Salt and pepper are both techniques used in password hashing to enhance security by making hashed passwords more resistant to attacks. Salt involves adding a unique, random value to each password before hashing, ensuring that identical passwords have different hashes, while pepper is a secret value added uniformly to all passwords, stored separately to protect against rainbow table attacks. Combining salt and pepper provides robust defense by mitigating risks from hash collisions and unauthorized access to stored hashes.
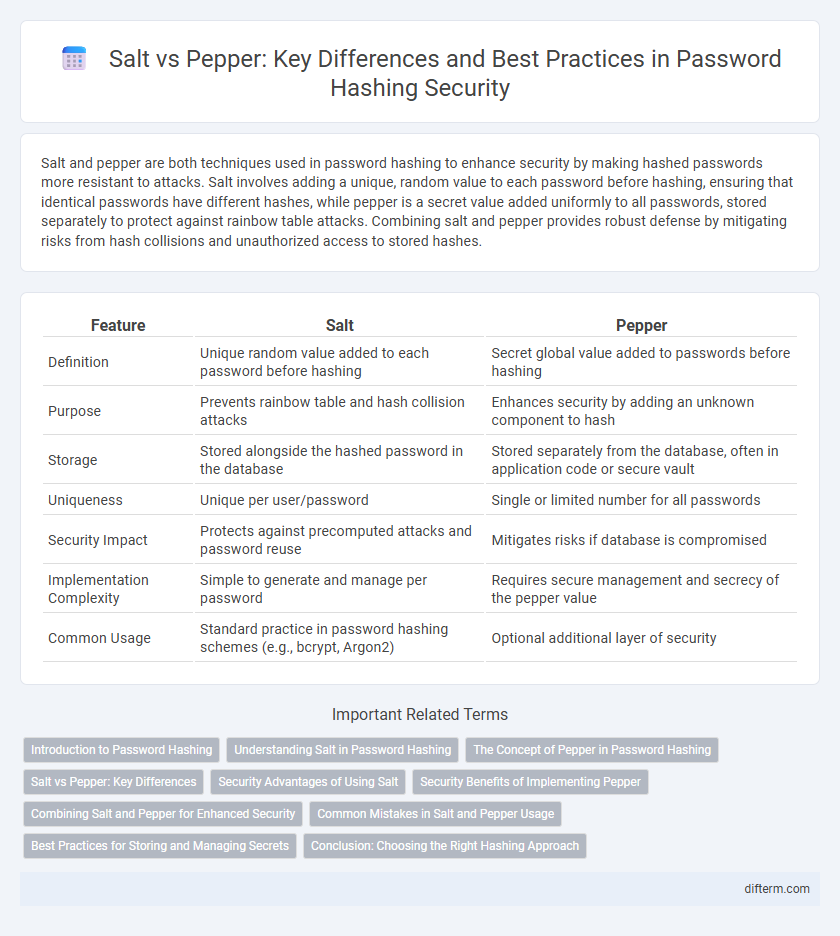
Table of Comparison
| Feature | Salt | Pepper |
|---|---|---|
| Definition | Unique random value added to each password before hashing | Secret global value added to passwords before hashing |
| Purpose | Prevents rainbow table and hash collision attacks | Enhances security by adding an unknown component to hash |
| Storage | Stored alongside the hashed password in the database | Stored separately from the database, often in application code or secure vault |
| Uniqueness | Unique per user/password | Single or limited number for all passwords |
| Security Impact | Protects against precomputed attacks and password reuse | Mitigates risks if database is compromised |
| Implementation Complexity | Simple to generate and manage per password | Requires secure management and secrecy of the pepper value |
| Common Usage | Standard practice in password hashing schemes (e.g., bcrypt, Argon2) | Optional additional layer of security |
Introduction to Password Hashing
Password hashing is a critical security measure that transforms plain-text passwords into fixed-length strings using cryptographic algorithms to protect user credentials from unauthorized access. Salt involves adding a unique, random value to each password before hashing to prevent attacks like rainbow table lookups by ensuring identical passwords have different hash outputs. Pepper is a secret value, kept server-side, integrated into the hashing process to add an extra layer of security against brute-force attacks even if the database is compromised.
Understanding Salt in Password Hashing
Salt in password hashing is a unique, randomly generated value added to each password before hashing to ensure that identical passwords result in different hashes, enhancing security against rainbow table attacks. It prevents attackers from identifying users with the same password and protects against precomputed hash attacks by introducing unpredictability. Proper implementation of salt involves generating a new salt for every password, storing it securely alongside the hash, and using strong cryptographic hash functions such as bcrypt or Argon2.
The Concept of Pepper in Password Hashing
Pepper in password hashing is a secret value added to passwords before hashing, enhancing security by being stored separately from the hashed passwords, unlike salt which is unique per user and stored with the hash. It mitigates risks from database breaches by preventing attackers from using precomputed hash tables or brute force attacks, requiring access to both the pepper and the hashed passwords to crack credentials. Common implementations involve a fixed pepper value kept securely in application code or environment variables, strengthening overall password protection frameworks.
Salt vs Pepper: Key Differences
Salt in password hashing is a unique, random value stored alongside the hash to ensure each password hash is distinct, preventing rainbow table attacks. Pepper is a secret key kept separate from the database, added to the password before hashing to provide an additional security layer against hash extraction. The key difference lies in salt being public and per-password, while pepper is secret and typically consistent across all passwords.
Security Advantages of Using Salt
Salt enhances password security by adding a unique, random value to each password before hashing, which prevents attackers from using precomputed rainbow tables for reverse engineering. It ensures that identical passwords result in different hashes, significantly strengthening defense against brute-force and collision attacks. Salting also complicates the process of cracking large sets of passwords, making it an essential component in secure authentication systems.
Security Benefits of Implementing Pepper
Implementing pepper in password hashing significantly enhances security by adding a secret value stored separately from the database, making it resistant to attacks even if the database is compromised. Unlike salt, which is unique per user but stored with the hash, pepper acts as an additional layer of defense against rainbow table and brute-force attacks. The secrecy and centralized management of pepper reduce exposure risks and bolster overall password protection in modern authentication systems.
Combining Salt and Pepper for Enhanced Security
Combining salt and pepper in password hashing significantly strengthens cryptographic security by mitigating risks of rainbow table and brute-force attacks. Salt, a unique per-user random value, ensures distinct hash outputs even for identical passwords, while pepper, a secret global value stored separately from the database, adds an additional layer of protection against server breaches. Integrating both techniques improves password hash resilience by complicating attackers' ability to reverse-engineer passwords, thereby enhancing overall system security.
Common Mistakes in Salt and Pepper Usage
Common mistakes in salt and pepper usage include reusing salts across multiple passwords, which diminishes their effectiveness in preventing rainbow table attacks, and storing pepper values alongside hashed passwords, compromising the additional layer of security peppers provide. Another frequent error is using insufficiently random or short salts and peppers, making them vulnerable to brute force or dictionary attacks. Failing to regularly update or rotate pepper values can also increase the risk of exposure if the pepper is ever leaked.
Best Practices for Storing and Managing Secrets
Salt involves adding unique, random data to each password before hashing, enhancing security by preventing rainbow table attacks. Pepper is a secret value, kept separate from the database and added to the password or hash to provide an extra layer of security against brute force attacks. Best practices for storing and managing secrets include using hardware security modules (HSMs) or secure vaults, rotating keys regularly, and ensuring salts are unique per password with peppers stored securely and independently.
Conclusion: Choosing the Right Hashing Approach
Selecting the appropriate password hashing technique significantly enhances security by mitigating risks associated with credential theft. Salt uniquely protects against rainbow table attacks by adding randomized data to each password hash, while pepper, a secret added to all passwords, strengthens defense against breaches even if salts and hashes are exposed. Combining both salt and pepper, tailored to system capabilities and threat models, results in a robust, layered approach to safeguarding user credentials.
Salt vs Pepper (in password hashing) Infographic
 difterm.com
difterm.com