Brute force attacks involve systematically trying every possible combination of passwords until the correct one is found, making them time-consuming but effective against weak passwords. Dictionary attacks use a precompiled list of common passwords and phrases to quickly guess credentials, targeting users who choose easily guessable passwords. Both methods highlight the importance of strong, complex passwords and multi-factor authentication to enhance security.
Table of Comparison
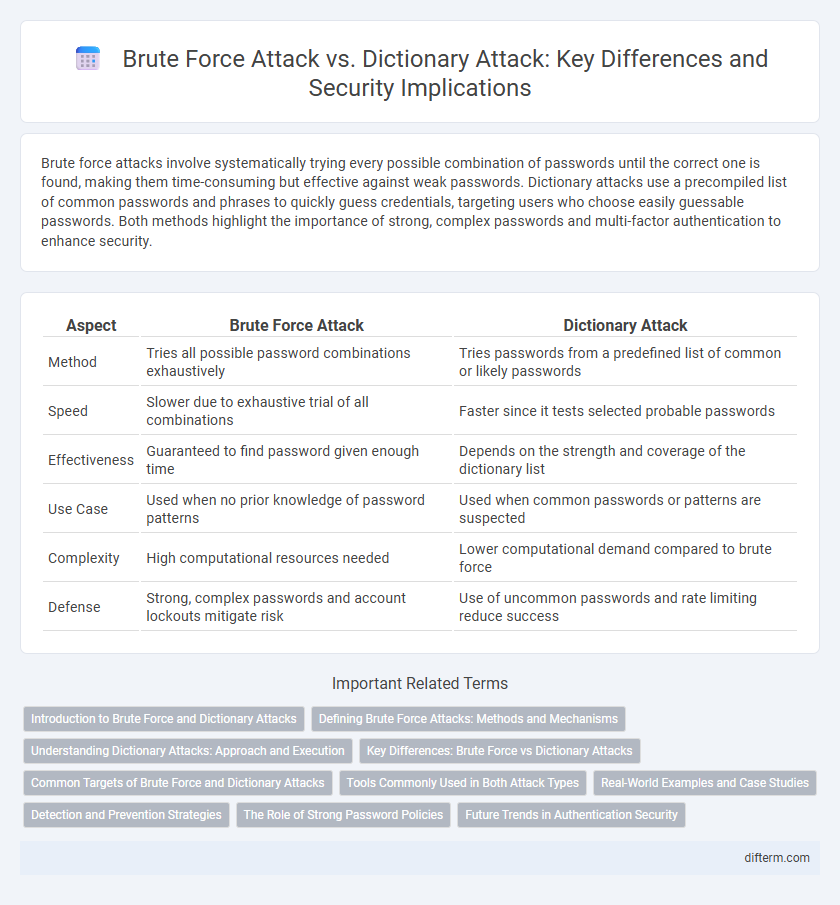
| Aspect | Brute Force Attack | Dictionary Attack |
|---|---|---|
| Method | Tries all possible password combinations exhaustively | Tries passwords from a predefined list of common or likely passwords |
| Speed | Slower due to exhaustive trial of all combinations | Faster since it tests selected probable passwords |
| Effectiveness | Guaranteed to find password given enough time | Depends on the strength and coverage of the dictionary list |
| Use Case | Used when no prior knowledge of password patterns | Used when common passwords or patterns are suspected |
| Complexity | High computational resources needed | Lower computational demand compared to brute force |
| Defense | Strong, complex passwords and account lockouts mitigate risk | Use of uncommon passwords and rate limiting reduce success |
Introduction to Brute Force and Dictionary Attacks
Brute force attacks involve systematically trying every possible combination of passwords or encryption keys until the correct one is found, making them exhaustive and time-consuming but highly effective against weak credentials. Dictionary attacks use a predefined list of probable passwords or phrases, significantly speeding up the breach process by focusing on commonly used or leaked passwords instead of random guesses. Both attack types exploit weak password policies and inadequate account lockout mechanisms, emphasizing the need for strong, complex passwords and multi-factor authentication in security protocols.
Defining Brute Force Attacks: Methods and Mechanisms
Brute force attacks involve systematically attempting all possible password combinations using automated software until the correct one is found, relying on computational power and time. These attacks utilize algorithms that generate every possible key sequence, including letters, numbers, and symbols, making them exhaustive but time-consuming. Common methods include simple brute force with no shortcuts and more advanced techniques like hybrid attacks that integrate dictionary words with additional characters to increase efficiency.
Understanding Dictionary Attacks: Approach and Execution
Dictionary attacks exploit precompiled lists of common passwords and phrases to systematically attempt access, leveraging the predictability of human password choices. These attacks execute by matching entries against user credentials, significantly reducing the time needed compared to random brute force attempts. Effective defenses include implementing account lockout policies, using multifactor authentication, and enforcing strong, unique password creation.
Key Differences: Brute Force vs Dictionary Attacks
Brute force attacks systematically try every possible combination of characters until the correct password is found, making them time-consuming but guaranteed to eventually succeed given enough time and resources. Dictionary attacks, by contrast, use a precompiled list of common passwords or phrases, exploiting human tendencies to choose predictable credentials and therefore usually succeed faster than pure brute force. The key difference lies in brute force attacking every potential password, while dictionary attacks target likely passwords based on real-world user behavior and commonly used password databases.
Common Targets of Brute Force and Dictionary Attacks
Common targets of brute force and dictionary attacks include user login credentials, such as usernames and passwords, for online accounts, email services, and financial platforms. These attacks also frequently target encrypted files and network devices like routers and VPNs to gain unauthorized access. High-value assets like corporate databases and administrative control panels are prime targets due to their sensitive information and control privileges.
Tools Commonly Used in Both Attack Types
Hydra and Medusa are widely utilized tools in both brute force and dictionary attacks, exploiting automated login attempts to gain unauthorized access. John the Ripper and Cain & Abel excel at password cracking by systematically trying vast numbers of potential passwords sourced from dictionaries or generated through permutations. These tools leverage extensive wordlists and algorithms to optimize attack efficiency against authentication systems.
Real-World Examples and Case Studies
Brute force attacks systematically try every possible password combination, exemplified by the 2012 LinkedIn breach where attackers exploited weak hashing to access millions of accounts. Dictionary attacks use precompiled lists of common passwords, as seen in the 2014 Dropbox hack where attackers gained access by rapidly testing popular passwords and email combinations. Security professionals emphasize the importance of strong, unique passwords and multi-factor authentication to defend against these prevalent attack vectors.
Detection and Prevention Strategies
Brute force attacks can be detected through monitoring multiple failed login attempts from a single IP address, while dictionary attacks often trigger alerts by identifying rapid attempts using common password lists. Prevention strategies include implementing account lockout policies, requiring strong password complexity, and utilizing multi-factor authentication to reduce the risk of unauthorized access. Intrusion detection systems and rate limiting can further mitigate both attack types by identifying and blocking repeated suspicious login behavior.
The Role of Strong Password Policies
Strong password policies significantly mitigate the risk of brute force and dictionary attacks by enforcing complexity, length, and unpredictability in user credentials. Implementing requirements such as a mix of uppercase, lowercase, numbers, and special characters exponentially increases the time and computational resources needed for attackers to crack passwords. Enforcing regular password changes and account lockouts after multiple failed attempts further strengthens defense mechanisms against these automated attack methods.
Future Trends in Authentication Security
Emerging trends in authentication security are leveraging AI-driven anomaly detection and behavioral biometrics to counter brute force and dictionary attacks more effectively. Multi-factor authentication (MFA) combined with adaptive risk assessment is becoming standard to thwart increasingly sophisticated password-guessing techniques. The rise of passwordless authentication methods, such as biometrics and hardware tokens, signals a shift towards reducing reliance on vulnerable credential-based systems.
Brute Force Attack vs Dictionary Attack Infographic
 difterm.com
difterm.com