Static analysis examines code without executing it, identifying vulnerabilities early in the development process by scanning source code, binaries, or bytecode for security flaws. Dynamic analysis tests applications in a runtime environment, detecting issues that only appear during execution such as memory leaks, runtime errors, or unexpected behaviors. Combining static and dynamic analysis provides a comprehensive security assessment by covering both code-level defects and real-time operational risks.
Table of Comparison
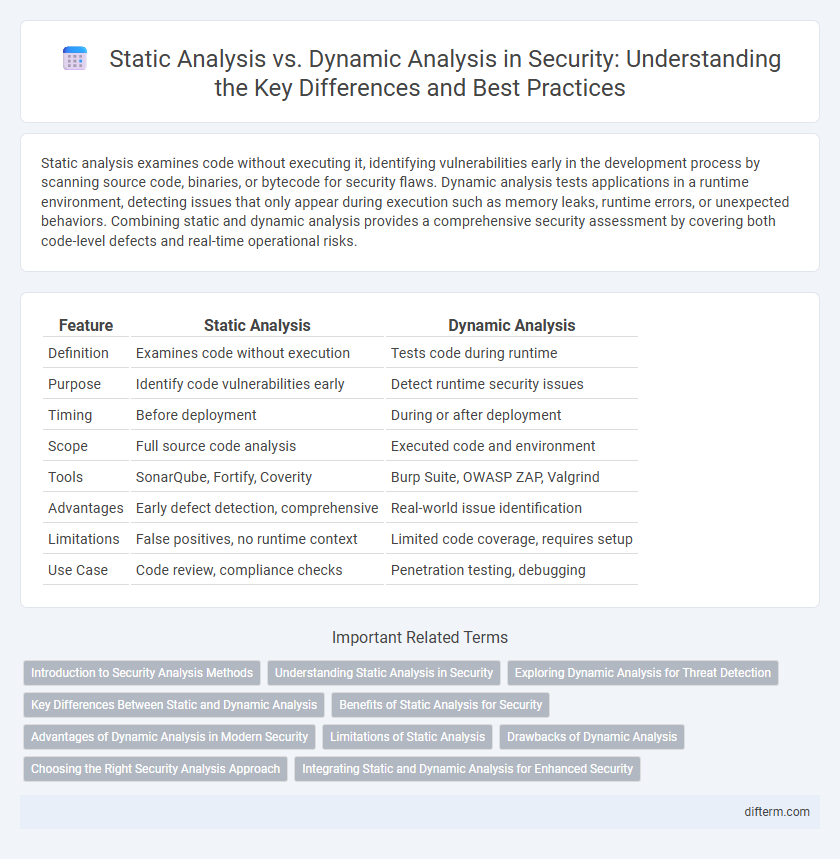
| Feature | Static Analysis | Dynamic Analysis |
|---|---|---|
| Definition | Examines code without execution | Tests code during runtime |
| Purpose | Identify code vulnerabilities early | Detect runtime security issues |
| Timing | Before deployment | During or after deployment |
| Scope | Full source code analysis | Executed code and environment |
| Tools | SonarQube, Fortify, Coverity | Burp Suite, OWASP ZAP, Valgrind |
| Advantages | Early defect detection, comprehensive | Real-world issue identification |
| Limitations | False positives, no runtime context | Limited code coverage, requires setup |
| Use Case | Code review, compliance checks | Penetration testing, debugging |
Introduction to Security Analysis Methods
Static analysis examines source code or binaries without execution to identify vulnerabilities such as coding errors and insecure constructs, enabling early detection during development. Dynamic analysis involves executing the program in a controlled environment, monitoring runtime behavior to uncover issues like memory leaks, runtime exceptions, and security flaws that only manifest during operation. Both methods complement each other to provide comprehensive security assessment by combining code inspection and behavioral evaluation.
Understanding Static Analysis in Security
Static analysis in security involves examining source code or binaries without executing the program, enabling early detection of vulnerabilities such as buffer overflows, injection flaws, and insecure APIs. This method leverages automated tools to identify potential security risks by scanning for coding errors, unsafe constructs, and policy violations, improving code quality before deployment. Static analysis enhances secure software development by providing insights into complex code paths and enforcing compliance with security standards without runtime overhead.
Exploring Dynamic Analysis for Threat Detection
Dynamic analysis offers real-time threat detection by monitoring the execution of applications within controlled environments, enabling the identification of runtime vulnerabilities and malware behaviors that static analysis might miss. It captures system calls, memory usage, and network activity, providing comprehensive visibility into potential security breaches and zero-day exploits. Leveraging sandboxing and behavior profiling, dynamic analysis complements static techniques to strengthen threat intelligence and incident response capabilities.
Key Differences Between Static and Dynamic Analysis
Static analysis examines source code or binaries without execution, identifying vulnerabilities such as syntax errors, insecure coding patterns, and potential security flaws early in the development cycle. Dynamic analysis tests running applications by monitoring system behavior, memory usage, and interactions in real-time to detect runtime errors, memory leaks, and exploit paths. Key differences include static analysis providing early detection with a broad code coverage, while dynamic analysis offers precise bug identification through actual execution context.
Benefits of Static Analysis for Security
Static analysis enhances security by detecting vulnerabilities early in the software development lifecycle, enabling developers to address coding flaws before deployment. It improves code quality through automated, comprehensive scanning of source code, identifying potential risks like SQL injection, buffer overflows, and cross-site scripting. Integrating static analysis into continuous integration pipelines accelerates remediation efforts and reduces the cost of fixing security issues compared to dynamic analysis conducted at runtime.
Advantages of Dynamic Analysis in Modern Security
Dynamic analysis excels in detecting runtime vulnerabilities by monitoring application behavior during execution, enabling identification of threats like buffer overflows, memory leaks, and logic errors that static analysis may miss. It provides real-time insight into how software interacts with system resources and external inputs, enhancing threat detection in complex, modern environments. This approach is particularly effective in uncovering zero-day exploits and runtime anomalies, making it essential for robust modern security strategies.
Limitations of Static Analysis
Static analysis struggles to detect runtime-specific vulnerabilities such as authentication bypasses or logic errors that only manifest during execution. It often generates false positives due to the lack of contextual information about actual program behavior and environment. Furthermore, static analysis tools have difficulty analyzing code with dynamic features, such as reflection or runtime code generation, limiting their effectiveness in complex software systems.
Drawbacks of Dynamic Analysis
Dynamic analysis often suffers from incomplete code coverage, as it only evaluates the program behavior during specific execution paths or inputs, leaving potential vulnerabilities in unexecuted code segments undetected. It requires a runtime environment, which can be resource-intensive and may introduce performance overhead, limiting its scalability in large or complex systems. Furthermore, dynamic analysis can struggle to identify security flaws that only manifest under rare or adversarial conditions, reducing its effectiveness compared to static analysis techniques.
Choosing the Right Security Analysis Approach
Choosing the right security analysis approach depends on the specific needs of the application and the environment it operates in. Static Analysis examines source code for vulnerabilities without execution, ideal for early detection of coding errors and ensuring compliance with secure coding standards, while Dynamic Analysis tests running applications to identify runtime issues like memory leaks and injection flaws. Integrating both methods provides comprehensive coverage, combining the thoroughness of static scanning with the real-time insights of dynamic testing to enhance overall security posture.
Integrating Static and Dynamic Analysis for Enhanced Security
Integrating static analysis and dynamic analysis combines the strengths of both techniques to provide comprehensive security coverage. Static analysis identifies vulnerabilities in source code early, while dynamic analysis detects runtime issues such as memory leaks and authentication flaws. This integration enhances threat detection accuracy, reduces false positives, and improves overall application security by addressing both code-level and execution-time vulnerabilities.
Static Analysis vs Dynamic Analysis Infographic
 difterm.com
difterm.com