A nonce and an initialization vector (IV) both serve as unique values used to ensure security in cryptographic operations by preventing replay attacks and maintaining data confidentiality. While a nonce is typically a number used once per encryption to guarantee uniqueness without requiring secrecy, an IV is often random or pseudo-random and used to initialize the encryption process to produce distinct ciphertexts from identical plaintexts. Proper implementation of nonces or IVs is critical in securing pet protection systems by safeguarding communication channels and preventing unauthorized data access.
Table of Comparison
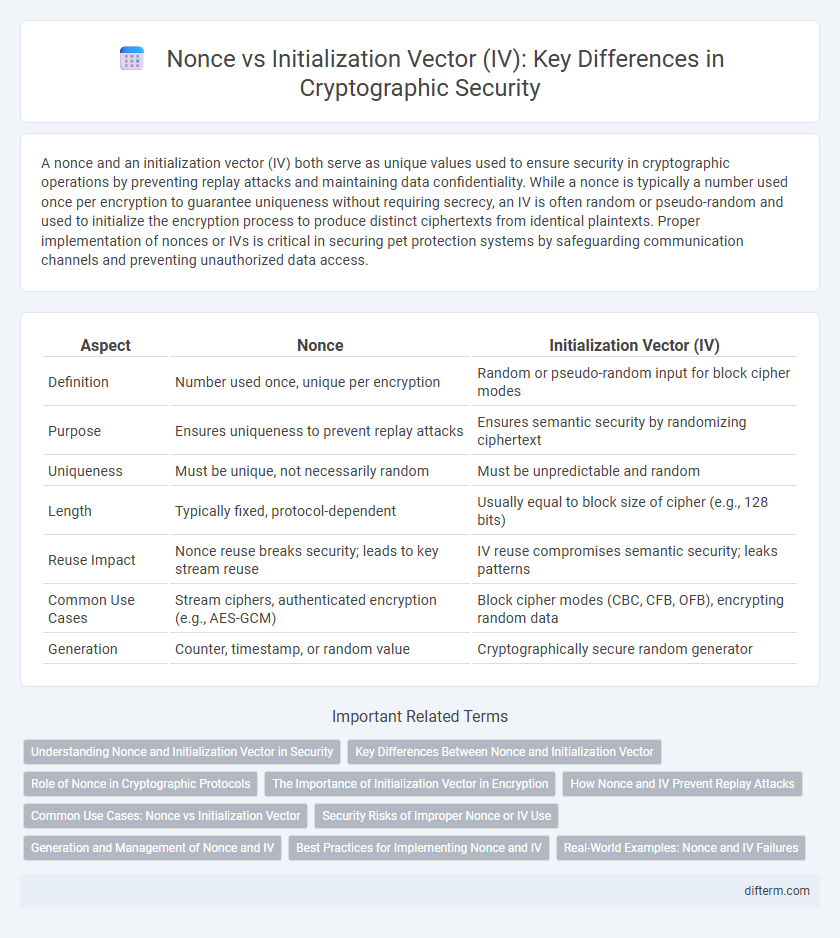
| Aspect | Nonce | Initialization Vector (IV) |
|---|---|---|
| Definition | Number used once, unique per encryption | Random or pseudo-random input for block cipher modes |
| Purpose | Ensures uniqueness to prevent replay attacks | Ensures semantic security by randomizing ciphertext |
| Uniqueness | Must be unique, not necessarily random | Must be unpredictable and random |
| Length | Typically fixed, protocol-dependent | Usually equal to block size of cipher (e.g., 128 bits) |
| Reuse Impact | Nonce reuse breaks security; leads to key stream reuse | IV reuse compromises semantic security; leaks patterns |
| Common Use Cases | Stream ciphers, authenticated encryption (e.g., AES-GCM) | Block cipher modes (CBC, CFB, OFB), encrypting random data |
| Generation | Counter, timestamp, or random value | Cryptographically secure random generator |
Understanding Nonce and Initialization Vector in Security
Nonce and Initialization Vector (IV) are critical components in cryptographic security to ensure data confidentiality and prevent replay attacks. A nonce is a unique, arbitrary number used only once per encryption session, typically ensuring message freshness and preventing reuse of keys, while an IV is a random or pseudo-random value that serves as an initial input to encryption algorithms like AES in CBC mode, ensuring distinct ciphertext outputs for identical plaintexts. Proper implementation of nonces and IVs strengthens resistance against cryptanalysis by introducing randomness and uniqueness in encryption operations.
Key Differences Between Nonce and Initialization Vector
A nonce is a unique, one-time-use value primarily designed to ensure that cryptographic operations like encryption and authentication produce distinct outputs, preventing replay attacks. An initialization vector (IV) is a random or pseudo-random value used to initialize encryption algorithms, especially block ciphers in modes like CBC or CTR, to ensure that identical plaintext blocks yield different ciphertexts. The key difference lies in nonce being typically a counter or sequentially incremented value ensuring uniqueness without necessarily being random, whereas an IV must be random or unpredictable to maintain semantic security in encryption schemes.
Role of Nonce in Cryptographic Protocols
A nonce plays a critical role in cryptographic protocols by providing a unique, random value for each encryption operation to prevent replay attacks and ensure message freshness. Unlike initialization vectors (IVs), nonces are often used in protocols that require synchronization between communicating parties, such as in authentication or key exchange processes. Proper implementation of nonces enhances security by guaranteeing that cryptographic operations yield distinct ciphertexts even when using the same key.
The Importance of Initialization Vector in Encryption
The initialization vector (IV) is crucial in encryption as it ensures that identical plaintext blocks produce unique ciphertext outputs, preventing pattern recognition and enhancing data confidentiality. Unlike nonces, which are typically used once per key to guarantee uniqueness, IVs introduce randomness and are essential for modes like CBC and CFB to maintain semantic security. Proper generation and management of IVs significantly reduce vulnerabilities to replay attacks and ciphertext manipulation, reinforcing robust cryptographic practices.
How Nonce and IV Prevent Replay Attacks
Nonces and initialization vectors (IVs) prevent replay attacks by ensuring that each encrypted message transaction is unique and cannot be reused maliciously. Nonces provide a one-time, unique value that is combined with the encryption key to eliminate message duplication, while IVs add randomness to encryption processes in block ciphers, preventing patterns in ciphertext that could be exploited. Both mechanisms disrupt attacker attempts to capture and resend valid data packets, maintaining message integrity and confidentiality in secure communications.
Common Use Cases: Nonce vs Initialization Vector
Nonces are commonly used in cryptographic protocols to ensure uniqueness in message encryption, preventing replay attacks by providing a one-time value per transaction. Initialization vectors (IVs) are primarily employed in symmetric encryption algorithms like AES CBC to randomize ciphertext output, ensuring different ciphertexts from identical plaintext inputs under the same key. While nonces emphasize uniqueness and freshness in nonce-based authenticated encryption schemes (e.g., AES-GCM), IVs focus on randomness and unpredictability during block cipher modes where IV reuse can compromise security.
Security Risks of Improper Nonce or IV Use
Improper use of nonces or initialization vectors (IVs) can lead to severe security vulnerabilities, such as replay attacks, ciphertext reuse, and compromised encryption integrity. Reusing a nonce or IV with the same key enables attackers to uncover plaintext data or encryption keys through known-plaintext or ciphertext-only attacks. Ensuring unique, unpredictable nonces and IVs is critical for maintaining confidentiality and preventing cryptographic failures in protocols like AES-GCM and ChaCha20-Poly1305.
Generation and Management of Nonce and IV
Nonces are typically generated to be unique and unpredictable for each cryptographic operation, ensuring that the same nonce is never reused with the same key, which is critical to maintaining security. Initialization vectors (IVs) are also generated uniquely but may follow specific protocol constraints, such as being random or pseudo-random values that align with the encryption mode requirements like CBC or CTR. Proper management involves securely storing or transmitting nonces and IVs alongside ciphertext to prevent replay attacks and ensure successful decryption while maintaining confidentiality and integrity.
Best Practices for Implementing Nonce and IV
Best practices for implementing nonce and initialization vector (IV) in security protocols emphasize ensuring uniqueness and unpredictability to prevent replay attacks and maintain cryptographic strength. Nonces must never repeat within the same key context, whereas IVs should be random or pseudo-random and ideally unpredictable for each encryption operation. Proper management of nonce and IV generation, combined with secure key handling, enhances confidentiality and integrity in encryption schemes like AES-GCM and ChaCha20-Poly1305.
Real-World Examples: Nonce and IV Failures
Real-world security breaches often stem from the improper reuse of nonces or initialization vectors (IVs), leading to catastrophic encryption failures such as in the infamous Debian OpenSSL bug of 2008, where predictable IVs compromised key generation. In the Wi-Fi WPA2 protocol, the reuse or predictable generation of nonces facilitates replay attacks and key recovery, exploiting vulnerabilities in CCMP encryption. These incidents underscore the critical importance of unique, unpredictable nonces and IVs in cryptographic protocols to ensure robust data confidentiality and integrity.
nonce vs initialization vector Infographic
 difterm.com
difterm.com