Salt and pepper are both cryptographic techniques used to enhance password security by adding unique data to passwords before hashing. Salt is a unique, random value generated for each password, stored alongside the hash to prevent rainbow table attacks and ensure that identical passwords produce different hashes. Pepper, typically a secret value added to the password before hashing, is kept server-side and not stored with the hash, providing an extra layer of security even if the database is compromised.
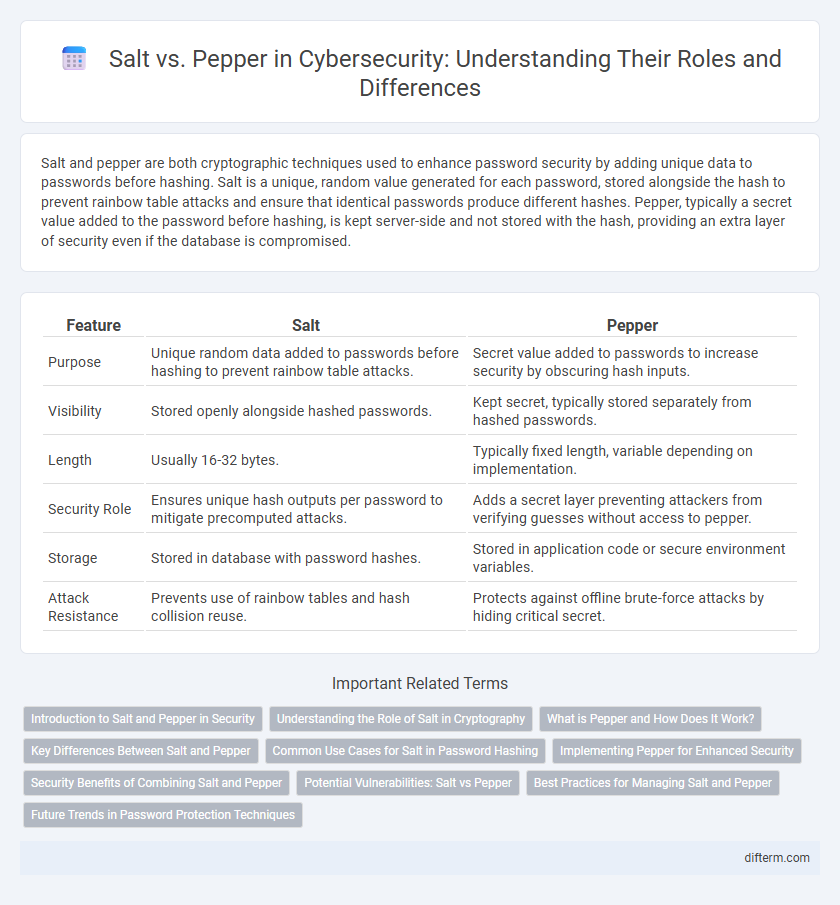
Table of Comparison
| Feature | Salt | Pepper |
|---|---|---|
| Purpose | Unique random data added to passwords before hashing to prevent rainbow table attacks. | Secret value added to passwords to increase security by obscuring hash inputs. |
| Visibility | Stored openly alongside hashed passwords. | Kept secret, typically stored separately from hashed passwords. |
| Length | Usually 16-32 bytes. | Typically fixed length, variable depending on implementation. |
| Security Role | Ensures unique hash outputs per password to mitigate precomputed attacks. | Adds a secret layer preventing attackers from verifying guesses without access to pepper. |
| Storage | Stored in database with password hashes. | Stored in application code or secure environment variables. |
| Attack Resistance | Prevents use of rainbow tables and hash collision reuse. | Protects against offline brute-force attacks by hiding critical secret. |
Introduction to Salt and Pepper in Security
Salt and pepper are cryptographic techniques used to enhance password security by mitigating risks of hash-based attacks. Salt is a unique, random value added to each password before hashing, ensuring that identical passwords produce different hashes. Pepper, typically a secret value stored separately from the database, adds another layer of complexity by being applied universally or selectively to passwords before hashing.
Understanding the Role of Salt in Cryptography
Salt in cryptography enhances password security by appending unique, random data to each password before hashing, preventing attackers from using precomputed hash tables like rainbow tables. This process ensures that identical passwords produce distinct hashes, significantly increasing resistance against brute-force and dictionary attacks. Unlike pepper, which is a secret value shared across passwords, salt is stored alongside the hash, maintaining its effectiveness through uniqueness rather than secrecy.
What is Pepper and How Does It Work?
Pepper is a secret cryptographic value added to passwords before hashing to enhance security by preventing attackers from using precomputed hash tables or rainbow tables. Unlike salt, which is unique and stored alongside each password, pepper is a fixed value kept hidden on the server, often embedded deep within the application code or configuration. By combining salt and pepper, password hashing becomes significantly more resistant to brute-force and dictionary attacks, improving overall system defense against credential breaches.
Key Differences Between Salt and Pepper
Salt in security refers to a unique random value added to passwords before hashing to prevent rainbow table attacks, ensuring each password hash is distinct even for identical passwords. Pepper is a secret value, stored separately from the database, added to the hash process to provide an additional layer of security against hash extraction and brute force attacks. The key difference lies in salt being unique per password and stored alongside the hash, while pepper is a fixed secret applied globally and kept confidential.
Common Use Cases for Salt in Password Hashing
Salt is widely used in password hashing to enhance security by adding unique random data to each password before hashing, preventing attackers from using precomputed hash tables like rainbow tables. It ensures that even identical passwords have different hashes, making brute-force attacks significantly more difficult. Common implementations include algorithms such as bcrypt, PBKDF2, and Argon2, which integrate salt to provide robust protection against various password-based attacks.
Implementing Pepper for Enhanced Security
Implementing pepper in security protocols involves adding a secret value stored separately from the database to hash functions, significantly strengthening password protection against rainbow table and brute-force attacks. Unlike salt, which is unique per password and stored alongside the hash, pepper remains confidential and consistent across users, providing an additional layer of defense. Incorporating pepper enhances security posture by minimizing risks associated with database breaches and complicating attackers' ability to reverse-engineer hashes.
Security Benefits of Combining Salt and Pepper
Combining salt and pepper in cryptographic hashing significantly enhances security by adding two layers of unique randomness to stored passwords, making brute-force and rainbow table attacks much more difficult. Salt, a random value unique to each password, prevents attackers from using precomputed hash databases, while pepper, a secret value known only to the server, adds an additional secret unknown to attackers. This dual approach reduces the risk of credential exposure even if the salt and hashed passwords are compromised, strengthening overall data protection.
Potential Vulnerabilities: Salt vs Pepper
Salt introduces unique, per-password randomness to hashed credentials, mitigating risks of rainbow table attacks while being stored alongside the hash, which can be exposed if the database is compromised. Pepper, a secret value added to passwords before hashing but kept separate from the database, enhances security by preventing attackers from easily verifying guessed passwords even with hash access; however, improper management or disclosure of the pepper can create a single point of failure. Both salt and pepper require secure generation and storage practices, as weaknesses in either can lead to brute force or credential cracking vulnerabilities.
Best Practices for Managing Salt and Pepper
Effective management of salt and pepper in security involves generating unique, cryptographically strong salts for each password and securely storing salts alongside hashed passwords to prevent collision attacks. Peppers, kept secret and stored separately from the database, add an extra layer of defense by complicating brute-force and rainbow table attacks. Implementing best practices includes rotating peppers periodically and using hardware security modules or environment variables to safeguard pepper values from exposure.
Future Trends in Password Protection Techniques
Emerging trends in password protection highlight the evolving role of salt and pepper techniques in enhancing cryptographic security against sophisticated cyberattacks. Future implementations are expected to integrate adaptive, context-aware salt strategies combined with secret pepper keys stored separately from hashed passwords to mitigate risks from database breaches. Advances in machine learning-driven anomaly detection will also complement these cryptographic measures, enabling real-time password integrity verification and reducing reliance on traditional static salts and peppers.
Salt vs Pepper Infographic
 difterm.com
difterm.com