Privacy by design integrates data protection into the development of security pet systems, ensuring user information remains confidential from the outset. Security by design emphasizes safeguarding the system against threats and vulnerabilities to prevent unauthorized access or breaches. Combining both approaches creates a robust security pet solution that protects user privacy while maintaining strong defense mechanisms.
Table of Comparison
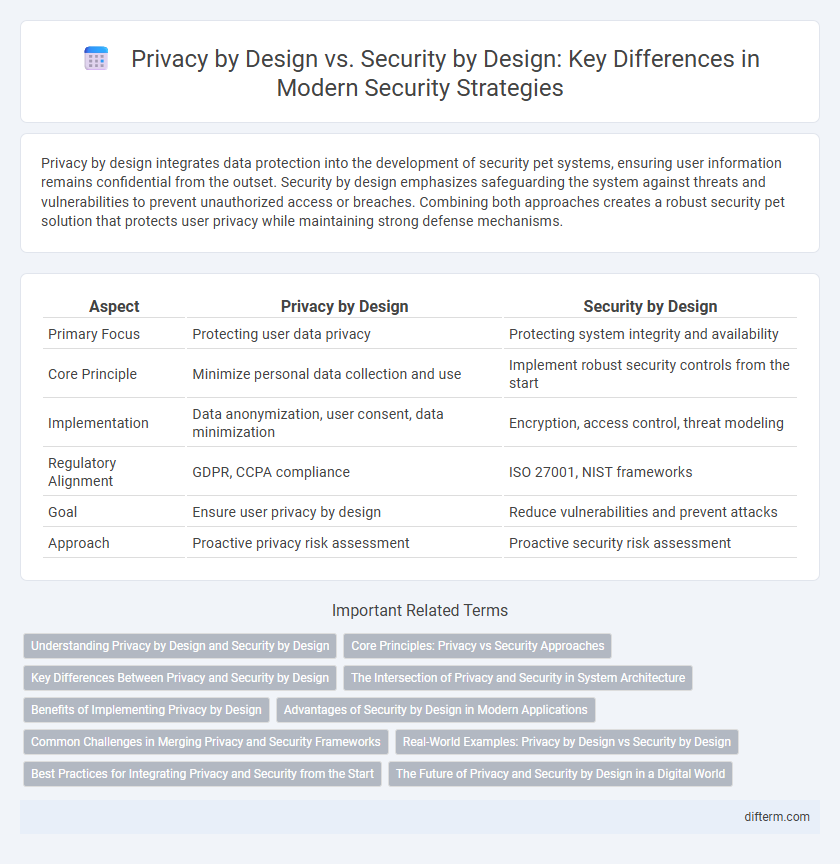
| Aspect | Privacy by Design | Security by Design |
|---|---|---|
| Primary Focus | Protecting user data privacy | Protecting system integrity and availability |
| Core Principle | Minimize personal data collection and use | Implement robust security controls from the start |
| Implementation | Data anonymization, user consent, data minimization | Encryption, access control, threat modeling |
| Regulatory Alignment | GDPR, CCPA compliance | ISO 27001, NIST frameworks |
| Goal | Ensure user privacy by design | Reduce vulnerabilities and prevent attacks |
| Approach | Proactive privacy risk assessment | Proactive security risk assessment |
Understanding Privacy by Design and Security by Design
Privacy by Design integrates proactive data protection measures into system architecture, ensuring personal information is secured from the outset. Security by Design focuses on embedding robust defense mechanisms throughout the development lifecycle to safeguard against cyber threats and unauthorized access. Both concepts emphasize anticipatory risk management, but Privacy by Design specifically targets data confidentiality and user consent, while Security by Design addresses overall system resilience and threat mitigation.
Core Principles: Privacy vs Security Approaches
Privacy by design emphasizes proactive data minimization, user consent, and transparency as core principles to protect personal information from the outset. Security by design centers on implementing robust technical controls such as encryption, authentication, and access management to safeguard systems against threats and vulnerabilities. Both approaches integrate risk assessment, but privacy prioritizes individual rights while security focuses on system integrity and confidentiality.
Key Differences Between Privacy and Security by Design
Privacy by Design emphasizes embedding data protection principles directly into systems and processes to safeguard personal information from the outset. Security by Design focuses on integrating robust security measures and protocols to prevent unauthorized access, breaches, and cyber threats throughout the system lifecycle. Key differences lie in Privacy by Design prioritizing individual data privacy rights, while Security by Design concentrates on maintaining overall system integrity and confidentiality.
The Intersection of Privacy and Security in System Architecture
Privacy by design integrates data protection principles directly into system architecture to ensure user information remains confidential and minimally collected. Security by design emphasizes robust defense mechanisms to safeguard systems against unauthorized access and cyber threats from the outset. The intersection of privacy and security in system architecture requires a holistic approach that balances data minimization with strong encryption, access controls, and continuous monitoring to protect both user privacy and system integrity.
Benefits of Implementing Privacy by Design
Implementing Privacy by Design ensures data protection measures are integrated into systems from the outset, reducing risks of breaches and enhancing user trust. This proactive approach minimizes compliance costs with regulations like GDPR by embedding privacy controls directly into workflows. Organizations benefit from stronger reputation management and competitive advantage through increased transparency and accountability in data handling.
Advantages of Security by Design in Modern Applications
Security by Design integrates security measures throughout the entire software development lifecycle, reducing vulnerabilities and enhancing system resilience against cyber threats. It enables proactive threat identification and mitigation, leading to fewer breaches and lower remediation costs in modern applications. Emphasizing secure coding practices and automated security testing ensures robust protection without compromising functionality or user experience.
Common Challenges in Merging Privacy and Security Frameworks
Integrating Privacy by Design and Security by Design frameworks often encounters challenges such as conflicting priorities, where privacy aims to minimize data collection while security focuses on data protection and access control. Balancing compliance with evolving regulations like GDPR alongside robust security protocols requires continuous alignment and collaboration between privacy officers and security teams. Addressing these issues demands unified governance models and adaptive risk assessment strategies to ensure both privacy and security objectives are met without compromising either.
Real-World Examples: Privacy by Design vs Security by Design
Privacy by Design integrates user data protection from the outset, exemplified by Apple's implementation of end-to-end encryption in iMessage, ensuring user messages remain confidential. Security by Design prioritizes system resilience against threats, as demonstrated by Google's Titan Security Key, which enhances account protection through hardware-based authentication. Both approaches adopt proactive, embedded strategies but target different aspects of safeguarding information in digital environments.
Best Practices for Integrating Privacy and Security from the Start
Integrating Privacy by Design and Security by Design from the start ensures comprehensive protection of personal data and system integrity through proactive risk assessment and threat modeling. Best practices include embedding data minimization, encryption, and access controls directly into the architecture alongside continuous monitoring and compliance checks aligned with GDPR and ISO/IEC 27001 standards. Early collaboration between privacy officers and security teams fosters a unified framework that reduces vulnerabilities and enhances trust in digital products and services.
The Future of Privacy and Security by Design in a Digital World
Privacy by design embeds data protection principles into the development process, ensuring user confidentiality and compliance with regulations like GDPR. Security by design focuses on creating robust systems that prevent unauthorized access and cyber threats through continuous vulnerability assessments and threat modeling. Future digital innovations will require integrating both approaches to build resilient architectures protecting sensitive information and maintaining user trust in an increasingly interconnected environment.
Privacy by design vs security by design Infographic
 difterm.com
difterm.com