Role-Based Access Control (RBAC) restricts system access based on predefined user roles, simplifying permission management but often lacking flexibility. Attribute-Based Access Control (ABAC) uses user, resource, and environmental attributes to enforce granular, context-aware policies, enhancing security in dynamic environments. Organizations with complex security requirements benefit from ABAC's dynamic decision-making, while RBAC remains effective for straightforward, role-centric access control.
Table of Comparison
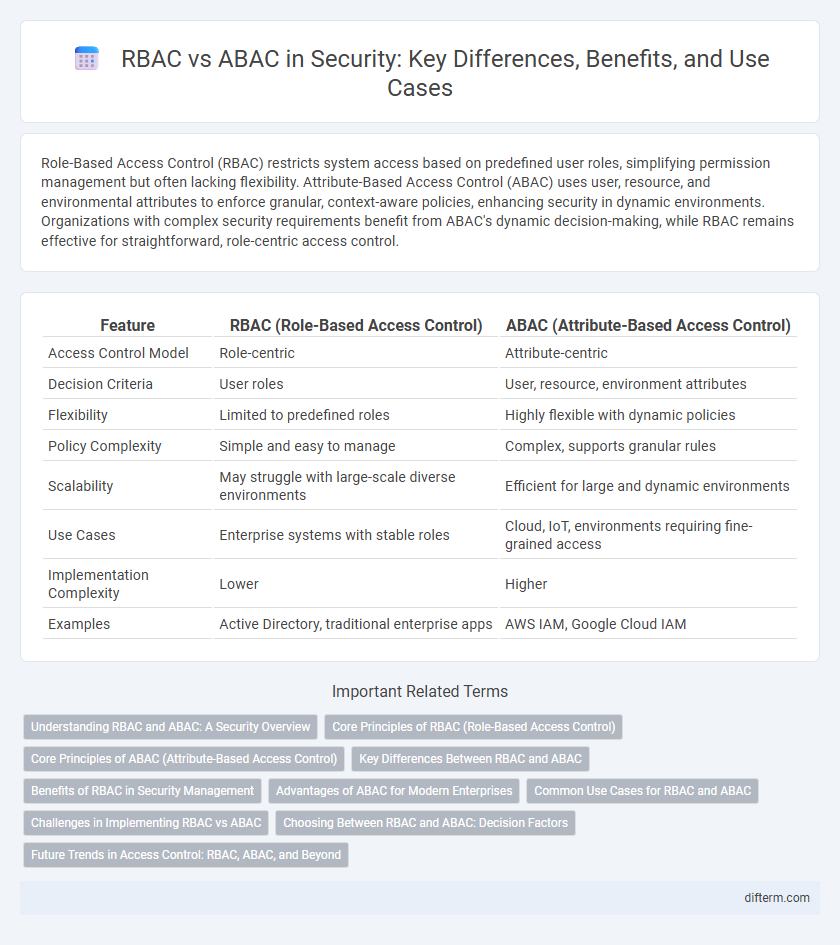
| Feature | RBAC (Role-Based Access Control) | ABAC (Attribute-Based Access Control) |
|---|---|---|
| Access Control Model | Role-centric | Attribute-centric |
| Decision Criteria | User roles | User, resource, environment attributes |
| Flexibility | Limited to predefined roles | Highly flexible with dynamic policies |
| Policy Complexity | Simple and easy to manage | Complex, supports granular rules |
| Scalability | May struggle with large-scale diverse environments | Efficient for large and dynamic environments |
| Use Cases | Enterprise systems with stable roles | Cloud, IoT, environments requiring fine-grained access |
| Implementation Complexity | Lower | Higher |
| Examples | Active Directory, traditional enterprise apps | AWS IAM, Google Cloud IAM |
Understanding RBAC and ABAC: A Security Overview
Role-Based Access Control (RBAC) assigns permissions based on predefined user roles, streamlining access management and reducing administrative complexity. Attribute-Based Access Control (ABAC) utilizes user attributes, resource attributes, and environmental conditions to enforce dynamic and context-aware security policies. Comparing RBAC and ABAC highlights that RBAC is suited for static, role-driven environments, whereas ABAC offers granular, flexible security in complex, evolving systems.
Core Principles of RBAC (Role-Based Access Control)
Role-Based Access Control (RBAC) operates on the core principles of role assignment, role authorization, and permission authorization, ensuring users gain access solely based on their designated roles within an organization. This model simplifies permission management by grouping access rights into roles, which are then assigned to users, streamlining administrative tasks and enhancing security policies. RBAC's emphasis on predefined roles prevents unauthorized access and supports compliance with regulatory frameworks, making it a foundational element in enterprise security architectures.
Core Principles of ABAC (Attribute-Based Access Control)
ABAC (Attribute-Based Access Control) enforces security by evaluating user, resource, and environmental attributes to determine access permissions, contrasting with RBAC's fixed role assignments. Core principles of ABAC include dynamic policy evaluation based on multiple attributes, fine-grained access control tailored to context, and enhanced flexibility for complex security requirements. This model supports improved compliance and reduces risks by enabling precise, attribute-driven authorization decisions.
Key Differences Between RBAC and ABAC
RBAC (Role-Based Access Control) assigns permissions based on predefined user roles, simplifying management but often lacking flexibility for dynamic environments. ABAC (Attribute-Based Access Control) leverages user, resource, and environmental attributes to make real-time access decisions, enabling granular and context-aware security policies. Key differences include RBAC's reliance on static roles versus ABAC's dynamic evaluation of multiple attributes for precise access control.
Benefits of RBAC in Security Management
Role-Based Access Control (RBAC) enhances security management by simplifying permission assignments through predefined roles aligned with organizational functions, reducing the risk of unauthorized access. It improves auditability and compliance by providing clear access control policies tied to job responsibilities, making it easier to monitor and manage user privileges. RBAC also accelerates onboarding and offboarding processes, minimizing human error and ensuring consistent enforcement of security policies across the enterprise.
Advantages of ABAC for Modern Enterprises
Attribute-Based Access Control (ABAC) offers modern enterprises enhanced security by enabling dynamic, context-aware access decisions based on user, resource, action, and environmental attributes. Unlike Role-Based Access Control (RBAC), ABAC supports fine-grained policies that adapt to complex organizational structures and evolving compliance requirements. This flexibility reduces risk by enforcing precise access controls and improving overall governance in diverse and distributed IT environments.
Common Use Cases for RBAC and ABAC
Role-Based Access Control (RBAC) is commonly used in organizations with well-defined job functions, such as enterprise IT environments managing employee permissions based on roles like admin, manager, or user. Attribute-Based Access Control (ABAC) excels in dynamic scenarios requiring fine-grained access decisions using user attributes, resource characteristics, and environmental conditions, frequently implemented in cloud services and healthcare systems. Both RBAC and ABAC support regulatory compliance, with RBAC simplifying access management in hierarchical structures, while ABAC enables context-aware policies for complex, multi-dimensional access requirements.
Challenges in Implementing RBAC vs ABAC
Implementing Role-Based Access Control (RBAC) faces challenges in managing role explosion and maintaining role hierarchies as organizational structures grow complex. Attribute-Based Access Control (ABAC) introduces difficulties in defining and evaluating dynamic policies and attributes consistently across diverse systems. Both models require robust governance frameworks to ensure accurate access decisions and prevent privilege creep in evolving security environments.
Choosing Between RBAC and ABAC: Decision Factors
Choosing between RBAC and ABAC depends on the complexity of access control requirements and the organization's scalability needs. RBAC offers simplicity by assigning permissions to roles, ideal for environments with well-defined job functions, whereas ABAC provides granular control using attributes and policies, suited for dynamic and context-aware access management. Organizations must evaluate factors such as the frequency of access changes, regulatory compliance demands, and system integration capabilities to determine the most effective model.
Future Trends in Access Control: RBAC, ABAC, and Beyond
Future trends in access control emphasize the integration of Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) to enhance security frameworks. Hybrid models leverage RBAC's simplicity with ABAC's fine-grained policy enforcement, enabling dynamic, context-aware access decisions across complex environments. Advancements in AI-driven analytics and blockchain technology are poised to revolutionize access control by automating attribute evaluations and ensuring immutable policy enforcement.
RBAC vs ABAC Infographic
 difterm.com
difterm.com