Risk refers to the likelihood and potential impact of a security threat affecting a pet, while hazard denotes any source or condition that could cause harm. Understanding hazards helps identify possible dangers in the environment, whereas assessing risk determines the probability and severity of those dangers manifesting. Effective pet security strategies rely on minimizing risks by controlling or eliminating hazards.
Table of Comparison
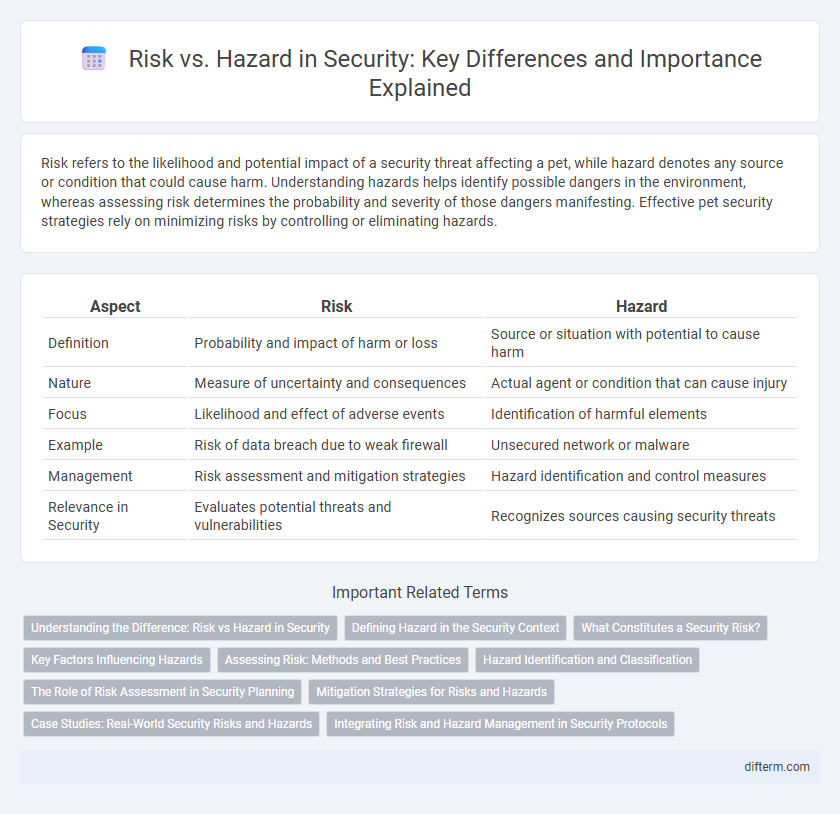
| Aspect | Risk | Hazard |
|---|---|---|
| Definition | Probability and impact of harm or loss | Source or situation with potential to cause harm |
| Nature | Measure of uncertainty and consequences | Actual agent or condition that can cause injury |
| Focus | Likelihood and effect of adverse events | Identification of harmful elements |
| Example | Risk of data breach due to weak firewall | Unsecured network or malware |
| Management | Risk assessment and mitigation strategies | Hazard identification and control measures |
| Relevance in Security | Evaluates potential threats and vulnerabilities | Recognizes sources causing security threats |
Understanding the Difference: Risk vs Hazard in Security
In security, a hazard refers to any potential source of harm or adverse effect, such as vulnerabilities in a system or physical threats like unauthorized access points. Risk, on the other hand, quantifies the likelihood and impact of these hazards causing actual damage or loss, factoring in existing controls and mitigation measures. Understanding the distinction between risk and hazard is essential for implementing effective security strategies that prioritize resources and reduce potential threats.
Defining Hazard in the Security Context
A hazard in the security context refers to any source of potential harm or adverse effect that can compromise the safety, integrity, or availability of assets, systems, or individuals. Unlike risk, which assesses the likelihood and impact of threats exploiting vulnerabilities, a hazard specifically identifies conditions or situations that can cause damage or danger. Understanding hazards is crucial for implementing targeted security controls and preventive measures to mitigate potential incidents.
What Constitutes a Security Risk?
A security risk constitutes any potential threat that can exploit vulnerabilities to cause harm, including unauthorized access, data breaches, or system failures. Unlike hazards, which are inherent dangers, security risks are tied to the likelihood of an attack and the impact it can have on assets or information. Effective risk assessment involves identifying, analyzing, and mitigating threats that could compromise confidentiality, integrity, or availability of critical systems.
Key Factors Influencing Hazards
Key factors influencing hazards include environmental conditions, which can exacerbate the severity and likelihood of hazardous events, and the presence of vulnerable populations that increase exposure risks. Operational processes and equipment integrity play critical roles in hazard identification, as failures or lapses often trigger hazardous situations. Regulatory compliance and workplace safety culture significantly impact hazard management by shaping protocols that mitigate potential threats.
Assessing Risk: Methods and Best Practices
Assessing risk involves identifying potential hazards and evaluating the likelihood and impact of adverse events using methods like qualitative analysis, quantitative analysis, and risk matrix scoring. Best practices include conducting thorough hazard identification, applying probabilistic risk assessment (PRA), and continuously updating risk profiles based on new data and environmental changes. Effective risk assessment integrates stakeholder input and employs software tools to enhance accuracy, thereby supporting informed decision-making in security management.
Hazard Identification and Classification
Hazard identification involves systematically recognizing potential sources of harm in the workplace, such as chemical exposures, electrical faults, or ergonomic issues. Accurate classification of hazards into categories like physical, chemical, biological, and psychosocial enables targeted risk control measures and prioritization. Implementing standardized hazard classification frameworks ensures consistent communication and compliance with safety regulations, ultimately reducing incident rates.
The Role of Risk Assessment in Security Planning
Risk assessment plays a critical role in security planning by systematically identifying potential threats and evaluating the likelihood and impact of security hazards. Differentiating between risk and hazard allows security professionals to prioritize resources effectively, targeting vulnerabilities that pose the greatest risk to assets and personnel. Implementing comprehensive risk assessment frameworks enhances decision-making processes, ensuring proactive mitigation strategies and continuous monitoring in dynamic threat environments.
Mitigation Strategies for Risks and Hazards
Mitigation strategies for risks involve systematic risk assessments, implementation of controls, and continuous monitoring to reduce the likelihood and impact of potential threats. Hazard mitigation focuses on eliminating or minimizing exposure through engineering controls, safety protocols, and hazard-specific training. Both approaches prioritize proactive measures to safeguard personnel and assets, ensuring compliance with regulatory standards and enhancing overall organizational resilience.
Case Studies: Real-World Security Risks and Hazards
Case studies in security reveal that risks often encompass the probability of cyber attacks disrupting operations, while hazards refer to inherent vulnerabilities like outdated software. For instance, the 2017 Equifax breach demonstrated how unpatched systems (hazards) escalated into massive data theft (risk realization). Analyzing such incidents highlights the critical need for proactive vulnerability management and risk assessment frameworks in organizational security protocols.
Integrating Risk and Hazard Management in Security Protocols
Integrating risk and hazard management within security protocols enhances threat detection and mitigation by systematically identifying potential hazards and assessing associated risks. This approach aligns hazard identification with risk analysis, enabling security teams to prioritize vulnerabilities based on impact and likelihood. Embedding these integrated processes into security frameworks ensures proactive threat response and compliance with safety standards.
Risk vs Hazard Infographic
 difterm.com
difterm.com