Threat intelligence involves collecting and analyzing data about potential cyber threats to anticipate and prevent attacks, while threat hunting is a proactive approach that searches within networks to detect hidden threats that have bypassed traditional security measures. Threat intelligence provides the contextual knowledge and indicators of compromise, enabling threat hunters to focus their efforts on investigating suspicious activities more efficiently. Combining both strategies enhances an organization's ability to identify, respond to, and mitigate advanced security threats effectively.
Table of Comparison
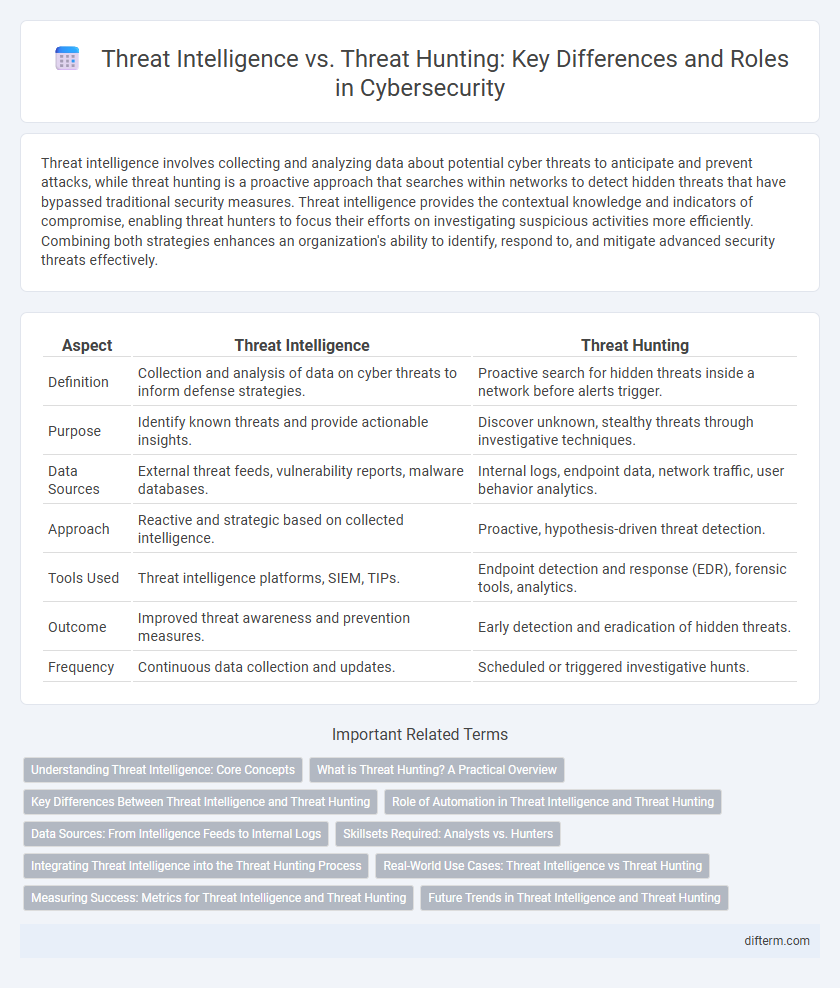
| Aspect | Threat Intelligence | Threat Hunting |
|---|---|---|
| Definition | Collection and analysis of data on cyber threats to inform defense strategies. | Proactive search for hidden threats inside a network before alerts trigger. |
| Purpose | Identify known threats and provide actionable insights. | Discover unknown, stealthy threats through investigative techniques. |
| Data Sources | External threat feeds, vulnerability reports, malware databases. | Internal logs, endpoint data, network traffic, user behavior analytics. |
| Approach | Reactive and strategic based on collected intelligence. | Proactive, hypothesis-driven threat detection. |
| Tools Used | Threat intelligence platforms, SIEM, TIPs. | Endpoint detection and response (EDR), forensic tools, analytics. |
| Outcome | Improved threat awareness and prevention measures. | Early detection and eradication of hidden threats. |
| Frequency | Continuous data collection and updates. | Scheduled or triggered investigative hunts. |
Understanding Threat Intelligence: Core Concepts
Threat intelligence involves the systematic collection, analysis, and dissemination of information about potential cyber threats to enhance an organization's defensive measures. Core concepts include indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) used by adversaries, and the context surrounding threat actors' motives and capabilities. Understanding these elements enables security teams to anticipate attacks, prioritize risks, and improve incident response strategies effectively.
What is Threat Hunting? A Practical Overview
Threat hunting is a proactive cybersecurity practice that involves actively searching for hidden threats and adversaries within a network before alerts are triggered. It utilizes advanced analytics, behavioral analysis, and threat intelligence to uncover sophisticated attacks that evade automated security tools. By continuously scrutinizing network activity and endpoints, threat hunting enhances an organization's ability to detect and respond to elusive cyber threats effectively.
Key Differences Between Threat Intelligence and Threat Hunting
Threat intelligence involves the systematic collection and analysis of data on cyber threats to provide actionable insights for proactive defense, while threat hunting is the active, iterative process of searching for hidden threats within an organization's environment. Key differences include that threat intelligence is largely external and strategic, focusing on known threats and indicators of compromise (IOCs), whereas threat hunting is internal and tactical, aiming to uncover unknown or emerging threats through hypothesis-driven investigation. Threat intelligence supports threat hunting by supplying relevant context and data, enabling hunters to prioritize and refine their search efforts effectively.
Role of Automation in Threat Intelligence and Threat Hunting
Automation in threat intelligence enables rapid data aggregation and analysis from diverse sources, accelerating the identification of emerging threats. In threat hunting, automation assists by prioritizing alerts and correlating behavioral patterns, enhancing manual investigation efficiency. Combined, automated tools empower security teams to proactively detect and respond to sophisticated cyber threats with greater accuracy and speed.
Data Sources: From Intelligence Feeds to Internal Logs
Threat intelligence relies heavily on external intelligence feeds such as open-source data, vendor alerts, and government advisories to provide a broad view of emerging threats and attack patterns. Threat hunting depends primarily on internal data sources, including system logs, network traffic, endpoint telemetry, and user behavior analytics, enabling proactive detection of anomalous activities within the organizational environment. Integrating both external threat intelligence and internal log data enriches threat hunting accuracy and enhances overall security posture evaluation.
Skillsets Required: Analysts vs. Hunters
Threat intelligence analysts require strong analytical skills, proficiency in data collection, and expertise in understanding cyber threats, tactics, techniques, and procedures (TTPs). Threat hunters need advanced skills in behavioral analysis, malware reverse engineering, and deep knowledge of system architectures to proactively identify hidden threats. Both roles demand continuous learning and the ability to interpret complex security data, but hunters often require more hands-on technical expertise for real-time investigations.
Integrating Threat Intelligence into the Threat Hunting Process
Integrating threat intelligence into the threat hunting process enhances the accuracy and efficiency of identifying advanced cyber threats by leveraging real-time data on indicators of compromise (IOCs), attacker tactics, techniques, and procedures (TTPs). Combining external threat intelligence feeds with internal telemetry allows security teams to proactively uncover hidden threats and respond faster to potential breaches. This synergy between threat intelligence and hunting reduces dwell time and strengthens an organization's overall cybersecurity posture.
Real-World Use Cases: Threat Intelligence vs Threat Hunting
Threat intelligence provides actionable insights by analyzing global data on cyber threats, enabling organizations to prioritize vulnerabilities and anticipate attacks based on current threat actor tactics, techniques, and procedures (TTPs). Threat hunting involves proactively searching within networks to identify undetected threats, often using hypotheses derived from threat intelligence to uncover hidden adversaries and anomalous behaviors. Combining threat intelligence with threat hunting enhances detection accuracy and response times in real-world scenarios, such as identifying advanced persistent threats (APTs) and insider threats before they cause significant damage.
Measuring Success: Metrics for Threat Intelligence and Threat Hunting
Measuring success in threat intelligence hinges on metrics like accuracy of threat detection, timeliness of alerts, and reduction in false positives, providing actionable insights for proactive defense. Threat hunting effectiveness is evaluated through metrics such as dwell time reduction, number of threats uncovered, and response time improvement, emphasizing active investigation and mitigation. Combining quantitative data like incident response rates with qualitative assessments of threat actor behavior enriches overall cybersecurity resilience.
Future Trends in Threat Intelligence and Threat Hunting
Emerging trends in threat intelligence emphasize predictive analytics and artificial intelligence to proactively identify evolving cyber threats before exploitation occurs. Threat hunting increasingly integrates automated machine learning models to detect subtle anomalies and insider threats that traditional methods often overlook. Both disciplines are converging toward real-time data sharing and collaborative platforms, enhancing rapid response capabilities in complex, multi-vector cyberattack environments.
Threat intelligence vs threat hunting Infographic
 difterm.com
difterm.com