Credential stuffing exploits stolen username-password pairs by automating login attempts across multiple sites, relying on users recycling passwords. Password spraying targets many accounts with a few common passwords to avoid account lockouts while maximizing access chances. Both attacks highlight the critical importance of strong, unique passwords and multi-factor authentication in defending against unauthorized access.
Table of Comparison
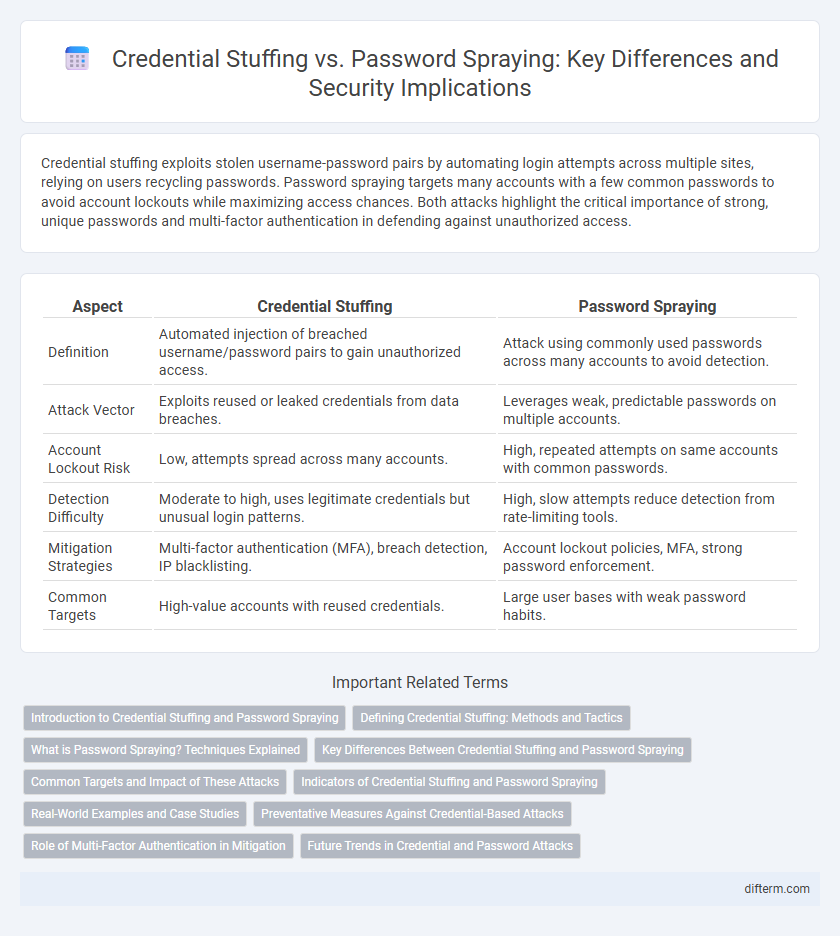
| Aspect | Credential Stuffing | Password Spraying |
|---|---|---|
| Definition | Automated injection of breached username/password pairs to gain unauthorized access. | Attack using commonly used passwords across many accounts to avoid detection. |
| Attack Vector | Exploits reused or leaked credentials from data breaches. | Leverages weak, predictable passwords on multiple accounts. |
| Account Lockout Risk | Low, attempts spread across many accounts. | High, repeated attempts on same accounts with common passwords. |
| Detection Difficulty | Moderate to high, uses legitimate credentials but unusual login patterns. | High, slow attempts reduce detection from rate-limiting tools. |
| Mitigation Strategies | Multi-factor authentication (MFA), breach detection, IP blacklisting. | Account lockout policies, MFA, strong password enforcement. |
| Common Targets | High-value accounts with reused credentials. | Large user bases with weak password habits. |
Introduction to Credential Stuffing and Password Spraying
Credential stuffing exploits large databases of stolen usernames and passwords, automating login attempts across multiple sites to gain unauthorized access. Password spraying targets a single or limited number of accounts by trying common passwords, avoiding account lockouts associated with repeated failed attempts. Both techniques capitalize on weak or reused credentials, posing significant risks to organizational security and user data privacy.
Defining Credential Stuffing: Methods and Tactics
Credential stuffing involves using automated tools to inject large volumes of stolen username and password pairs obtained from previous data breaches into multiple login portals to gain unauthorized access. Attackers deploy sophisticated bots that mimic human behavior, evading detection by bypassing rate limits and IP blocking while exploiting credential reuse across platforms. This tactic focuses on the validity of breached credentials rather than guessing passwords, differentiating it fundamentally from password spraying methods.
What is Password Spraying? Techniques Explained
Password spraying is a cyberattack technique where attackers use a small set of commonly used passwords against many different accounts to avoid detection by lockout mechanisms. Unlike credential stuffing, which uses leaked username-password pairs, password spraying targets widespread accounts with generic passwords like "123456" or "Password1." This method exploits weak password policies and user behavior, making it a persistent threat to organizational security.
Key Differences Between Credential Stuffing and Password Spraying
Credential stuffing exploits large volumes of stolen username-password pairs to breach multiple accounts automatically, relying on users reusing credentials across sites, while password spraying targets numerous accounts with a limited set of common passwords to avoid account lockouts. Credential stuffing attacks typically involve high-speed, automated login attempts using leaked databases, whereas password spraying emphasizes stealth and slow, distributed attempts to bypass security thresholds. Understanding these key differences informs more effective defense strategies, including anomaly detection and adaptive authentication policies.
Common Targets and Impact of These Attacks
Credential stuffing primarily targets large-scale online platforms such as e-commerce sites, social media networks, and financial services where users often reuse passwords, leading to mass account takeovers. Password spraying typically focuses on enterprise environments and cloud services by attempting a few commonly used passwords across many accounts to avoid detection, often resulting in unauthorized access to sensitive corporate data. Both attacks contribute to significant financial losses, reputational damage, and increased vulnerability to subsequent data breaches.
Indicators of Credential Stuffing and Password Spraying
Credential stuffing attacks are identified by rapid, repeated login attempts using lists of compromised credentials, often targeting multiple accounts with the same password across various platforms. Password spraying is detected by slow, systematic login attempts using a few commonly used passwords across many accounts to avoid triggering account lockouts. Unusual login patterns, an increase in failed authentications, and multiple IP addresses attempting access to numerous user accounts indicate these credential-based threats.
Real-World Examples and Case Studies
Credential stuffing attacks exploited leaked credentials in the 2019 Marriott breach, leading to unauthorized access to millions of guest accounts. Password spraying was demonstrated in the 2020 Microsoft Exchange hack, where attackers used common passwords across numerous accounts to evade detection. These case studies highlight how attackers tailor techniques based on available data and target organizations with varied defenses.
Preventative Measures Against Credential-Based Attacks
Implement multifactor authentication (MFA) to significantly reduce the risk of credential stuffing and password spraying attacks by adding an extra layer of security beyond passwords. Employ monitoring tools that detect unusual login patterns and limit the number of failed login attempts to prevent automated credential abuse. Regularly update password policies to enforce strong, unique passwords and educate users about phishing risks to minimize compromised credentials in the workforce.
Role of Multi-Factor Authentication in Mitigation
Credential stuffing and password spraying attacks exploit stolen or commonly used credentials to breach accounts, posing significant security risks. Multi-factor authentication (MFA) plays a crucial role in mitigation by requiring additional verification beyond passwords, effectively blocking unauthorized access even if credentials are compromised. Implementing MFA significantly reduces the success rate of these attacks by adding layers of security, such as biometric verification or one-time codes.
Future Trends in Credential and Password Attacks
Emerging trends in credential stuffing highlight increased use of AI-driven automation to bypass multi-factor authentication and exploit massive data breaches rapidly. Password spraying is evolving with sophisticated algorithms that rotate common passwords against targeted accounts, reducing detection risks. Future security strategies must prioritize adaptive machine learning defenses and continuous behavioral analysis to counteract these advancing attack methods.
Credential Stuffing vs Password Spraying Infographic
 difterm.com
difterm.com