A Bastion Host serves as a secure gateway for accessing internal networks, typically hardened and monitored to prevent unauthorized access. A Jump Box is a specialized server used to connect to other machines within a private network, often acting as a controlled access point for administrators. Both enhance security by restricting direct access to sensitive systems, but Bastion Hosts emphasize hardened perimeter defense while Jump Boxes focus on controlled internal access.
Table of Comparison
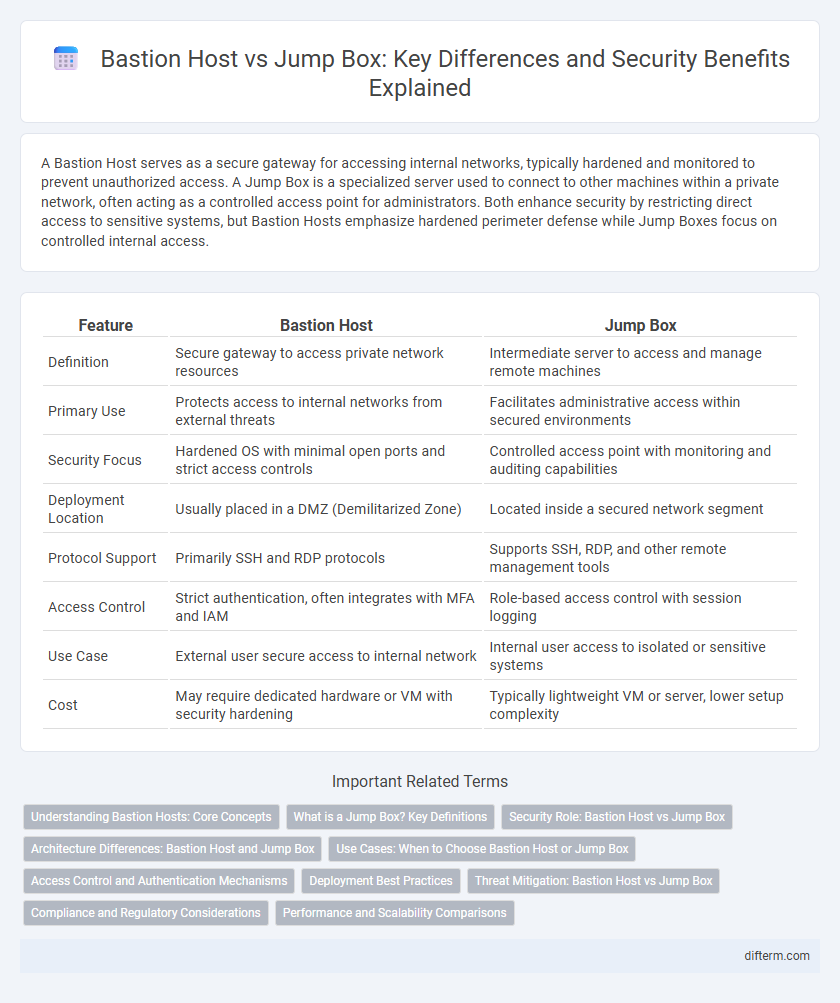
| Feature | Bastion Host | Jump Box |
|---|---|---|
| Definition | Secure gateway to access private network resources | Intermediate server to access and manage remote machines |
| Primary Use | Protects access to internal networks from external threats | Facilitates administrative access within secured environments |
| Security Focus | Hardened OS with minimal open ports and strict access controls | Controlled access point with monitoring and auditing capabilities |
| Deployment Location | Usually placed in a DMZ (Demilitarized Zone) | Located inside a secured network segment |
| Protocol Support | Primarily SSH and RDP protocols | Supports SSH, RDP, and other remote management tools |
| Access Control | Strict authentication, often integrates with MFA and IAM | Role-based access control with session logging |
| Use Case | External user secure access to internal network | Internal user access to isolated or sensitive systems |
| Cost | May require dedicated hardware or VM with security hardening | Typically lightweight VM or server, lower setup complexity |
Understanding Bastion Hosts: Core Concepts
Bastion hosts serve as fortified gateways designed to securely manage access to private networks, minimizing attack surfaces by restricting entry points. They are typically hardened servers with strict security policies, often deployed in a demilitarized zone (DMZ) to control and monitor inbound connections to internal systems. Understanding the role of bastion hosts is crucial for implementing layered security architectures that protect critical infrastructure from unauthorized access.
What is a Jump Box? Key Definitions
A Jump Box is a secure, hardened server used to access and manage devices within a protected network, serving as a controlled gateway for administrative tasks. It restricts direct access to sensitive environments by enabling audited and monitored connections through a single entry point, reducing the attack surface. This setup enhances security by isolating management sessions from the production network, ensuring controlled and traceable access to critical infrastructure.
Security Role: Bastion Host vs Jump Box
A Bastion Host serves as a hardened gateway specifically designed to withstand attacks and securely manage access to private networks, often featuring strict monitoring and limited open ports. A Jump Box functions primarily as a controlled intermediate server allowing administrators to access devices in a restricted environment, emphasizing auditability and session control. Both enhance security by isolating access points, but Bastion Hosts prioritize defense mechanisms while Jump Boxes focus on secure, manageable access.
Architecture Differences: Bastion Host and Jump Box
A Bastion Host is a hardened, specially secured server designed to withstand direct attacks, acting as a controlled gateway for accessing internal networks, typically placed in a demilitarized zone (DMZ). In contrast, a Jump Box operates as an intermediary server that provides administrative access to internal resources but may not be as rigorously fortified as a Bastion Host. The architectural distinction lies in the Bastion Host's role in network perimeter defense, while Jump Boxes primarily serve as access points within trusted segments, emphasizing different security postures and deployment strategies.
Use Cases: When to Choose Bastion Host or Jump Box
Bastion Hosts are ideal for providing secure, auditable access to critical systems in cloud environments, acting as a hardened gateway that limits exposure to external threats. Jump Boxes excel when internal network segmentation requires controlled access points for administrators to manage multiple resources through a single entry node. Choosing between the two depends on the specific security architecture, where Bastion Hosts suit public-facing scenarios and Jump Boxes fit well within private network segments demanding granular access control.
Access Control and Authentication Mechanisms
Bastion Hosts and Jump Boxes serve as critical gateways for secure access to private networks, but Bastion Hosts often incorporate stricter access control policies and enhanced multi-factor authentication systems to minimize attack surfaces. Jump Boxes typically provide a hardened environment for administrators and leverage role-based access control (RBAC) alongside centralized authentication protocols like LDAP or Active Directory. Both mechanisms ensure audit logging and session recording, but Bastion Hosts prioritize defense-in-depth strategies for robust identity verification and dynamic access management.
Deployment Best Practices
Deploy Bastion Hosts in isolated network zones with strict access controls to minimize attack surfaces and ensure secure administrative access to critical systems. Jump Boxes should be configured with multi-factor authentication and robust logging mechanisms to track user activity and prevent unauthorized access. Regularly update and patch both Bastion Hosts and Jump Boxes to mitigate vulnerabilities and align with security compliance standards.
Threat Mitigation: Bastion Host vs Jump Box
Bastion Hosts and Jump Boxes serve as critical access control points in network security, reducing attack surfaces by isolating management access to sensitive environments. Bastion Hosts are hardened servers designed with minimal services to withstand potential threats, offering robust protection through strict firewall rules and continuous monitoring. Jump Boxes, often used as intermediary devices, provide secure, logged access but may require additional configuration and hardening to achieve the same level of threat mitigation as Bastion Hosts.
Compliance and Regulatory Considerations
Bastion Hosts and Jump Boxes play critical roles in securing access to sensitive environments while ensuring compliance with regulations such as HIPAA, PCI-DSS, and GDPR. Bastion Hosts are heavily monitored and hardened gateways designed to provide controlled access, generating comprehensive audit logs required for regulatory audits. Jump Boxes offer similar functionality but may vary in compliance readiness depending on their configuration, making it essential to implement strict access controls, encryption, and monitoring to meet regulatory standards.
Performance and Scalability Comparisons
Bastion hosts are optimized for secure access with minimal overhead, providing reliable performance for managing a limited number of connections but may face scalability challenges as the number of users increases. Jump boxes offer enhanced scalability by supporting multiple simultaneous sessions and integrating with automation tools, making them suitable for dynamic, large-scale environments. Performance-wise, jump boxes can distribute workloads more efficiently, reducing latency and improving user experience under heavy access demands.
Bastion Host vs Jump Box Infographic
 difterm.com
difterm.com