Malware is a broad category of malicious software designed to harm, exploit, or steal information from devices, while ransomware is a specific type of malware that encrypts files and demands payment for their release. Understanding the distinction is crucial for effective cybersecurity measures and timely responses to attacks. Implementing robust antivirus solutions and regular data backups can significantly reduce the impact of both malware and ransomware threats.
Table of Comparison
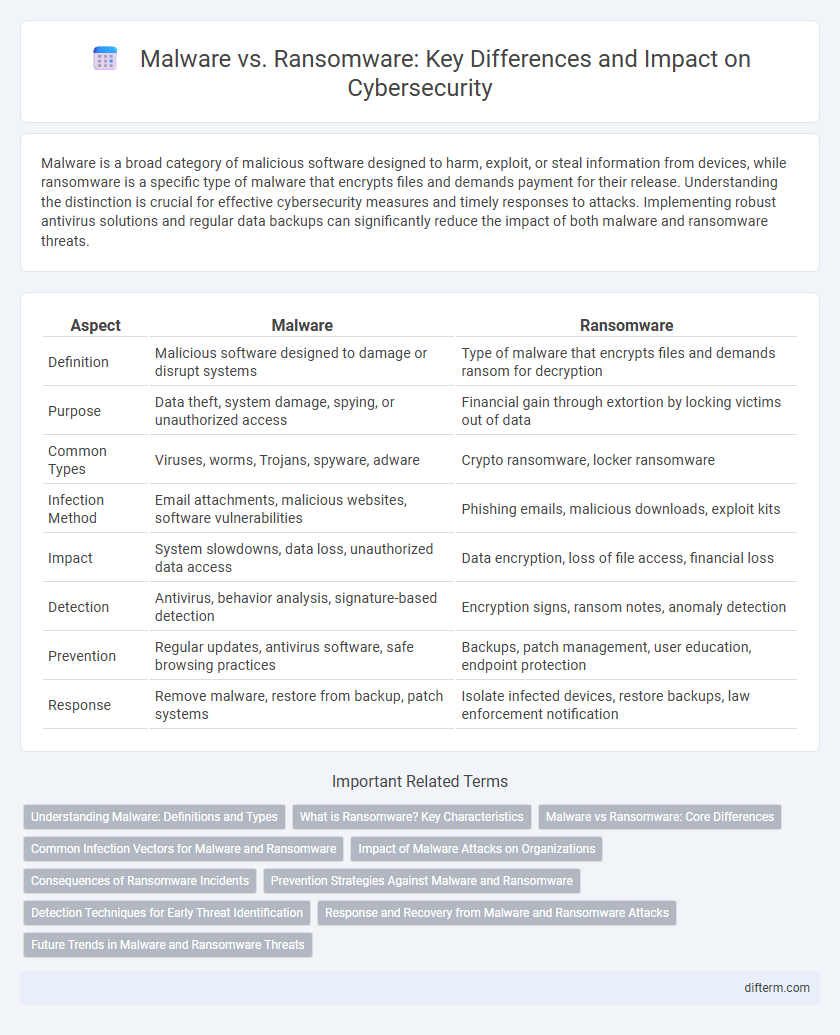
| Aspect | Malware | Ransomware |
|---|---|---|
| Definition | Malicious software designed to damage or disrupt systems | Type of malware that encrypts files and demands ransom for decryption |
| Purpose | Data theft, system damage, spying, or unauthorized access | Financial gain through extortion by locking victims out of data |
| Common Types | Viruses, worms, Trojans, spyware, adware | Crypto ransomware, locker ransomware |
| Infection Method | Email attachments, malicious websites, software vulnerabilities | Phishing emails, malicious downloads, exploit kits |
| Impact | System slowdowns, data loss, unauthorized data access | Data encryption, loss of file access, financial loss |
| Detection | Antivirus, behavior analysis, signature-based detection | Encryption signs, ransom notes, anomaly detection |
| Prevention | Regular updates, antivirus software, safe browsing practices | Backups, patch management, user education, endpoint protection |
| Response | Remove malware, restore from backup, patch systems | Isolate infected devices, restore backups, law enforcement notification |
Understanding Malware: Definitions and Types
Malware encompasses a broad category of malicious software designed to infiltrate, damage, or disable computer systems, including viruses, worms, Trojans, spyware, adware, and ransomware. Each type of malware operates differently; viruses replicate by attaching to clean files, worms spread independently across networks, and Trojans disguise themselves as legitimate applications to deceive users. Recognizing these distinctions is crucial for developing targeted cybersecurity strategies and effective threat mitigation.
What is Ransomware? Key Characteristics
Ransomware is a type of malicious software designed to encrypt a victim's files or lock them out of their system, demanding payment to restore access. Key characteristics include encryption of critical data, a ransom note with payment instructions, and the use of cryptocurrencies for anonymous transactions. Unlike general malware, ransomware specifically targets data hostage situations to extort money from individuals or organizations.
Malware vs Ransomware: Core Differences
Malware is a broad category of malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, encompassing viruses, worms, trojans, spyware, and ransomware. Ransomware is a specific type of malware that encrypts victims' data or locks systems, demanding a ransom payment to restore access, targeting financial gain through extortion. Understanding these core differences is essential for designing targeted cybersecurity defenses and incident response strategies against evolving threats.
Common Infection Vectors for Malware and Ransomware
Malware and ransomware frequently infiltrate systems through phishing emails, malicious attachments, and compromised websites exploiting browser vulnerabilities. Network vulnerabilities such as unpatched software, unsecured remote desktop protocols (RDP), and weak passwords often serve as gateways for ransomware attacks. Drive-by downloads and infected software updates remain critical infection vectors across both malware and ransomware campaigns.
Impact of Malware Attacks on Organizations
Malware attacks compromise sensitive data, disrupt business operations, and lead to significant financial losses for organizations. Ransomware, a type of malware, specifically encrypts critical files, demanding ransom payments to restore access and causing severe downtime and reputational damage. Effective cybersecurity measures and employee training are essential to mitigate these risks and protect organizational assets.
Consequences of Ransomware Incidents
Ransomware incidents often result in severe operational disruptions, data loss, and significant financial costs due to ransom payments and recovery expenses. Unlike general malware, ransomware encrypts critical files, making business continuity impossible until the ransom is paid or systems are restored from backups. The consequences also include reputational damage and potential legal liabilities, especially when sensitive customer data is compromised.
Prevention Strategies Against Malware and Ransomware
Effective prevention strategies against malware and ransomware include using advanced endpoint protection tools that detect and block malicious activity in real-time. Regularly updating software and operating systems closes vulnerabilities exploited by cybercriminals, while employee training on phishing and suspicious links reduces infection risks. Implementing robust backup solutions ensures data recovery without paying ransoms in case of ransomware attacks.
Detection Techniques for Early Threat Identification
Malware detection relies on signature-based methods and heuristic analysis to identify malicious code patterns and unusual behavior within system files. Ransomware detection employs behavioral monitoring and anomaly detection algorithms that track encryption activities and unauthorized file modifications to flag potential threats early. Advanced machine learning models enhance early threat identification by analyzing vast data sets to detect subtle signs of malware and ransomware attacks before system compromise.
Response and Recovery from Malware and Ransomware Attacks
Effective response to malware attacks involves isolating affected systems and deploying up-to-date antivirus tools to remove threats while preserving data integrity. Ransomware recovery requires secure backups for rapid restoration without yielding to attacker demands, alongside comprehensive incident response plans to minimize downtime. Both scenarios benefit from continuous monitoring and post-attack analysis to strengthen defenses against future breaches.
Future Trends in Malware and Ransomware Threats
Emerging malware and ransomware threats are increasingly leveraging artificial intelligence and machine learning to enhance their evasion capabilities and automate attacks. The proliferation of Internet of Things (IoT) devices expands the attack surface, enabling more sophisticated and large-scale ransomware campaigns targeting critical infrastructure. Future trends indicate a rise in fileless malware and ransomware-as-a-service models, driving widespread adoption by cybercriminals with minimal technical expertise.
Malware vs Ransomware Infographic
 difterm.com
difterm.com