VPNs provide encrypted tunnels to secure remote access but often trust users once inside the network, increasing vulnerability to insider threats. Zero Trust Network Access (ZTNA) enforces strict identity verification and continuous authentication for every access request, minimizing the risk of unauthorized entry. By verifying users and devices dynamically, ZTNA ensures granular control and reduces the attack surface more effectively than traditional VPNs.
Table of Comparison
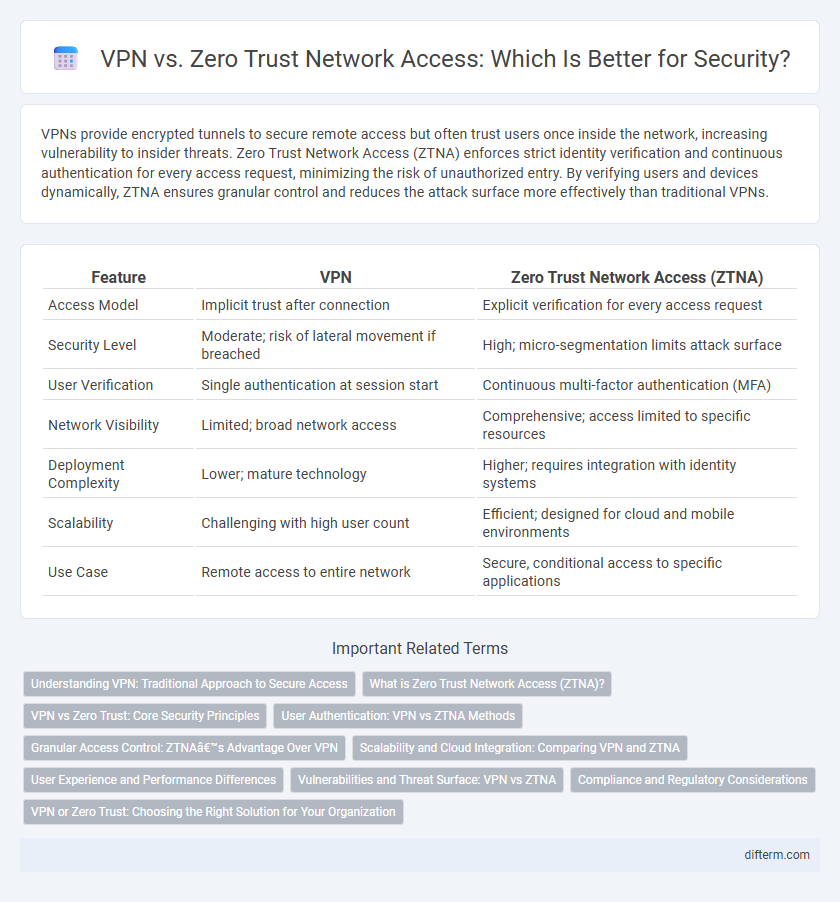
| Feature | VPN | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Access Model | Implicit trust after connection | Explicit verification for every access request |
| Security Level | Moderate; risk of lateral movement if breached | High; micro-segmentation limits attack surface |
| User Verification | Single authentication at session start | Continuous multi-factor authentication (MFA) |
| Network Visibility | Limited; broad network access | Comprehensive; access limited to specific resources |
| Deployment Complexity | Lower; mature technology | Higher; requires integration with identity systems |
| Scalability | Challenging with high user count | Efficient; designed for cloud and mobile environments |
| Use Case | Remote access to entire network | Secure, conditional access to specific applications |
Understanding VPN: Traditional Approach to Secure Access
Virtual Private Networks (VPNs) provide encrypted tunnels that securely connect remote users to an organization's internal network, relying on perimeter-based security models. This traditional approach grants users broad access once authenticated, increasing risk if credentials are compromised. VPNs lack granular control and continuous verification, which limits their effectiveness against modern cyber threats.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a security framework that restricts user access to applications and data based on strict identity verification, regardless of the user's location or device. Unlike traditional VPNs that provide broad network access, ZTNA enforces granular, role-based access controls by continuously validating trust before granting entry. This approach significantly reduces the risk of lateral movement within networks and enhances protection against unauthorized access and cyber threats.
VPN vs Zero Trust: Core Security Principles
VPNs create encrypted tunnels to protect data in transit, but trust all users inside the network perimeter implicitly, posing risks if credentials are compromised. Zero Trust Network Access (ZTNA) enforces strict identity verification and least-privilege access, continually validating every user and device regardless of location. This core security principle reduces attack surfaces by minimizing implicit trust and adapting dynamically to threats.
User Authentication: VPN vs ZTNA Methods
VPN relies on traditional user authentication methods like username and password, often supplemented with multi-factor authentication (MFA) to verify identity. Zero Trust Network Access (ZTNA) uses continuous, context-aware authentication that evaluates user behavior, device health, and location before granting access. ZTNA's dynamic authentication model enhances security by minimizing unauthorized access risks compared to static VPN credentials.
Granular Access Control: ZTNA’s Advantage Over VPN
Zero Trust Network Access (ZTNA) provides granular access control by authenticating and authorizing users and devices for specific applications or resources, minimizing the attack surface compared to traditional VPNs that grant broad network access. ZTNA enforces least-privilege access policies dynamically, facilitating real-time monitoring and reducing the risk of lateral movement within the network. This fine-grained approach significantly enhances security posture and compliance over the all-or-nothing access model typical of VPN solutions.
Scalability and Cloud Integration: Comparing VPN and ZTNA
VPNs often face scalability challenges due to limited capacity and complex configurations when extending access to numerous remote users, whereas Zero Trust Network Access (ZTNA) offers dynamic, policy-based access controls that scale efficiently across distributed environments. ZTNA integrates seamlessly with cloud-native infrastructures, providing granular, context-aware security that aligns with modern cloud applications and workloads. This enables organizations to enhance security posture while maintaining performance and flexibility in rapidly evolving cloud ecosystems.
User Experience and Performance Differences
VPNs often experience latency and slower connection speeds due to routing all traffic through centralized servers, which can degrade user experience. Zero Trust Network Access (ZTNA) optimizes performance by granting secure, direct access to specific applications based on continuous verification, minimizing network congestion. ZTNA enhances user experience with seamless, context-aware authentication and reduced access delays compared to traditional VPNs.
Vulnerabilities and Threat Surface: VPN vs ZTNA
VPNs increase the attack surface by providing broad network access, making it easier for threat actors to exploit vulnerabilities once inside the network. Zero Trust Network Access (ZTNA) minimizes vulnerabilities by enforcing strict access controls based on continuous verification of user identity and device posture. ZTNA's micro-segmentation and least-privilege principles significantly reduce lateral movement and threat exposure compared to traditional VPNs.
Compliance and Regulatory Considerations
Zero Trust Network Access (ZTNA) offers granular access controls that align closely with compliance frameworks such as GDPR, HIPAA, and PCI-DSS by enforcing strict user authentication and continuous verification, reducing the risk of data breaches. Virtual Private Networks (VPNs) provide encrypted tunnels but often lack detailed access policies, potentially exposing organizations to regulatory non-compliance due to broad network access. Implementing ZTNA can streamline audit processes and demonstrate adherence to security mandates by limiting access based on user identity, device posture, and contextual risk factors.
VPN or Zero Trust: Choosing the Right Solution for Your Organization
VPNs provide secure remote access by encrypting internet connections and masking IP addresses, ideal for straightforward, perimeter-based security needs. Zero Trust Network Access (ZTNA) enforces strict identity verification and granular access controls, reducing insider threats and minimizing attack surfaces for dynamic, hybrid environments. Organizations prioritizing adaptive security and minimizing lateral movement risks benefit from adopting ZTNA over traditional VPN solutions.
VPN vs Zero Trust Network Access Infographic
 difterm.com
difterm.com