Social engineering exploits human psychology to manipulate individuals into revealing confidential information, while phishing uses deceptive emails or websites to trick users into disclosing sensitive data. Both tactics aim to bypass traditional security measures by targeting user behavior instead of technical vulnerabilities. Understanding and recognizing these threats is crucial for effective cybersecurity defense.
Table of Comparison
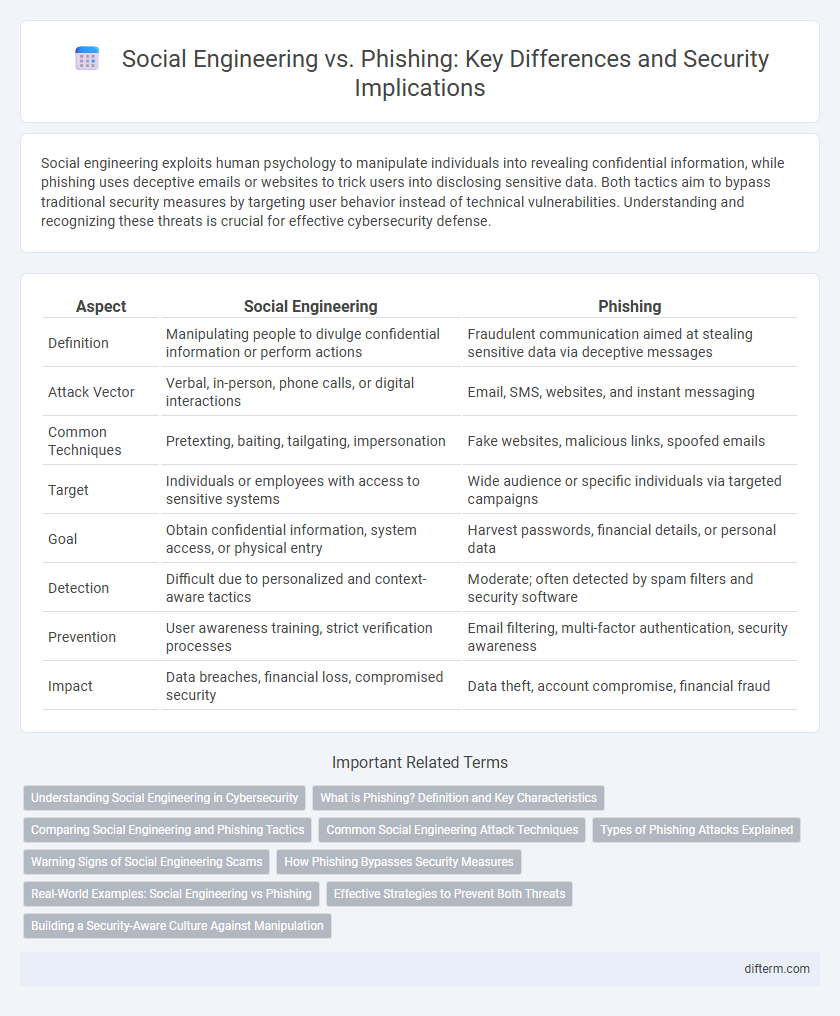
| Aspect | Social Engineering | Phishing |
|---|---|---|
| Definition | Manipulating people to divulge confidential information or perform actions | Fraudulent communication aimed at stealing sensitive data via deceptive messages |
| Attack Vector | Verbal, in-person, phone calls, or digital interactions | Email, SMS, websites, and instant messaging |
| Common Techniques | Pretexting, baiting, tailgating, impersonation | Fake websites, malicious links, spoofed emails |
| Target | Individuals or employees with access to sensitive systems | Wide audience or specific individuals via targeted campaigns |
| Goal | Obtain confidential information, system access, or physical entry | Harvest passwords, financial details, or personal data |
| Detection | Difficult due to personalized and context-aware tactics | Moderate; often detected by spam filters and security software |
| Prevention | User awareness training, strict verification processes | Email filtering, multi-factor authentication, security awareness |
| Impact | Data breaches, financial loss, compromised security | Data theft, account compromise, financial fraud |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. Unlike phishing, which primarily uses deceptive emails or messages to trick users, social engineering involves a broader range of tactics, including pretexting, baiting, and tailgating. Effective defense requires employee training, awareness programs, and robust verification protocols to identify and thwart human-based cyber threats.
What is Phishing? Definition and Key Characteristics
Phishing is a cyberattack technique that involves fraudulent attempts to obtain sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in electronic communications. Key characteristics include deceptive emails or messages that create a sense of urgency, use spoofed websites mimicking legitimate services, and employ social engineering tactics to manipulate recipients into divulging confidential data. This method exploits human psychology rather than technical vulnerabilities to breach security defenses.
Comparing Social Engineering and Phishing Tactics
Social engineering tactics manipulate human psychology to gain unauthorized access to sensitive information, often using pretexting, baiting, or tailgating techniques. Phishing specifically employs fraudulent emails or messages designed to deceive recipients into revealing credentials or clicking malicious links. Both methods exploit trust and human error, but phishing relies primarily on digital communication channels, while social engineering can include in-person or phone-based interactions.
Common Social Engineering Attack Techniques
Common social engineering attack techniques include pretexting, baiting, and tailgating, which manipulate human psychology to gain unauthorized access or information. Phishing specifically targets individuals through deceptive emails or messages designed to steal sensitive data such as login credentials or financial details. Understanding these techniques is crucial for strengthening cybersecurity measures and preventing breaches caused by human error.
Types of Phishing Attacks Explained
Phishing attacks encompass various types including spear phishing, where attackers target specific individuals with personalized messages, and whaling, which focuses on high-profile targets like executives. Clone phishing involves duplicating legitimate emails to trick recipients into revealing sensitive data or clicking malicious links. Other common methods include vishing (voice phishing) and smishing (SMS phishing), each exploiting different communication channels to deceive victims.
Warning Signs of Social Engineering Scams
Unusual requests for sensitive information such as passwords or personal details often signal social engineering scams. Attackers may create a sense of urgency or fear to manipulate victims into bypassing security protocols. Verification of the source and skepticism towards unsolicited communications can help identify these deceptive tactics.
How Phishing Bypasses Security Measures
Phishing attacks bypass security measures by exploiting human psychology rather than relying on technical vulnerabilities, often using deceptive emails and fake websites to trick users into revealing sensitive information. These attacks leverage social engineering techniques to manipulate trust and urgency, bypassing firewalls and antivirus software designed to detect malicious code. The effectiveness of phishing largely stems from its ability to target the user's decision-making process, making traditional security tools less effective in preventing credential theft or data breaches.
Real-World Examples: Social Engineering vs Phishing
Social engineering attacks exploit human psychology by manipulating individuals into divulging confidential information, such as the 2011 RSA SecurID breach where attackers used spear-phishing emails to deliver malware. Phishing schemes often use deceptive emails or websites mimicking trusted entities, exemplified by the 2016 Democratic National Committee email hack caused by credential theft via a phishing campaign. Both tactics rely on human error, but social engineering extends beyond digital channels, including in-person or phone-based manipulations, while phishing primarily targets users electronically.
Effective Strategies to Prevent Both Threats
Social engineering and phishing attacks exploit human psychology to gain unauthorized access to sensitive information, making employee training a critical defense strategy. Implementing multi-factor authentication (MFA) and regularly updating security protocols significantly reduce the risk of credential compromise and unauthorized entry. Continuous monitoring through advanced threat detection systems further enhances an organization's ability to identify and respond swiftly to these evolving cyber threats.
Building a Security-Aware Culture Against Manipulation
Building a security-aware culture is critical to defending against social engineering and phishing attacks, which exploit human psychology rather than technical vulnerabilities. Training employees to recognize tactics such as pretexting, baiting, and spear-phishing strengthens organizational resilience by reducing susceptibility to manipulation. Regular awareness programs, simulated phishing campaigns, and clear reporting mechanisms empower staff to identify and respond effectively to social engineering threats.
Social Engineering vs Phishing Infographic
 difterm.com
difterm.com