Secure Boot ensures the device boots only using software trusted by the manufacturer by verifying digital signatures during startup, preventing unauthorized code from loading. Measured Boot, on the other hand, records each step of the boot process into a trusted platform module (TPM), enabling attestation of the system's integrity to external parties. Both mechanisms enhance security, with Secure Boot focusing on prevention and Measured Boot enabling detection and verification.
Table of Comparison
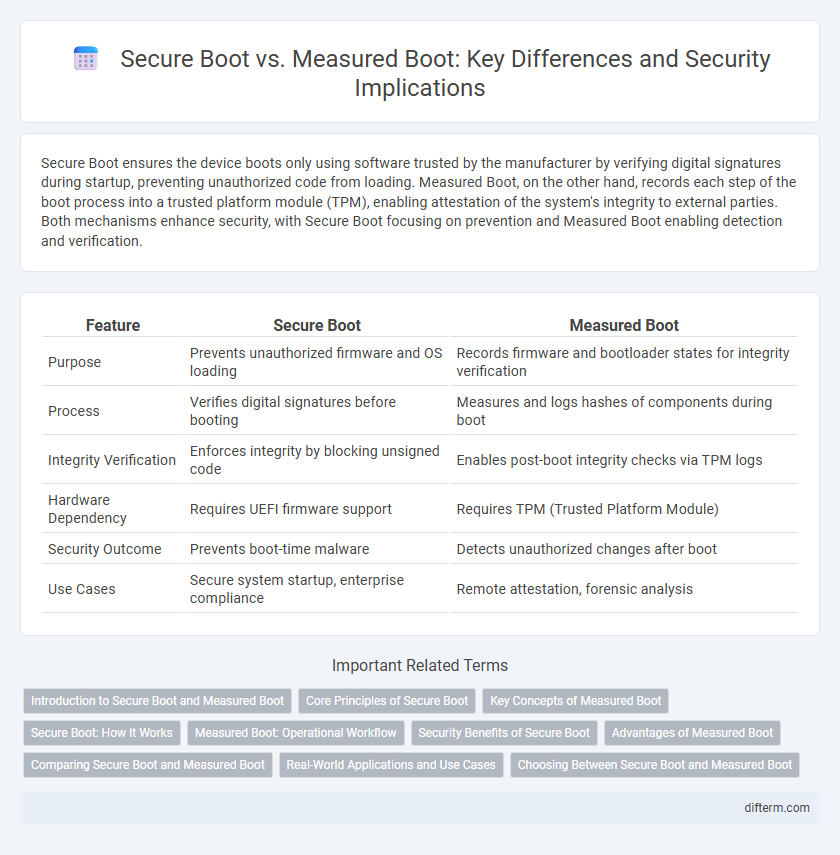
| Feature | Secure Boot | Measured Boot |
|---|---|---|
| Purpose | Prevents unauthorized firmware and OS loading | Records firmware and bootloader states for integrity verification |
| Process | Verifies digital signatures before booting | Measures and logs hashes of components during boot |
| Integrity Verification | Enforces integrity by blocking unsigned code | Enables post-boot integrity checks via TPM logs |
| Hardware Dependency | Requires UEFI firmware support | Requires TPM (Trusted Platform Module) |
| Security Outcome | Prevents boot-time malware | Detects unauthorized changes after boot |
| Use Cases | Secure system startup, enterprise compliance | Remote attestation, forensic analysis |
Introduction to Secure Boot and Measured Boot
Secure Boot is a security standard that ensures a device boots using only trusted software by verifying digital signatures of the bootloader and firmware components. Measured Boot records cryptographic measurements of each boot phase into a Trusted Platform Module (TPM), enabling remote attestation and integrity verification. Both technologies provide complementary protections: Secure Boot prevents unauthorized code execution during startup, while Measured Boot enables detection of boot-time tampering.
Core Principles of Secure Boot
Secure Boot ensures system integrity by allowing only digitally signed and verified firmware and software components to execute during startup, preventing unauthorized code from running. It relies on a hardware-rooted trust chain anchored in immutable firmware, such as a Trusted Platform Module (TPM) or a secure processor, to validate each stage of the boot process. This mechanism blocks malicious bootloaders and rootkits, enhancing device security by enforcing strict authentication before operating system load.
Key Concepts of Measured Boot
Measured Boot enhances system security by recording cryptographic hashes of each boot component, allowing verification of firmware and software integrity before execution. It leverages a Trusted Platform Module (TPM) to securely store these measurements, enabling remote attestation and detection of unauthorized modifications. This process ensures a tamper-evident boot sequence, complementing Secure Boot's signature verification by providing detailed boot state evidence.
Secure Boot: How It Works
Secure Boot ensures device integrity by verifying the digital signature of firmware and bootloaders against a trusted database stored in the platform's firmware. It prevents unauthorized or malicious software from loading during the startup process by allowing only signed and trusted code to execute. This cryptographic verification process helps protect against rootkits, bootkits, and low-level malware attacks targeting the boot sequence.
Measured Boot: Operational Workflow
Measured Boot enhances device security by creating a cryptographic hash of each firmware and software component during startup, which is then stored in a Trusted Platform Module (TPM) for verification. This operational workflow ensures the integrity of the boot process by comparing current measurements against known good values, detecting unauthorized modifications or tampering before the operating system loads. By maintaining a trusted record of boot components, Measured Boot supports secure attestation and enables systems to respond to integrity violations in real time.
Security Benefits of Secure Boot
Secure Boot enhances device security by ensuring that only trusted, signed firmware and software components load during the startup process, preventing unauthorized code execution and rootkit infections. It verifies the digital signatures of bootloaders and operating systems, blocking malicious or tampered software from running. This foundational integrity check protects systems against persistent malware attacks and firmware-level compromises, significantly improving overall cybersecurity posture.
Advantages of Measured Boot
Measured Boot enhances system security by creating a verifiable record of the boot process, enabling detection of unauthorized changes or malware that bypass Secure Boot's signature verification. It offers continuous attestation by measuring each component before execution, facilitating remote validation and stronger trust in system integrity. Unlike Secure Boot, Measured Boot supports detailed forensic analysis and dynamic platform integrity assessment, improving overall threat response capabilities.
Comparing Secure Boot and Measured Boot
Secure Boot verifies the authenticity of firmware and bootloaders by checking digital signatures during the startup process, preventing unauthorized code execution. Measured Boot records cryptographic hashes of each boot component into a Trusted Platform Module (TPM) to create a verifiable log for attestation and forensic analysis. While Secure Boot enforces integrity at boot time, Measured Boot provides a continuous chain of trust enabling remote verification of system integrity.
Real-World Applications and Use Cases
Secure Boot ensures that a device boots exclusively with software authorized by the Original Equipment Manufacturer, preventing unauthorized OS loading and firmware tampering, commonly employed in enterprise laptops and mobile devices to hinder malware attacks. Measured Boot records each boot component's hash value into a Trusted Platform Module (TPM), enabling system administrators to detect unauthorized modifications through remote attestation, frequently used in cloud servers and critical infrastructure systems requiring integrity verification. Both technologies complement each other in environments demanding robust security: Secure Boot enforcing static authenticity, while Measured Boot provides dynamic visibility into the boot process for continuous compliance monitoring.
Choosing Between Secure Boot and Measured Boot
Choosing between Secure Boot and Measured Boot depends on the security goals and threat models of the system. Secure Boot ensures that only trusted firmware and software load during startup by verifying digital signatures, preventing unauthorized code execution from the earliest boot stages. Measured Boot complements this by recording cryptographic measurements of each boot component, enabling remote attestation and integrity verification without necessarily blocking untrusted software from running.
Secure Boot vs Measured Boot Infographic
 difterm.com
difterm.com