Single Sign-On (SSO) allows users to access multiple applications with one set of credentials, enhancing user convenience and reducing password fatigue. Federated Identity extends this concept by enabling users to use their credentials across different organizations or domains, facilitating seamless access in distributed environments. Both methods improve security by centralizing authentication, but federated identity supports broader interoperability and cross-domain trust.
Table of Comparison
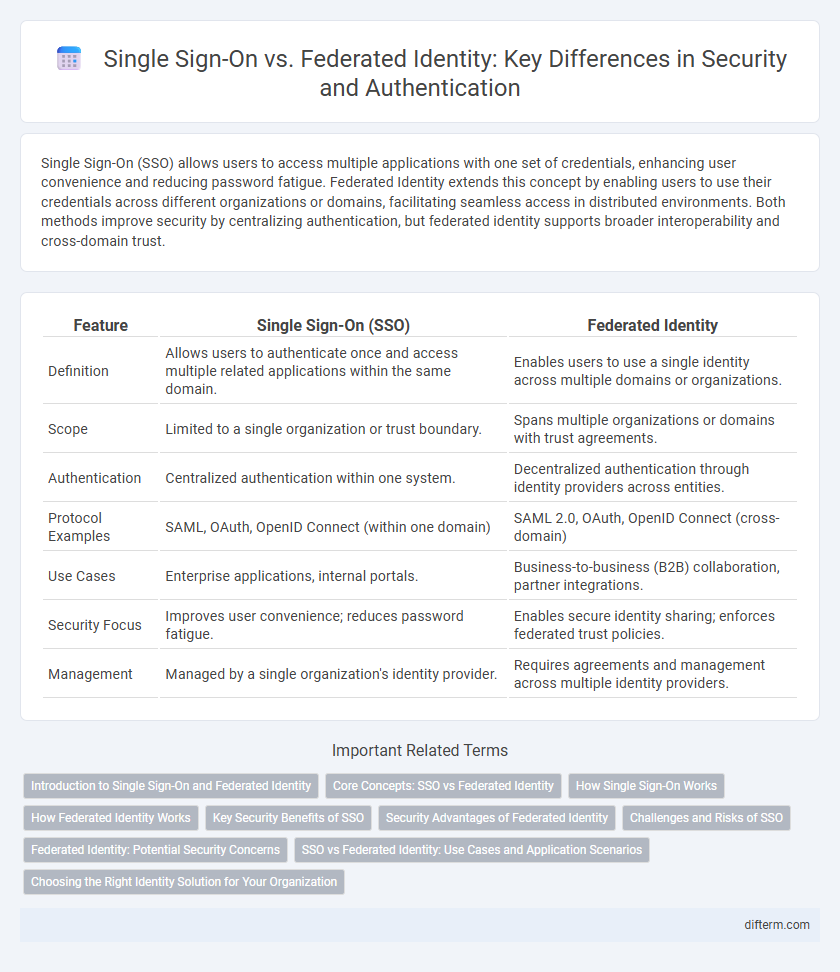
| Feature | Single Sign-On (SSO) | Federated Identity |
|---|---|---|
| Definition | Allows users to authenticate once and access multiple related applications within the same domain. | Enables users to use a single identity across multiple domains or organizations. |
| Scope | Limited to a single organization or trust boundary. | Spans multiple organizations or domains with trust agreements. |
| Authentication | Centralized authentication within one system. | Decentralized authentication through identity providers across entities. |
| Protocol Examples | SAML, OAuth, OpenID Connect (within one domain) | SAML 2.0, OAuth, OpenID Connect (cross-domain) |
| Use Cases | Enterprise applications, internal portals. | Business-to-business (B2B) collaboration, partner integrations. |
| Security Focus | Improves user convenience; reduces password fatigue. | Enables secure identity sharing; enforces federated trust policies. |
| Management | Managed by a single organization's identity provider. | Requires agreements and management across multiple identity providers. |
Introduction to Single Sign-On and Federated Identity
Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials, streamlining authentication and improving security by reducing password fatigue. Federated Identity extends this concept by allowing users to use a single digital identity across multiple organizations, promoting interoperability and secure data sharing among trusted entities. Both technologies enhance user experience and security frameworks by simplifying access management and minimizing credential exposure.
Core Concepts: SSO vs Federated Identity
Single Sign-On (SSO) allows users to access multiple applications with one set of login credentials managed centrally within a single organization. Federated Identity extends this concept by enabling identity sharing across different organizations through trust relationships and standardized protocols like SAML or OAuth. While SSO improves user convenience within a domain, Federated Identity enhances cross-domain authentication and access control for integrated services.
How Single Sign-On Works
Single Sign-On (SSO) works by allowing users to authenticate once through an identity provider (IdP) and gain access to multiple connected applications without re-entering credentials. It leverages protocols such as SAML, OAuth, or OpenID Connect to securely exchange authentication tokens between the IdP and service providers (SPs). This streamlines user access management while reducing password fatigue and improving overall security posture in enterprise environments.
How Federated Identity Works
Federated Identity enables users to access multiple systems using a single digital identity managed by a trusted identity provider, facilitating seamless authentication across organizational boundaries. It relies on standardized protocols such as SAML, OAuth, or OpenID Connect to securely exchange authentication and authorization data between participating domains. This approach enhances security by reducing password proliferation and centralizing access control while maintaining user privacy through token-based verification.
Key Security Benefits of SSO
Single Sign-On (SSO) enhances security by reducing password fatigue, minimizing the risk of weak or reused passwords across multiple applications. Centralized authentication strengthens access control and simplifies monitoring, enabling quicker detection of suspicious activities. Improved user experience decreases password reset requests, lowering help desk costs and reducing potential security vulnerabilities.
Security Advantages of Federated Identity
Federated Identity enhances security by enabling centralized authentication across multiple organizations, reducing password fatigue and minimizing phishing risks through consistent credential management. It supports multi-factor authentication (MFA) integration at the identity provider level, ensuring robust user verification before access is granted. This approach also improves auditability and compliance by providing unified access logs across federated systems, enhancing threat detection and response capabilities.
Challenges and Risks of SSO
Single Sign-On (SSO) centralizes user authentication, which increases the risk of a single point of failure that can lead to unauthorized access if compromised. Challenges include managing secure token exchanges, ensuring robust password policies, and detecting credential stuffing or phishing attacks targeting SSO credentials. Organizations must also address risks related to session hijacking and inadequate logout mechanisms to maintain secure and seamless user access.
Federated Identity: Potential Security Concerns
Federated Identity introduces potential security concerns such as token interception, where attackers may capture authentication tokens during transmission, leading to unauthorized access. The reliance on third-party identity providers also increases the risk of a single point of failure, where a compromised or misconfigured provider can jeopardize multiple connected services. Furthermore, inadequate implementation of trust relationships and inconsistent security policies across federated partners can expose vulnerabilities, making robust federation protocols and continuous monitoring essential.
SSO vs Federated Identity: Use Cases and Application Scenarios
Single Sign-On (SSO) is ideal for organizations requiring streamlined access to multiple internal applications within a single domain, enhancing user convenience and reducing password fatigue. Federated Identity is suited for scenarios involving cross-organizational collaboration, enabling users to authenticate across different domains or enterprises without managing multiple credentials. Use cases for SSO include corporate intranets and cloud service suites, while federated identity is prevalent in partnerships, mergers, and SaaS integrations that span distinct organizations.
Choosing the Right Identity Solution for Your Organization
Selecting the optimal identity solution hinges on your organization's security requirements, scale, and user management complexity. Single Sign-On (SSO) centralizes authentication within one domain, simplifying access while reducing password fatigue and minimizing attack vectors. Federated Identity extends trust across multiple domains, enabling seamless, secure collaboration with external partners through standardized protocols like SAML or OAuth, essential for organizations with diverse partnerships or multi-cloud environments.
Single Sign-On vs Federated Identity Infographic
 difterm.com
difterm.com