Social engineering exploits human psychology to manipulate individuals into divulging confidential information, bypassing technical security measures without physical access. Physical intrusion involves unauthorized entry into secure locations to steal data or assets, relying on stealth and physical barriers rather than psychological tactics. Both methods pose significant threats, requiring integrated security protocols that address human behavior and physical safeguards.
Table of Comparison
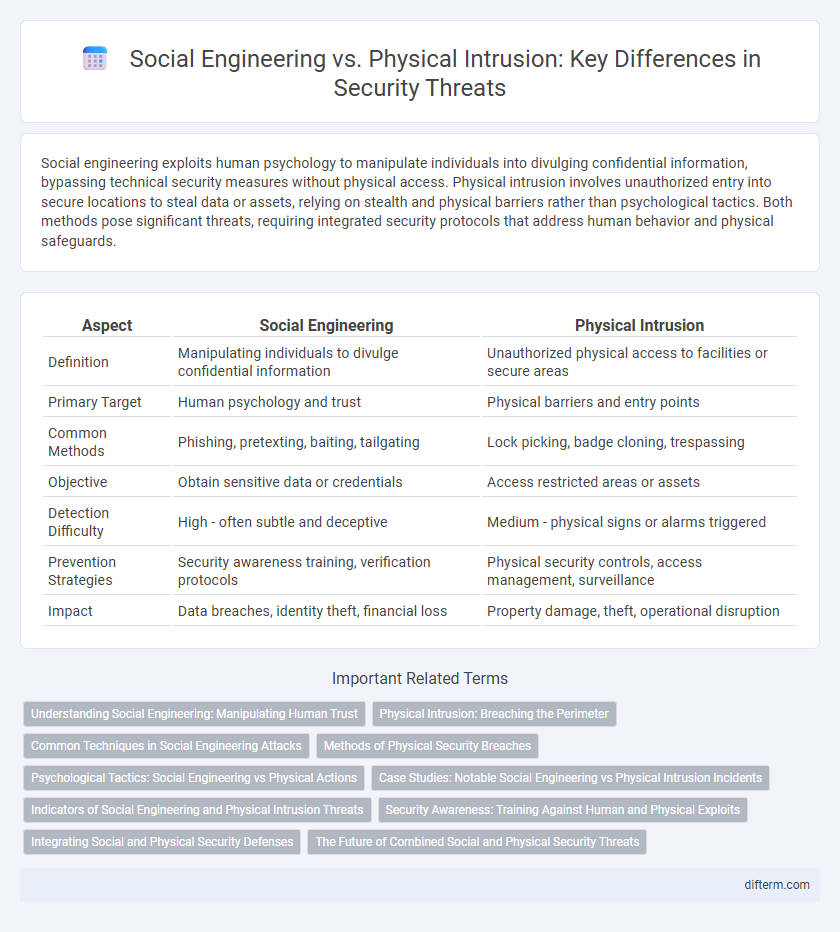
| Aspect | Social Engineering | Physical Intrusion |
|---|---|---|
| Definition | Manipulating individuals to divulge confidential information | Unauthorized physical access to facilities or secure areas |
| Primary Target | Human psychology and trust | Physical barriers and entry points |
| Common Methods | Phishing, pretexting, baiting, tailgating | Lock picking, badge cloning, trespassing |
| Objective | Obtain sensitive data or credentials | Access restricted areas or assets |
| Detection Difficulty | High - often subtle and deceptive | Medium - physical signs or alarms triggered |
| Prevention Strategies | Security awareness training, verification protocols | Physical security controls, access management, surveillance |
| Impact | Data breaches, identity theft, financial loss | Property damage, theft, operational disruption |
Understanding Social Engineering: Manipulating Human Trust
Social engineering exploits human psychology to bypass traditional security measures by manipulating trust, often through tactics like phishing, pretexting, and baiting. Attackers impersonate trusted individuals or create convincing scenarios to extract sensitive information or gain unauthorized access. Understanding these manipulation techniques is crucial for developing effective training programs and implementing multi-layered security protocols to mitigate social engineering risks.
Physical Intrusion: Breaching the Perimeter
Physical intrusion involves breaching the perimeter of a secure facility by exploiting weaknesses in physical barriers such as fences, doors, and access control systems. Techniques include lock picking, tailgating, and bypassing security checkpoints, which allow unauthorized individuals to gain entry and potentially compromise sensitive assets. Implementing layered security measures like surveillance cameras, biometric access controls, and alarm systems is essential to deter and detect perimeter breaches effectively.
Common Techniques in Social Engineering Attacks
Phishing emails, pretexting, and baiting are common techniques used in social engineering attacks to manipulate individuals into revealing sensitive information or granting unauthorized access. Attackers often exploit human psychology by creating a sense of urgency or trust to bypass digital and physical security measures. These methods pose significant risks as they target the weakest link in security: human behavior.
Methods of Physical Security Breaches
Physical security breaches commonly involve methods such as tailgating, where unauthorized individuals follow authorized personnel into secured areas, and lock picking or bypassing access controls to gain entry. Intruders may also exploit weaknesses in surveillance systems or employ covert entry techniques like badge cloning and exploiting unattended doors. These methods highlight the importance of robust physical barriers, employee vigilance, and integrated security technologies to prevent unauthorized access.
Psychological Tactics: Social Engineering vs Physical Actions
Social engineering exploits psychological manipulation techniques such as pretexting, phishing, and impersonation to deceive individuals into divulging sensitive information or granting access. Physical intrusion relies on tangible actions like tailgating, lock picking, and unauthorized entry to breach secure environments. Understanding the distinction in tactics emphasizes the importance of cybersecurity training alongside physical security measures.
Case Studies: Notable Social Engineering vs Physical Intrusion Incidents
Notable social engineering incidents include the 2011 RSA SecureID breach, where attackers manipulated employees through phishing to access sensitive authentication data. Physical intrusion cases, like the 2013 Target data breach, saw criminals bypass physical security controls by infiltrating HVAC vendors, leading to the theft of 40 million customer credit card records. These incidents highlight the critical importance of integrating both cyber and physical security measures to defend against multifaceted threats.
Indicators of Social Engineering and Physical Intrusion Threats
Indicators of social engineering threats often include unsolicited requests for sensitive information, unusual urgency in communications, and inconsistencies in the caller or sender's identity verification. Physical intrusion threats are typically identified by unauthorized access attempts, tampering with locks or security devices, and presence of unfamiliar individuals in restricted areas. Monitoring these indicators through employee training, access logs, and surveillance systems enhances detection and prevention strategies.
Security Awareness: Training Against Human and Physical Exploits
Security awareness training is critical in defending organizations against social engineering and physical intrusion threats by educating employees about recognizing manipulation tactics and unauthorized access attempts. Effective programs emphasize identifying phishing schemes, tailgating, and pretexting while reinforcing physical security protocols like badge usage and access control. Integrating scenario-based simulations enhances employee preparedness, reducing human error vulnerabilities linked to cyber and physical security breaches.
Integrating Social and Physical Security Defenses
Integrating social and physical security defenses enhances protection by addressing both human manipulation and unauthorized access risks simultaneously. Combining employee training on social engineering tactics with advanced physical controls like biometric access systems reduces vulnerabilities exploited by attackers. Coordinated security protocols and real-time monitoring ensure comprehensive threat mitigation across digital and physical domains.
The Future of Combined Social and Physical Security Threats
Emerging threats increasingly blend social engineering tactics with physical intrusion methods, challenging traditional security frameworks. Attackers exploit psychological manipulation to gain trust or access before executing physical breaches, amplifying risk across corporate and critical infrastructure environments. Integrating advanced biometric systems with behavioral analytics offers a proactive defense against this evolving hybrid threat landscape.
Social Engineering vs Physical Intrusion Infographic
 difterm.com
difterm.com