A sandbox isolates suspicious files or code within a controlled environment to monitor behavior without risking system integrity, while a honeypot acts as a decoy system designed to attract and trap attackers, gathering intelligence on their tactics. Sandboxes provide dynamic analysis by safely executing potentially malicious software, whereas honeypots collect data by simulating vulnerable targets to detect intrusion attempts. Both tools enhance cybersecurity by offering complementary approaches to threat detection and prevention.
Table of Comparison
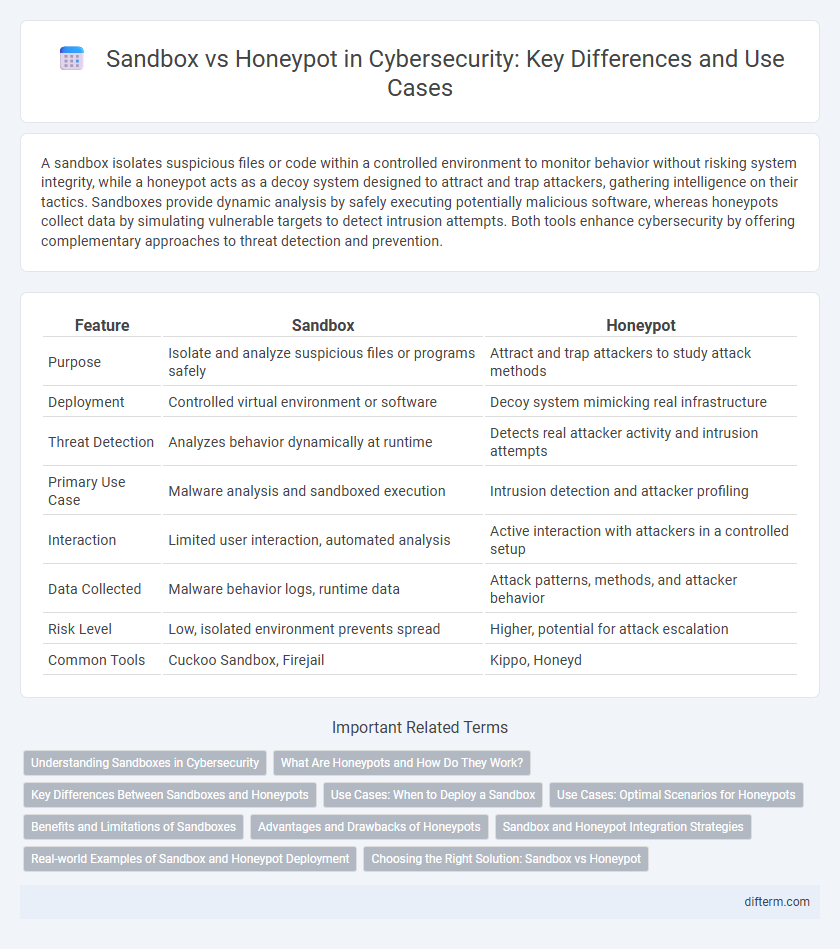
| Feature | Sandbox | Honeypot |
|---|---|---|
| Purpose | Isolate and analyze suspicious files or programs safely | Attract and trap attackers to study attack methods |
| Deployment | Controlled virtual environment or software | Decoy system mimicking real infrastructure |
| Threat Detection | Analyzes behavior dynamically at runtime | Detects real attacker activity and intrusion attempts |
| Primary Use Case | Malware analysis and sandboxed execution | Intrusion detection and attacker profiling |
| Interaction | Limited user interaction, automated analysis | Active interaction with attackers in a controlled setup |
| Data Collected | Malware behavior logs, runtime data | Attack patterns, methods, and attacker behavior |
| Risk Level | Low, isolated environment prevents spread | Higher, potential for attack escalation |
| Common Tools | Cuckoo Sandbox, Firejail | Kippo, Honeyd |
Understanding Sandboxes in Cybersecurity
Sandboxes in cybersecurity provide controlled environments to safely execute and analyze suspicious files or code, isolating them from the main system to prevent potential damage. Unlike honeypots, which deceive attackers by mimicking real systems to gather intelligence, sandboxes primarily focus on dynamic behavior analysis and threat detection. This containment method is essential for identifying zero-day exploits and malware without risking network compromise.
What Are Honeypots and How Do They Work?
Honeypots are cybersecurity tools designed to attract and trap malicious attackers by simulating vulnerable systems or networks, enabling security teams to analyze attack methods and gather intelligence without risking real assets. They operate by mimicking legitimate targets, enticing hackers to interact with the decoy environment, which records attacker behavior and techniques in a controlled setting. This proactive defense mechanism enhances threat detection, incident response, and the development of stronger security measures by providing detailed insights into attacker tactics and vulnerabilities exploited.
Key Differences Between Sandboxes and Honeypots
Sandboxes isolate suspicious programs in a controlled environment to analyze behavior without risking the host system, while honeypots mimic vulnerable systems to attract and study attackers' tactics. Sandboxes focus on dynamic malware analysis by executing code safely, whereas honeypots gather intelligence on real-world attack methods and threat actors. The primary difference lies in sandboxes restricting interaction to prevent escapes, whereas honeypots encourage attacker engagement to collect forensic data.
Use Cases: When to Deploy a Sandbox
Sandboxes are ideal for safely analyzing suspicious files or code in a controlled, isolated environment without risking network security. They enable security teams to observe malicious behavior and detect zero-day threats during malware analysis and incident response. Deploying sandboxes is crucial for proactive threat hunting and verifying the effectiveness of security controls before threats escalate.
Use Cases: Optimal Scenarios for Honeypots
Honeypots are optimal in scenarios requiring early detection of novel threats, as they attract and isolate attackers by mimicking vulnerable systems, enabling detailed threat intelligence collection. They are particularly effective in monitoring insider threats and advanced persistent threats (APTs) by capturing attacker behavior in a controlled environment without alerting the intruder. Organizations leverage honeypots to enhance intrusion detection systems (IDS) and improve security posture through proactive threat hunting and forensic analysis.
Benefits and Limitations of Sandboxes
Sandboxes provide a secure environment to safely analyze and execute unknown or suspicious code, preventing potential harm to live systems by isolating the threat. They enhance malware detection and threat analysis but are limited by resource intensity, potential evasion techniques by advanced malware, and sometimes incomplete replication of the production environment. Effective sandbox deployment strengthens cybersecurity defenses by offering detailed behavior insights, though continuous updates and tuning are necessary to address sophisticated threats.
Advantages and Drawbacks of Honeypots
Honeypots enhance network security by luring attackers into a controlled environment, allowing detailed monitoring and analysis of malicious activities without risking critical assets. They provide valuable threat intelligence and help in detecting novel attack methods, but require significant maintenance and can become targets themselves if improperly isolated. Despite their power in deception, honeypots may generate false positives and consume resources that could be allocated to other security measures.
Sandbox and Honeypot Integration Strategies
Sandbox and honeypot integration strategies enhance cybersecurity by combining proactive and reactive defense mechanisms. Sandboxes analyze suspicious files or code in isolated environments to detect zero-day threats, while honeypots lure attackers to gather intelligence on attack methods and behavior. Integrating these tools enables continuous threat analysis and automated containment, improving incident response and reducing false positives.
Real-world Examples of Sandbox and Honeypot Deployment
Widely used in cybersecurity, Google's VirusTotal utilizes sandbox technology to safely analyze suspicious files by executing them in isolated environments, preventing system compromise while providing detailed behavioral reports. Honeyd, an open-source honeypot framework, emulates multiple virtual hosts with distinct configurations to deceive attackers and gather intelligence on intrusion methods, enhancing network defense strategies. Financial institutions deploy sandboxing to automatically test email attachments for malware, while honeypots are strategically placed within their networks to detect advanced persistent threats, exemplifying real-world application in threat management.
Choosing the Right Solution: Sandbox vs Honeypot
Selecting between a sandbox and a honeypot depends on the security objective: sandboxes isolate and analyze suspicious files or code in a controlled environment to detect malware behavior, while honeypots lure attackers by mimicking vulnerable systems to gather intelligence on attack methods. Organizations focused on proactive threat detection and malware analysis benefit from sandboxes, leveraging dynamic analysis tools and behavior monitoring for real-time insights. Honeypots provide valuable data for threat intelligence and attacker profiling, enhancing network defenses through deception but require careful deployment to avoid exposure risks.
Sandbox vs Honeypot Infographic
 difterm.com
difterm.com