Social engineering manipulates human behavior to gain unauthorized access, exploiting trust and psychological tactics rather than system vulnerabilities. Technical exploits, however, leverage software or hardware weaknesses to breach security defenses directly. Understanding both methods is crucial for comprehensive security pet protection strategies.
Table of Comparison
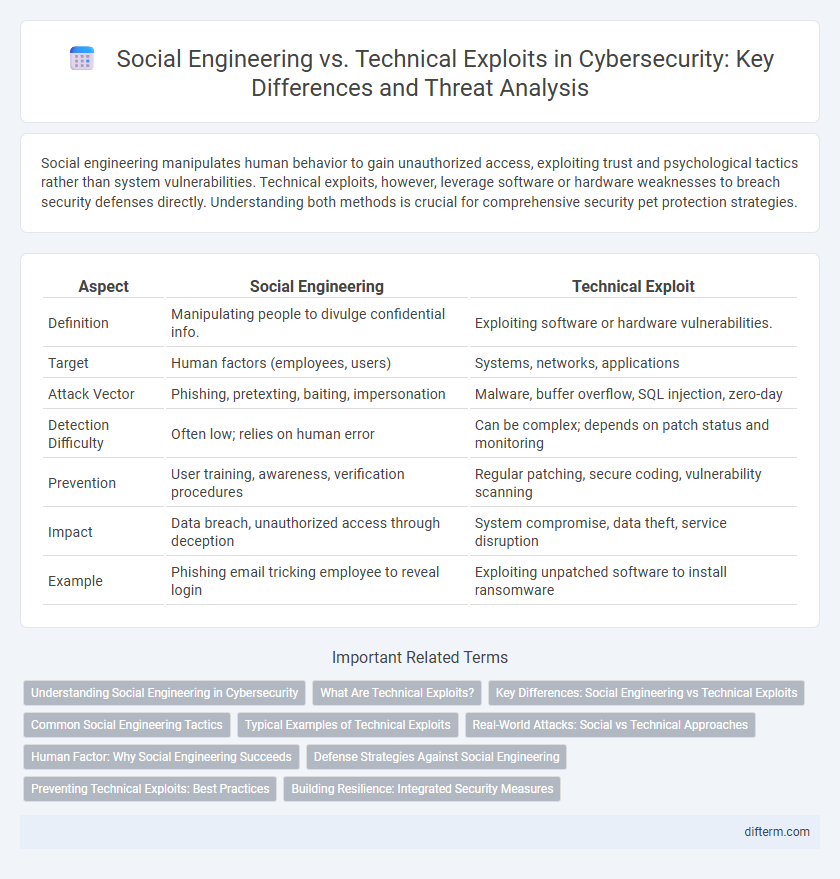
| Aspect | Social Engineering | Technical Exploit |
|---|---|---|
| Definition | Manipulating people to divulge confidential info. | Exploiting software or hardware vulnerabilities. |
| Target | Human factors (employees, users) | Systems, networks, applications |
| Attack Vector | Phishing, pretexting, baiting, impersonation | Malware, buffer overflow, SQL injection, zero-day |
| Detection Difficulty | Often low; relies on human error | Can be complex; depends on patch status and monitoring |
| Prevention | User training, awareness, verification procedures | Regular patching, secure coding, vulnerability scanning |
| Impact | Data breach, unauthorized access through deception | System compromise, data theft, service disruption |
| Example | Phishing email tricking employee to reveal login | Exploiting unpatched software to install ransomware |
Understanding Social Engineering in Cybersecurity
Social engineering manipulates human psychology to gain unauthorized access to sensitive information, contrasting with technical exploits that target software vulnerabilities. Techniques such as phishing, pretexting, and baiting rely on deception rather than code exploitation, emphasizing the critical need for user awareness and training in cybersecurity defense. Understanding social engineering enhances threat detection by prioritizing human factors alongside traditional technical safeguards.
What Are Technical Exploits?
Technical exploits are methods that attackers use to take advantage of vulnerabilities in software, hardware, or networks to gain unauthorized access or cause damage. These exploits often involve coding techniques like buffer overflows, SQL injection, or zero-day vulnerabilities that manipulate system weaknesses. Understanding technical exploits is crucial for developing effective security measures such as patch management, intrusion detection systems, and secure coding practices.
Key Differences: Social Engineering vs Technical Exploits
Social Engineering exploits human psychology by manipulating individuals into revealing confidential information, whereas Technical Exploits target software vulnerabilities to gain unauthorized access. Social Engineering involves tactics such as phishing, pretexting, and baiting, which rely on deception and trust, while Technical Exploits utilize methods like malware, zero-day attacks, and buffer overflows to compromise systems. Understanding these key differences is vital for developing comprehensive security strategies that address both human and technological weaknesses.
Common Social Engineering Tactics
Common social engineering tactics include phishing, pretexting, baiting, and tailgating, which manipulate human psychology to gain unauthorized access or sensitive information. Attackers often impersonate trusted figures or create a sense of urgency to exploit victims' trust and prompt immediate action. These methods contrast with technical exploits that target software vulnerabilities, emphasizing the need for security awareness training alongside technological defenses.
Typical Examples of Technical Exploits
Typical examples of technical exploits include buffer overflows, SQL injection, and cross-site scripting (XSS), which target software vulnerabilities to gain unauthorized access or control. Malware such as ransomware and trojans exploits system weaknesses to compromise data integrity and availability. Zero-day exploits leverage previously unknown vulnerabilities, making early detection and patching critical for maintaining security.
Real-World Attacks: Social vs Technical Approaches
Social engineering attacks exploit human psychology to manipulate individuals into divulging confidential information, often bypassing technical safeguards and relying on tactics such as phishing, pretexting, and baiting. Technical exploits leverage software vulnerabilities and system weaknesses, utilizing malware, zero-day attacks, or brute force methods to gain unauthorized access to networks and data. Real-world attacks frequently combine social and technical approaches, increasing effectiveness by deceiving users to activate malicious software or reveal access credentials.
Human Factor: Why Social Engineering Succeeds
Social engineering succeeds because it exploits the inherent trust and psychological vulnerabilities of humans, making individuals the weakest link in security defenses. Attackers manipulate emotions like fear, curiosity, and urgency to bypass technical safeguards without needing to exploit software or hardware vulnerabilities. Understanding human behavior is crucial for developing effective training programs to mitigate social engineering risks.
Defense Strategies Against Social Engineering
Effective defense strategies against social engineering prioritize employee education and awareness training to recognize phishing, pretexting, and baiting attempts. Implementing strict verification protocols, such as multi-factor authentication and callback verification, reduces the risk of unauthorized access through manipulated human interactions. Continuous monitoring of network activity and reporting suspicious behavior create an adaptive security posture to counter evolving social engineering tactics.
Preventing Technical Exploits: Best Practices
Preventing technical exploits requires implementing robust cybersecurity measures such as regular software patching, system hardening, and continuous vulnerability assessments. Employing multi-factor authentication, firewall configurations, and intrusion detection systems significantly reduces the risk of unauthorized access. Consistent employee training on identifying suspicious activities complements these strategies, creating a comprehensive defense against technical exploits.
Building Resilience: Integrated Security Measures
Building resilience against cyber threats requires a combination of defensive strategies targeting both social engineering and technical exploits. Implementing multi-layered security measures such as employee training on phishing awareness, robust authentication protocols, and regular system vulnerability assessments enhances the organization's ability to detect and mitigate attacks. Integrating behavioral analytics with advanced threat detection technologies ensures comprehensive protection against human manipulation and technical vulnerabilities simultaneously.
Social Engineering vs Technical Exploit Infographic
 difterm.com
difterm.com