Hashing transforms data into a fixed-size string of characters, ensuring password confidentiality by converting the original password into an irreversible format. Salting enhances security by adding a unique random value to each password before hashing, preventing attackers from using precomputed hash tables or rainbow tables. Combining salting with hashing creates a robust defense against common password attacks, significantly reducing the risk of credential compromise.
Table of Comparison
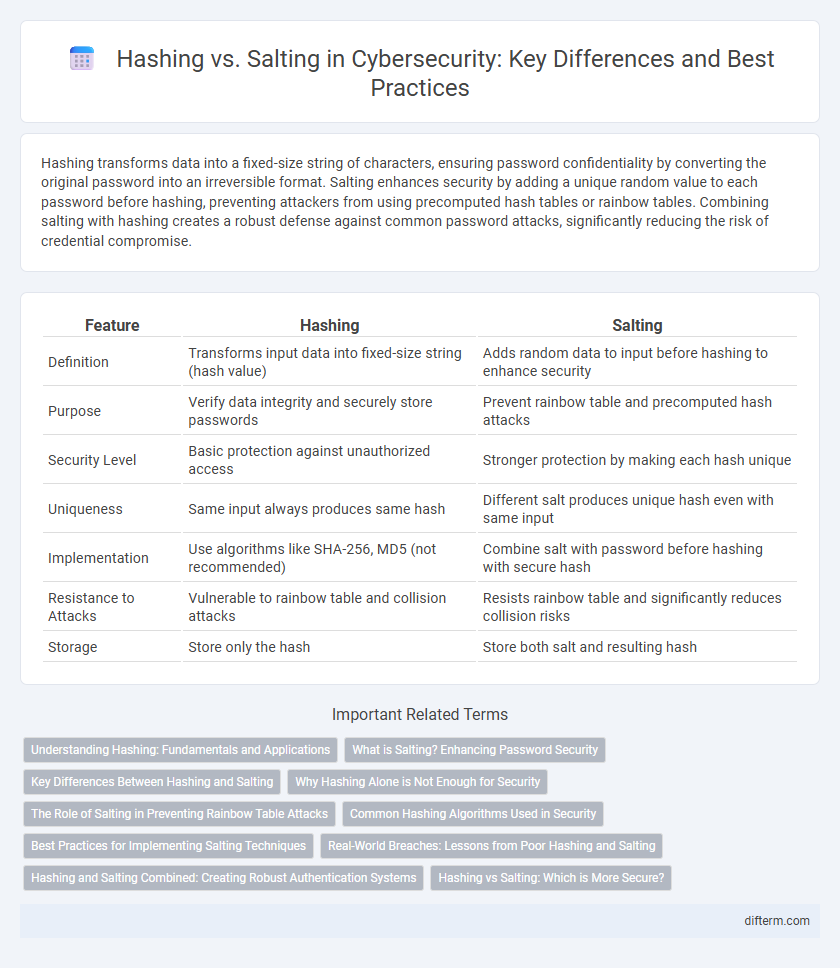
| Feature | Hashing | Salting |
|---|---|---|
| Definition | Transforms input data into fixed-size string (hash value) | Adds random data to input before hashing to enhance security |
| Purpose | Verify data integrity and securely store passwords | Prevent rainbow table and precomputed hash attacks |
| Security Level | Basic protection against unauthorized access | Stronger protection by making each hash unique |
| Uniqueness | Same input always produces same hash | Different salt produces unique hash even with same input |
| Implementation | Use algorithms like SHA-256, MD5 (not recommended) | Combine salt with password before hashing with secure hash |
| Resistance to Attacks | Vulnerable to rainbow table and collision attacks | Resists rainbow table and significantly reduces collision risks |
| Storage | Store only the hash | Store both salt and resulting hash |
Understanding Hashing: Fundamentals and Applications
Hashing transforms data into fixed-size, unique strings called hash values, ensuring data integrity and secure storage of sensitive information. Cryptographic hash functions like SHA-256 and MD5 are widely used to protect passwords, verify messages, and maintain data authenticity by producing irreversible outputs. Proper implementation of hashing prevents unauthorized data access and is foundational in cybersecurity, digital signatures, and blockchain technology.
What is Salting? Enhancing Password Security
Salting is a security technique that involves adding a unique random value to each password before hashing to enhance protection against attacks. By incorporating salts, it prevents attackers from using precomputed tables like rainbow tables to reverse hashed passwords. This ensures that even identical passwords result in different hash outputs, significantly strengthening password security.
Key Differences Between Hashing and Salting
Hashing transforms input data into a fixed-length string, serving as a one-way function to ensure data integrity, while salting appends a unique random value to the input before hashing to enhance security against rainbow table attacks. Hashing alone can be vulnerable to precomputed hash attacks, whereas salting combats this by making identical inputs produce different hash outputs. Salting requires storing the salt value securely alongside the hash to verify data, amplifying password protection beyond basic hashing.
Why Hashing Alone is Not Enough for Security
Hashing alone is not enough for security because it produces deterministic outputs, making systems vulnerable to rainbow table attacks and hash collisions. Without salting, attackers can easily use precomputed hash databases to reverse-engineer passwords or sensitive data. Incorporating unique salts ensures that identical inputs yield distinct hashes, significantly enhancing resistance against brute-force and dictionary attacks.
The Role of Salting in Preventing Rainbow Table Attacks
Salting enhances password security by adding a unique, random value to each password before hashing, making rainbow table attacks ineffective because precomputed hash tables cannot match salted hashes. This technique ensures that identical passwords result in different hashes, significantly increasing the difficulty of offline password cracking attempts. Salting is a critical defense in modern authentication systems, protecting user credentials against large-scale hash reversal attacks.
Common Hashing Algorithms Used in Security
Common hashing algorithms used in security include SHA-256, SHA-3, and bcrypt, each providing varying levels of cryptographic strength and resistance to collision attacks. SHA-256, a member of the SHA-2 family, is widely used for data integrity verification and digital signatures due to its balance of speed and security. Bcrypt, designed specifically for password hashing, incorporates salting and adaptive work factors to defend against brute-force attacks and rainbow table exploits effectively.
Best Practices for Implementing Salting Techniques
Implementing salting techniques involves generating a unique, cryptographically secure random salt for each password before hashing to prevent rainbow table attacks. Salts should be stored alongside the hashed passwords in the database to allow proper verification during authentication processes. Employing algorithms like bcrypt, scrypt, or Argon2 combines salting with key stretching, enhancing security against brute-force and dictionary attacks.
Real-World Breaches: Lessons from Poor Hashing and Salting
Real-world breaches often expose inadequate hashing and salting practices, such as using unsalted hashes or deprecated algorithms like MD5, leading to rapid password cracking by attackers. Effective salting introduces unique random data to each password hash, significantly increasing resistance against rainbow table attacks and enhancing overall security. Organizations that neglect proper salting and rely solely on hashing face severe data compromises, emphasizing the critical need for modern standards like bcrypt or Argon2 in protecting sensitive credentials.
Hashing and Salting Combined: Creating Robust Authentication Systems
Hashing and salting combined create robust authentication systems by transforming passwords into fixed-length, non-reversible strings while adding unique random data (salt) to each input, preventing attackers from using precomputed hash tables such as rainbow tables. This method significantly enhances security by ensuring that even identical passwords generate distinct hash outputs, thwarting collision attacks and improving resistance against brute force attempts. Salting and hashing together protect sensitive information and maintain the integrity of authentication processes in modern cybersecurity frameworks.
Hashing vs Salting: Which is More Secure?
Hashing transforms data into a fixed-length irreversible string, ensuring data integrity and secure password storage, but it is vulnerable to rainbow table attacks without added protection. Salting enhances security by appending a unique random value to each password before hashing, effectively preventing precomputed hash attacks and ensuring that identical passwords produce distinct hashes. Salting combined with hashing is significantly more secure than hashing alone, as it mitigates risks of hash collisions and offline cracking.
Hashing vs Salting Infographic
 difterm.com
difterm.com