Fuzz testing identifies security vulnerabilities by automatically inputting random or unexpected data into software to uncover runtime errors and crashes. Static analysis examines source code without execution, detecting potential security flaws by analyzing code patterns and structures. Combining fuzz testing with static analysis enhances overall security by addressing different types of vulnerabilities throughout the software development lifecycle.
Table of Comparison
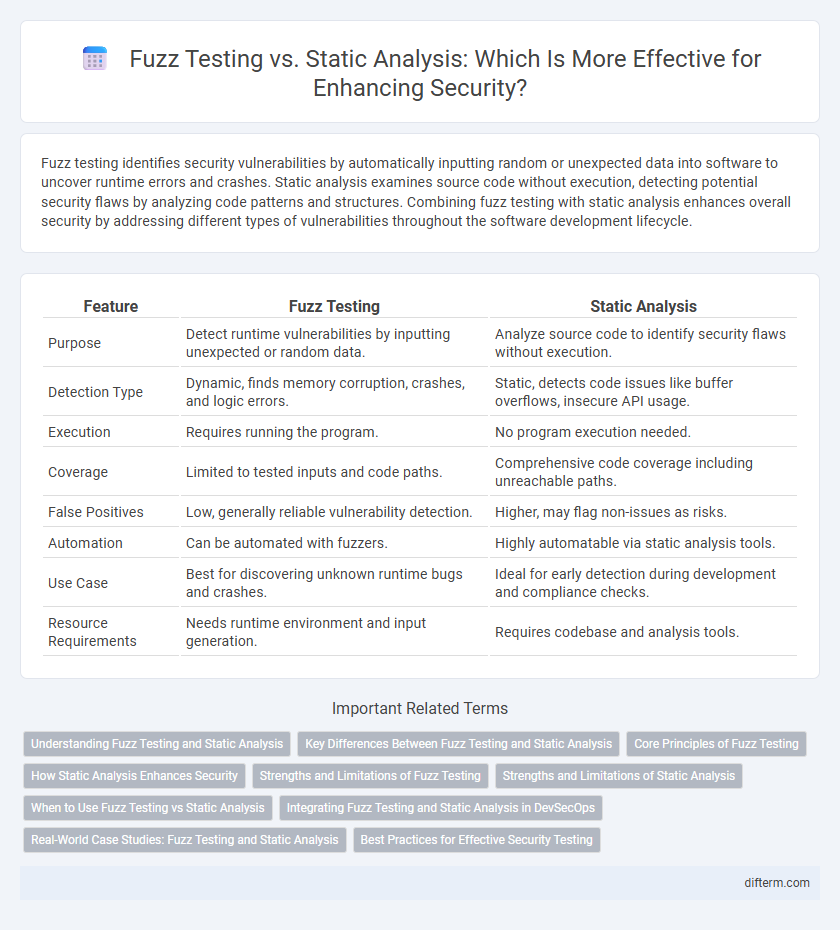
| Feature | Fuzz Testing | Static Analysis |
|---|---|---|
| Purpose | Detect runtime vulnerabilities by inputting unexpected or random data. | Analyze source code to identify security flaws without execution. |
| Detection Type | Dynamic, finds memory corruption, crashes, and logic errors. | Static, detects code issues like buffer overflows, insecure API usage. |
| Execution | Requires running the program. | No program execution needed. |
| Coverage | Limited to tested inputs and code paths. | Comprehensive code coverage including unreachable paths. |
| False Positives | Low, generally reliable vulnerability detection. | Higher, may flag non-issues as risks. |
| Automation | Can be automated with fuzzers. | Highly automatable via static analysis tools. |
| Use Case | Best for discovering unknown runtime bugs and crashes. | Ideal for early detection during development and compliance checks. |
| Resource Requirements | Needs runtime environment and input generation. | Requires codebase and analysis tools. |
Understanding Fuzz Testing and Static Analysis
Fuzz testing involves feeding random or malformed inputs into software to identify vulnerabilities and crashes, making it effective for discovering unknown security flaws. Static analysis examines source code or binaries without execution to detect potential security issues such as buffer overflows, injection flaws, and coding violations early in the development cycle. Combining fuzz testing and static analysis enhances security by addressing both dynamic runtime behaviors and code-based vulnerabilities.
Key Differences Between Fuzz Testing and Static Analysis
Fuzz testing identifies vulnerabilities by inputting random or unexpected data into running programs to trigger crashes or errors, providing dynamic, runtime insights. Static analysis examines source code without execution to detect potential security flaws, enabling early detection during development. Fuzz testing excels at uncovering runtime memory corruption and logic errors, while static analysis efficiently finds code syntax issues, insecure coding patterns, and vulnerabilities across the entire codebase.
Core Principles of Fuzz Testing
Fuzz testing operates by automatically generating and inputting random or malformed data into software to uncover security vulnerabilities and crashes, emphasizing dynamic code execution. It focuses on exploring unexpected execution paths and identifying runtime errors, such as buffer overflows and memory leaks, that static analysis might miss. This technique relies on monitoring application behavior under stress conditions to detect anomalies, making it invaluable for discovering zero-day exploits and complex bugs.
How Static Analysis Enhances Security
Static analysis enhances security by identifying vulnerabilities and coding errors early in the software development lifecycle, enabling developers to address potential threats before deployment. It provides automated, comprehensive code reviews that detect issues like buffer overflows, injection flaws, and insecure coding patterns without executing the program. Integrating static analysis tools into continuous integration pipelines ensures consistent enforcement of security policies and reduces the risk of introducing exploitable vulnerabilities in production environments.
Strengths and Limitations of Fuzz Testing
Fuzz testing excels at detecting runtime vulnerabilities by automatically generating malformed inputs to expose bugs such as buffer overflows, memory leaks, and crashes that occur during actual program execution. It provides concrete evidence of security issues by triggering faults in real-time, which static analysis may overlook due to its reliance on code inspection without execution. However, fuzz testing struggles with coverage limitations, struggling to explore deep or rare execution paths and often missing vulnerabilities that require specific input sequences or contextual conditions.
Strengths and Limitations of Static Analysis
Static analysis excels at identifying security vulnerabilities early by analyzing source code without execution, enabling detection of issues like buffer overflows, injection flaws, and unsafe API usage. It provides comprehensive coverage, including dead code and complex control flows, but often generates false positives and struggles with runtime context or dynamic behavior. Despite limitations in detecting runtime-specific vulnerabilities, static analysis remains essential for early bug detection and compliance enforcement in secure software development.
When to Use Fuzz Testing vs Static Analysis
Fuzz testing excels in identifying runtime vulnerabilities by inputting malformed or unexpected data to uncover security flaws and memory errors during program execution. Static analysis is ideal during early development phases, scanning source code for coding errors, insecure patterns, and compliance violations without executing the program. Use fuzz testing when dynamic behavior and real-world attack scenarios need validation, and choose static analysis for comprehensive code review and early detection of security risks.
Integrating Fuzz Testing and Static Analysis in DevSecOps
Integrating fuzz testing and static analysis within DevSecOps enhances vulnerability detection by combining dynamic input generation with code-level inspection, enabling comprehensive security coverage during development. Fuzz testing uncovers runtime errors and unexpected behavior by executing varied and unexpected inputs, while static analysis identifies code vulnerabilities early without code execution. This synergy accelerates feedback loops, reduces false positives, and strengthens application security throughout continuous integration and continuous delivery pipelines.
Real-World Case Studies: Fuzz Testing and Static Analysis
Real-world case studies demonstrate that fuzz testing excels at uncovering runtime vulnerabilities such as memory corruption and input validation errors in complex software like web browsers and network protocols. Static analysis tools consistently identify coding errors, potential security flaws, and compliance issues by analyzing source code without execution, proven effective in large-scale projects like open-source operating systems and financial applications. Combining fuzz testing with static analysis provides comprehensive security coverage, reducing false negatives and increasing vulnerability detection rates in enterprise software environments.
Best Practices for Effective Security Testing
Fuzz testing uncovers vulnerabilities by feeding unpredictable inputs to software, revealing runtime errors and memory leaks that static analysis might miss. Static analysis complements fuzzing by detecting code-level security flaws early in development through automated scanning of source code for patterns linked to vulnerabilities. Integrating fuzz testing with static analysis, combined with continuous updating of test cases and code analysis tools, ensures comprehensive coverage and enhances the effectiveness of security testing protocols.
Fuzz Testing vs Static Analysis Infographic
 difterm.com
difterm.com