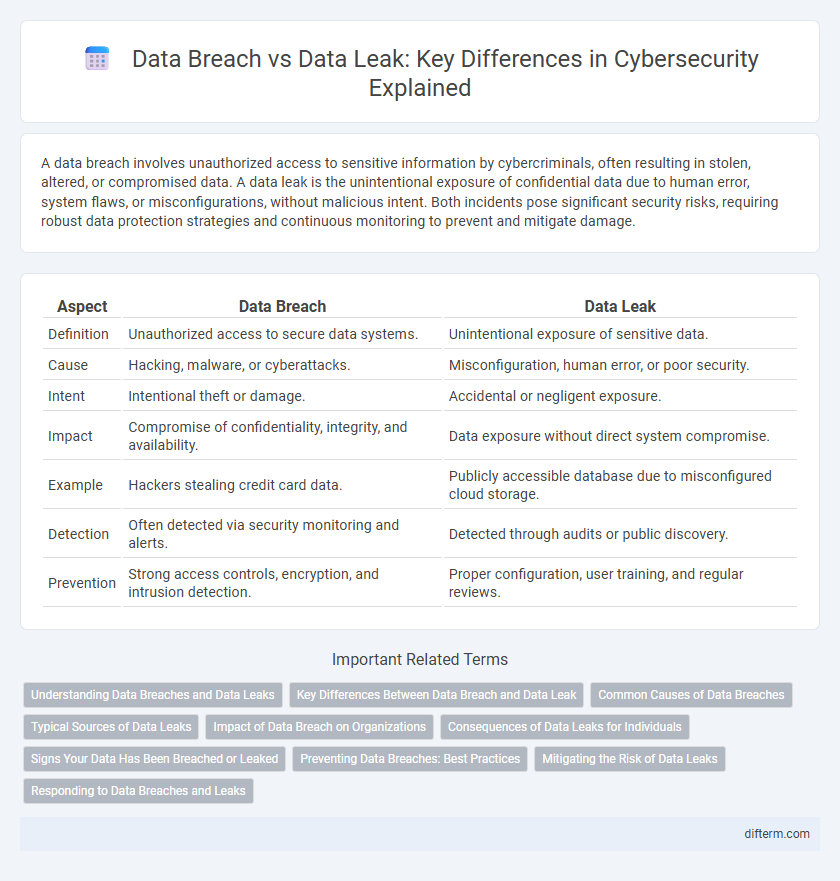
A data breach involves unauthorized access to sensitive information by cybercriminals, often resulting in stolen, altered, or compromised data. A data leak is the unintentional exposure of confidential data due to human error, system flaws, or misconfigurations, without malicious intent. Both incidents pose significant security risks, requiring robust data protection strategies and continuous monitoring to prevent and mitigate damage.
Table of Comparison
| Aspect | Data Breach | Data Leak |
|---|---|---|
| Definition | Unauthorized access to secure data systems. | Unintentional exposure of sensitive data. |
| Cause | Hacking, malware, or cyberattacks. | Misconfiguration, human error, or poor security. |
| Intent | Intentional theft or damage. | Accidental or negligent exposure. |
| Impact | Compromise of confidentiality, integrity, and availability. | Data exposure without direct system compromise. |
| Example | Hackers stealing credit card data. | Publicly accessible database due to misconfigured cloud storage. |
| Detection | Often detected via security monitoring and alerts. | Detected through audits or public discovery. |
| Prevention | Strong access controls, encryption, and intrusion detection. | Proper configuration, user training, and regular reviews. |
Understanding Data Breaches and Data Leaks
Data breaches involve unauthorized access to sensitive information, often resulting from cyberattacks or system vulnerabilities, exposing confidential data to malicious actors. In contrast, data leaks occur when sensitive information is inadvertently exposed due to misconfigurations, human error, or inadequate security controls, without direct external hacking. Understanding the distinct causes and implications of data breaches and data leaks is essential for implementing effective cybersecurity measures and protecting organizational data assets.
Key Differences Between Data Breach and Data Leak
A data breach involves unauthorized access or theft of sensitive information by malicious actors, often exploiting system vulnerabilities to extract data, whereas a data leak occurs when sensitive information is unintentionally exposed or accessible due to misconfigurations or human error. Data breaches typically involve deliberate cyberattacks aimed at compromising confidentiality, while data leaks result from accidental exposure without direct external hacking attempts. Understanding these distinctions aids in implementing targeted cybersecurity measures to prevent both intentional breaches and accidental leaks.
Common Causes of Data Breaches
Common causes of data breaches include weak passwords, unpatched software vulnerabilities, and phishing attacks that exploit user credentials. Employees accidentally mishandling sensitive data or falling victim to social engineering tactics also significantly contribute to breaches. Insecure third-party vendors and misconfigured cloud storage further increase the risk of unauthorized access and data exposure.
Typical Sources of Data Leaks
Typical sources of data leaks include misconfigured cloud storage, unsecured APIs, and insider threats such as employees mishandling sensitive information. Weaknesses in third-party vendor security and unpatched software vulnerabilities also frequently lead to unauthorized exposure of data. Understanding these sources is critical for implementing effective data protection strategies and preventing significant information breaches.
Impact of Data Breach on Organizations
Data breaches expose sensitive organizational information, leading to significant financial losses, legal penalties, and reputational damage. Compromised customer data undermines trust, causing long-term declines in customer loyalty and market value. Regulatory fines from authorities such as GDPR and HIPAA amplify the economic impact, stressing the importance of robust cybersecurity measures.
Consequences of Data Leaks for Individuals
Data leaks expose sensitive personal information such as social security numbers, financial details, and private communications, increasing the risk of identity theft and financial fraud for individuals. Unlike data breaches, which typically result from targeted attacks, data leaks often arise from accidental exposure or misconfigurations, causing widespread unauthorized access. The long-term consequences include compromised privacy, damaged reputation, and potential legal challenges stemming from the misuse of leaked information.
Signs Your Data Has Been Breached or Leaked
Unusual account activity, such as unexpected password changes or unauthorized transactions, often signals a data breach, while discovery of sensitive information publicly accessible online typically indicates a data leak. Frequent spam emails, sudden loss of access to accounts, and alerts from monitoring services are key signs your data has been compromised. Monitoring system logs for irregular access patterns and using breach detection tools can help identify both breaches and leaks promptly.
Preventing Data Breaches: Best Practices
Preventing data breaches involves implementing robust encryption protocols, regular security audits, and strict access controls to protect sensitive information from unauthorized entry. Employee training on phishing attacks and malware recognition significantly reduces the risk of human error leading to breaches. Deploying advanced intrusion detection systems and multi-factor authentication enhances overall network security and prevents accidental data leaks.
Mitigating the Risk of Data Leaks
Mitigating the risk of data leaks involves implementing robust access controls and continuous monitoring to detect unauthorized data exposure promptly. Encryption of sensitive information both at rest and in transit reduces the likelihood of data being readable if leaked. Regular security audits and employee training on data handling best practices further strengthen the defense against inadvertent or malicious data leaks.
Responding to Data Breaches and Leaks
Responding to data breaches requires immediate incident containment, comprehensive forensic analysis, and notification to affected parties to mitigate damage and comply with legal obligations. In contrast, addressing data leaks involves identifying the source of unauthorized data exposure, enhancing access controls, and implementing continuous monitoring to prevent recurrence. Both scenarios demand robust response protocols to protect sensitive information and maintain organizational trust.
Data breach vs Data leak Infographic
 difterm.com
difterm.com