewall to allow legitimate traffic while blocking unauthorized or unsolicited packets.
How Stateless Firewalls Work
Stateless firewalls operate by inspecting each incoming packet individually, without considering any context or connection state, using predefined static rules to permit or block traffic based solely on IP addresses, ports, and protocols. They quickly filter traffic by matching packets against rule sets but lack the ability to track session information or ensure packets are part of an established connection. This simplicity enables fast processing but makes stateless firewalls less effective against sophisticated attacks compared to stateful firewalls.
Use Cases for Stateful Firewalls
Stateful firewalls are ideal for environments requiring deep packet inspection and continuous monitoring of active connections, such as enterprise networks handling sensitive data or complex applications. They excel in scenarios where tracking the state and context of network traffic is critical for preventing unauthorized access and mitigating sophisticated cyber threats. Stateful firewalls are commonly deployed in corporate data centers, cloud infrastructures, and secure remote access gateways to enforce dynamic security policies based on connection state information.
Use Cases for Stateless Firewalls
Stateless firewalls are ideal for high-speed filtering in environments requiring simple, rule-based packet inspection without maintaining connection state, such as perimeter security for IoT devices and edge routers. These firewalls efficiently handle large volumes of traffic by analyzing packets independently, making them suitable for DMZ segments where speed is critical and complex session tracking is unnecessary. Stateless firewalls also excel in scenarios where resource constraints demand minimal processing overhead, ensuring fast throughput with straightforward access control lists.
Advantages and Disadvantages of Each Approach
Stateful firewalls maintain context by tracking active connections, enabling more precise filtering and protection against unauthorized access, but they require more memory and processing power, potentially impacting performance in high-traffic environments. Stateless firewalls filter packets individually based on predetermined rules, offering faster processing and lower resource consumption but lacking the ability to detect complex or session-based attacks. Choosing between them depends on network size, security requirements, and performance considerations.
Choosing the Right Firewall for Your Security Needs
Stateful firewalls monitor active connections and make decisions based on the context of traffic, offering robust protection against complex attacks, while stateless firewalls filter packets independently, providing faster performance but less security. Choosing the right firewall depends on your network's complexity, security requirements, and performance needs; stateful firewalls suit environments requiring detailed inspection, whereas stateless firewalls are ideal for high-speed, low-risk scenarios. Prioritizing criteria such as throughput capacity, intrusion detection capabilities, and protocol support ensures optimal firewall selection for effective threat mitigation.
Stateful Firewall vs Stateless Firewall Infographic
 difterm.com
difterm.com