Passive reconnaissance involves gathering information about a target without direct interaction, minimizing the risk of detection by using publicly available sources like social media, websites, and DNS records. Active reconnaissance includes directly engaging with the target network or systems through techniques such as port scanning or vulnerability probing, increasing the likelihood of discovery but providing more detailed and accurate data. Understanding the trade-offs between these methods is crucial for developing effective security strategies and response plans.
Table of Comparison
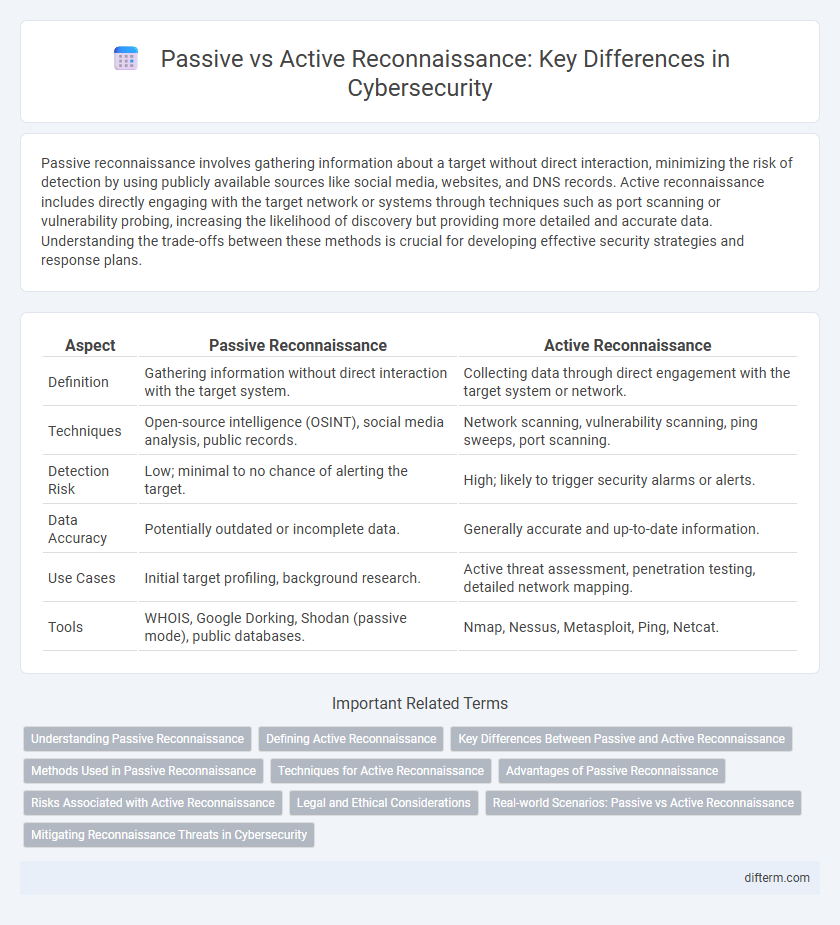
| Aspect | Passive Reconnaissance | Active Reconnaissance |
|---|---|---|
| Definition | Gathering information without direct interaction with the target system. | Collecting data through direct engagement with the target system or network. |
| Techniques | Open-source intelligence (OSINT), social media analysis, public records. | Network scanning, vulnerability scanning, ping sweeps, port scanning. |
| Detection Risk | Low; minimal to no chance of alerting the target. | High; likely to trigger security alarms or alerts. |
| Data Accuracy | Potentially outdated or incomplete data. | Generally accurate and up-to-date information. |
| Use Cases | Initial target profiling, background research. | Active threat assessment, penetration testing, detailed network mapping. |
| Tools | WHOIS, Google Dorking, Shodan (passive mode), public databases. | Nmap, Nessus, Metasploit, Ping, Netcat. |
Understanding Passive Reconnaissance
Passive reconnaissance involves gathering information about a target without direct interaction, using publicly available data such as social media profiles, domain registration records, and network footprints. This method minimizes the risk of detection since it does not trigger alerts or security defenses on the target systems. Understanding passive reconnaissance is crucial for identifying potential security vulnerabilities early and fortifying defenses before an active attack occurs.
Defining Active Reconnaissance
Active reconnaissance involves direct interaction with the target system to gather information, often by sending probes, scanning ports, and exploiting vulnerabilities. This method provides detailed and real-time data but increases the risk of detection by intrusion detection systems (IDS). Security professionals use active reconnaissance to identify attack vectors and assess system defenses, balancing thoroughness with operational stealth.
Key Differences Between Passive and Active Reconnaissance
Passive reconnaissance involves gathering information without direct interaction with the target system, relying on publicly available data such as social media, domain names, and network footprints. Active reconnaissance entails direct probing and scanning of the target's network or systems to identify vulnerabilities, using tools like port scanners and vulnerability assessors. The key difference lies in risk and detectability: passive methods minimize exposure and detection risk, whereas active methods increase the likelihood of alerting security defenses due to the direct engagement with the target.
Methods Used in Passive Reconnaissance
Passive reconnaissance methods primarily involve gathering information without directly interacting with the target system, utilizing techniques such as open-source intelligence (OSINT), social media analysis, domain name system (DNS) queries, and publicly available network metadata. Tools like search engines, WHOIS databases, and network scanners that operate without sending packets to the target help in mapping the attack surface discreetly. This approach minimizes detection risk and provides valuable data on IP addresses, server configurations, employee details, and infrastructure before launching any active probing.
Techniques for Active Reconnaissance
Active reconnaissance techniques include network scanning, vulnerability scanning, and direct interaction with target systems to gather detailed information such as open ports, running services, and system configurations. Tools like Nmap, Nessus, and Metasploit are commonly employed to perform comprehensive active reconnaissance by probing targets and identifying exploitable weaknesses. These techniques increase the risk of detection compared to passive reconnaissance but provide more precise and actionable data for penetration testing and security assessments.
Advantages of Passive Reconnaissance
Passive reconnaissance offers the advantage of remaining undetected by target systems, as it gathers information without directly interacting with them, minimizing the risk of triggering security alerts. This method leverages open-source intelligence (OSINT), such as public websites, social media, and domain registration data, enabling comprehensive data collection without leaving digital footprints. Security professionals use passive reconnaissance to conduct stealthy assessments, enhancing vulnerability analysis while preserving operational security.
Risks Associated with Active Reconnaissance
Active reconnaissance involves direct interaction with the target system, increasing the risk of detection by security monitoring tools such as intrusion detection systems (IDS) and firewalls. This method exposes the attacker to potential legal consequences due to unauthorized access attempts and can trigger defensive responses including IP blocking or tracing. In contrast, passive reconnaissance gathers information without direct contact, minimizing risk but limiting data depth.
Legal and Ethical Considerations
Passive reconnaissance involves gathering information without directly interacting with the target, minimizing legal risks by avoiding unauthorized access or data breaches. Active reconnaissance, which entails direct engagement such as scanning or probing, carries higher legal and ethical concerns, including potential violations of privacy laws and unauthorized network access. Ethical security professionals ensure compliance with regulations like GDPR and obtain explicit permission before conducting active reconnaissance to mitigate legal repercussions.
Real-world Scenarios: Passive vs Active Reconnaissance
Passive reconnaissance involves gathering information about a target without direct interaction, such as monitoring public websites, social media profiles, and DNS records, minimizing the risk of detection. Active reconnaissance requires direct engagement with the target system through techniques like port scanning, network mapping, and vulnerability scanning, increasing the chance of triggering security defenses or alerts. In real-world scenarios, passive reconnaissance is ideal for stealthy intelligence collection during the initial research phase, while active reconnaissance is essential for detailed system analysis and exploitation planning.
Mitigating Reconnaissance Threats in Cybersecurity
Mitigating reconnaissance threats in cybersecurity involves implementing robust network monitoring tools to detect and block active reconnaissance attempts while employing strict access controls and anonymization techniques to minimize data exposure during passive reconnaissance. Organizations should deploy intrusion detection systems (IDS) and regularly update firewall rules to prevent unauthorized scanning and probing activities. Continuous threat intelligence gathering enhances visibility into attacker methodologies, enabling proactive defense against reconnaissance-driven exploits.
Passive Reconnaissance vs Active Reconnaissance Infographic
 difterm.com
difterm.com