File Integrity Monitoring ensures security by detecting unauthorized changes in critical system files, providing real-time alerts on potential breaches. Log Analysis complements this by examining system and application logs to identify suspicious activities or patterns that indicate security threats. Together, they form a robust defense strategy by continuously verifying file authenticity and scrutinizing event data for comprehensive protection.
Table of Comparison
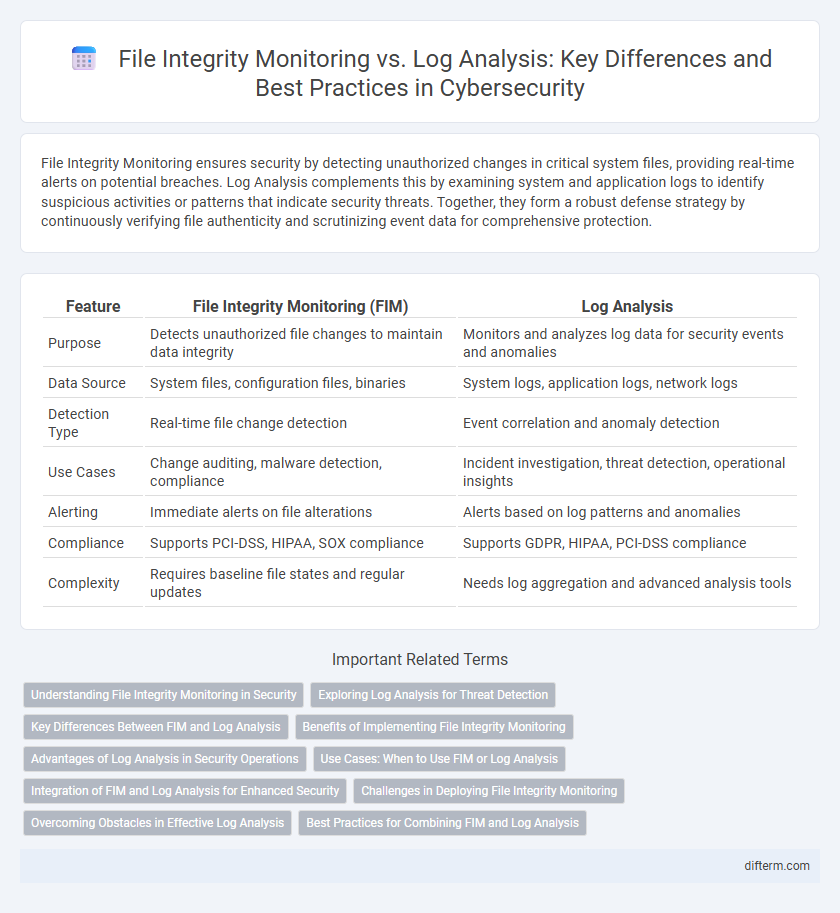
| Feature | File Integrity Monitoring (FIM) | Log Analysis |
|---|---|---|
| Purpose | Detects unauthorized file changes to maintain data integrity | Monitors and analyzes log data for security events and anomalies |
| Data Source | System files, configuration files, binaries | System logs, application logs, network logs |
| Detection Type | Real-time file change detection | Event correlation and anomaly detection |
| Use Cases | Change auditing, malware detection, compliance | Incident investigation, threat detection, operational insights |
| Alerting | Immediate alerts on file alterations | Alerts based on log patterns and anomalies |
| Compliance | Supports PCI-DSS, HIPAA, SOX compliance | Supports GDPR, HIPAA, PCI-DSS compliance |
| Complexity | Requires baseline file states and regular updates | Needs log aggregation and advanced analysis tools |
Understanding File Integrity Monitoring in Security
File Integrity Monitoring (FIM) plays a critical role in cybersecurity by continuously verifying the integrity of key system files, configurations, and software to detect unauthorized changes or tampering. By comparing current file states against a trusted baseline, FIM helps organizations promptly identify potential security breaches, malware infections, or insider threats. Effective implementation of FIM enhances compliance with standards such as PCI DSS, HIPAA, and GDPR while strengthening overall threat detection and incident response capabilities.
Exploring Log Analysis for Threat Detection
Log analysis for threat detection involves systematically examining system and application logs to identify unusual patterns or indicators of compromise that signal potential security breaches. By correlating log entries across multiple sources, security teams can detect anomalies such as unauthorized access, malware activity, and insider threats in real-time. Integrating log analysis with security information and event management (SIEM) systems enhances visibility, accelerates incident response, and complements file integrity monitoring for comprehensive cybersecurity defense.
Key Differences Between FIM and Log Analysis
File Integrity Monitoring (FIM) and Log Analysis serve distinct roles in cybersecurity; FIM tracks unauthorized changes to critical files by comparing their baseline states, while Log Analysis examines event logs to detect patterns and anomalies indicative of security threats. FIM provides real-time alerts about alterations to system files, configurations, and executables, ensuring data integrity, whereas Log Analysis aggregates and interprets vast log data from multiple sources to identify potential breaches or operational issues. The key difference lies in FIM's focus on file-level modifications versus Log Analysis's broader role in correlating event data for comprehensive threat detection and compliance monitoring.
Benefits of Implementing File Integrity Monitoring
File Integrity Monitoring (FIM) enhances cybersecurity by continuously tracking changes to critical system files, ensuring unauthorized modifications are detected in real-time. It provides detailed alerts on suspicious activities, enabling rapid incident response and reducing the risk of data breaches. FIM complements log analysis by offering granular file-level visibility, which is essential for compliance with standards like PCI DSS and HIPAA.
Advantages of Log Analysis in Security Operations
Log analysis enhances security operations by providing real-time insights into system activities, enabling rapid detection of anomalies and potential breaches. It aggregates and correlates vast amounts of log data from multiple sources, improving threat identification and incident response capabilities. Unlike file integrity monitoring, log analysis offers continuous visibility and context for security events, facilitating proactive defense mechanisms.
Use Cases: When to Use FIM or Log Analysis
File Integrity Monitoring (FIM) is essential for detecting unauthorized changes to critical system files and configurations, making it ideal for compliance reporting and early breach detection. Log analysis excels in monitoring system events, user activities, and network traffic to identify suspicious patterns, insider threats, and operational anomalies. Organizations should implement FIM for pinpointing file-level tampering while leveraging log analysis for comprehensive insight into system-wide security events and incident response.
Integration of FIM and Log Analysis for Enhanced Security
Integrating File Integrity Monitoring (FIM) with Log Analysis creates a robust security framework by correlating real-time file change data with system and application event logs, enabling faster detection of suspicious activities and potential breaches. This combined approach enhances incident response accuracy by providing comprehensive visibility into unauthorized file alterations alongside contextual log information, thereby reducing false positives. Leveraging automated alerts from both FIM and log analysis tools streamlines threat intelligence and compliance reporting, crucial for maintaining system integrity and regulatory adherence.
Challenges in Deploying File Integrity Monitoring
Deploying File Integrity Monitoring (FIM) presents challenges such as high false positive rates due to dynamic system changes, which complicate accurate baseline establishment. The need for continuous updates and tuning to account for legitimate software modifications demands significant administrative effort and resource allocation. Additionally, integrating FIM with existing security frameworks can be complex, requiring compatibility adjustments and thorough policy configurations to maintain effective monitoring.
Overcoming Obstacles in Effective Log Analysis
Effective log analysis faces obstacles such as data overload, inconsistent log formats, and false positives that hinder timely threat detection. Implementing automated parsing tools and employing machine learning algorithms enhances accurate pattern recognition and reduces noise in log data. Integrating file integrity monitoring provides contextual validation, improving incident response by correlating unauthorized changes with suspicious log events.
Best Practices for Combining FIM and Log Analysis
Combining File Integrity Monitoring (FIM) with log analysis enhances security by providing comprehensive visibility into unauthorized file changes and associated system activities. Best practices include correlating FIM alerts with log data from endpoints, servers, and security devices to quickly identify suspicious behavior patterns and reduce false positives. Implementing automated workflows that integrate FIM and log management tools improves incident response times and strengthens overall threat detection capabilities.
File Integrity Monitoring vs Log Analysis Infographic
 difterm.com
difterm.com