Air gapping physically isolates critical systems from unsecured networks, eliminating remote access risks and ensuring maximum security. Network segmentation divides a network into smaller, controlled segments to limit unauthorized lateral movement and contain potential breaches. Combining both methods creates a layered defense, enhancing an organization's overall cybersecurity posture.
Table of Comparison
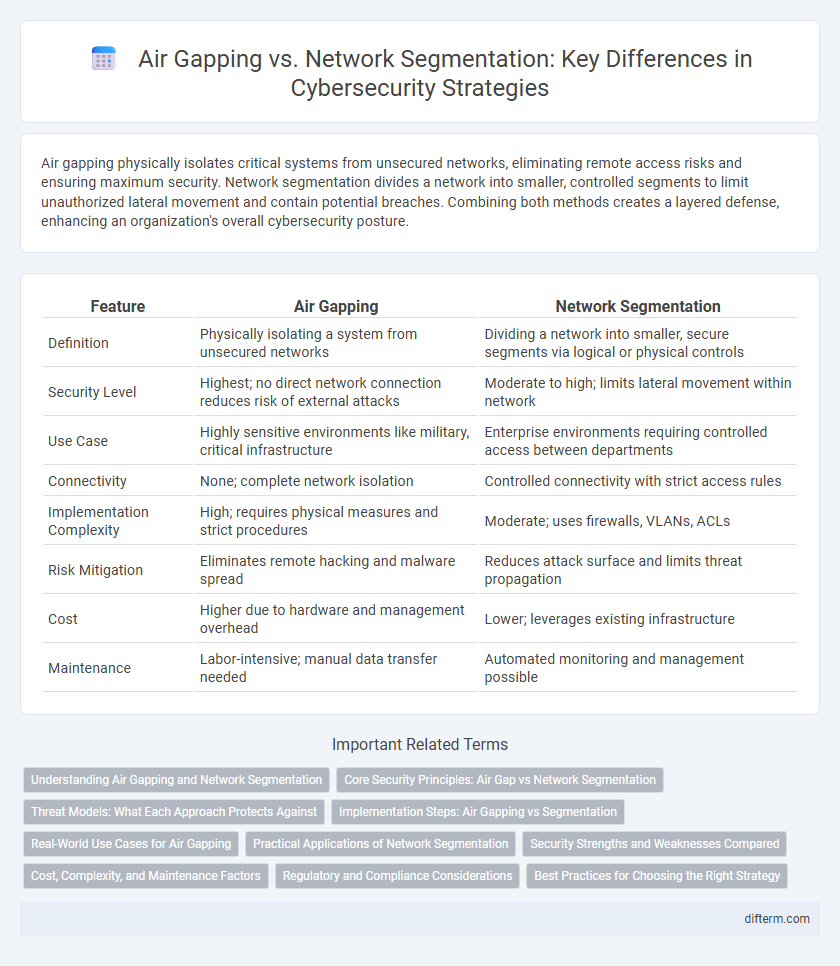
| Feature | Air Gapping | Network Segmentation |
|---|---|---|
| Definition | Physically isolating a system from unsecured networks | Dividing a network into smaller, secure segments via logical or physical controls |
| Security Level | Highest; no direct network connection reduces risk of external attacks | Moderate to high; limits lateral movement within network |
| Use Case | Highly sensitive environments like military, critical infrastructure | Enterprise environments requiring controlled access between departments |
| Connectivity | None; complete network isolation | Controlled connectivity with strict access rules |
| Implementation Complexity | High; requires physical measures and strict procedures | Moderate; uses firewalls, VLANs, ACLs |
| Risk Mitigation | Eliminates remote hacking and malware spread | Reduces attack surface and limits threat propagation |
| Cost | Higher due to hardware and management overhead | Lower; leverages existing infrastructure |
| Maintenance | Labor-intensive; manual data transfer needed | Automated monitoring and management possible |
Understanding Air Gapping and Network Segmentation
Air gapping isolates critical systems by physically disconnecting them from unsecured networks, preventing any digital communication and significantly reducing the risk of remote cyberattacks. Network segmentation divides a network into smaller, isolated segments to contain breaches and limit lateral movement of threats within an organization. Both strategies enhance cybersecurity by controlling access and reducing attack surfaces, but air gapping provides a higher level of isolation compared to network segmentation.
Core Security Principles: Air Gap vs Network Segmentation
Air gapping provides an isolated environment by physically separating critical systems from unsecured networks, eliminating data transmission pathways and significantly reducing cyberattack risks. Network segmentation divides a larger network into smaller, controlled segments, enforcing strict access controls and monitoring traffic to contain breaches and limit lateral movement within the network. Both air gapping and network segmentation apply the principle of least privilege and defense-in-depth to enhance data protection and maintain system integrity.
Threat Models: What Each Approach Protects Against
Air gapping protects against remote cyberattacks by isolating critical systems from any network connection, eliminating external access points and significantly reducing the risk of data breaches or malware infiltration. Network segmentation limits lateral movement within an internal network, containing threats such as insider attacks, malware spread, and compromised devices by dividing the network into isolated zones with controlled communication. Both strategies address different threat models: air gapping is effective against external network-based threats, while network segmentation focuses on minimizing damage from internal threats and improving overall network resilience.
Implementation Steps: Air Gapping vs Segmentation
Air gapping implementation involves physically isolating critical systems by removing all network connections, ensuring no data exchange with unsecured environments through strict hardware controls and manual data transfer protocols. Network segmentation requires designing and deploying VLANs, firewalls, and access control policies to create secure zones within a network, limiting lateral movement and reducing attack surfaces. Regular validation, monitoring, and updating of segmentation rules or air gap integrity are essential to maintain effective security postures in both methods.
Real-World Use Cases for Air Gapping
Air gapping is a cybersecurity strategy that physically isolates critical systems from unsecured networks, effectively preventing remote cyberattacks. Real-world use cases include safeguarding classified government data, protecting industrial control systems in utilities, and securing financial transaction networks where absolute isolation is essential. Unlike network segmentation, which relies on software-defined barriers within connected networks, air gapping ensures offline operation, minimizing the risk of lateral movement by threat actors.
Practical Applications of Network Segmentation
Network segmentation enhances security by dividing a network into isolated zones, limiting lateral movement of threats and containing breaches within specific segments. Practical applications include separating sensitive data environments from general user access, isolating critical infrastructure systems like SCADA networks, and enforcing access controls through firewalls and VLANs to reduce attack surfaces. This targeted control enables organizations to apply tailored security policies, monitor traffic efficiently, and respond faster to security incidents compared to air gapping, which physically isolates networks but lacks the granular flexibility of segmentation.
Security Strengths and Weaknesses Compared
Air gapping offers the strongest defense by completely isolating critical systems from external networks, effectively preventing remote cyber attacks and data breaches. Network segmentation improves security by dividing a network into isolated segments, limiting lateral movement of threats, but remains vulnerable to internal attacks and misconfigured segmentation policies. While air gapping provides maximum isolation, it often lacks flexibility and complicates data transfer processes, whereas network segmentation balances security with operational efficiency but requires continuous monitoring and robust access controls.
Cost, Complexity, and Maintenance Factors
Air gapping offers maximum security by physically isolating systems but incurs high costs and complex implementation challenges due to hardware requirements and strict maintenance protocols. Network segmentation reduces risk within connected environments by logically dividing networks, providing cost-effective scalability and simpler ongoing management. Choosing between the two depends on balancing budget constraints, security needs, and operational complexity.
Regulatory and Compliance Considerations
Air gapping provides the highest level of physical isolation by completely disconnecting critical systems from unsecured networks, aligning with strict regulatory requirements such as NIST 800-53 and HIPAA for safeguarding sensitive data. Network segmentation implements controlled boundaries within networks to limit access and reduce attack surfaces, supporting compliance frameworks like PCI-DSS and GDPR by enforcing data privacy and minimizing exposure. Regulatory standards often mandate either approach based on risk assessments, with air gapping preferred for mission-critical environments and segmentation suitable for complex infrastructures requiring controlled interconnectivity.
Best Practices for Choosing the Right Strategy
Air gapping provides maximum isolation by physically separating critical systems from unsecured networks, making it ideal for highly sensitive environments such as classified government or industrial control systems. Network segmentation enhances security by dividing a larger network into smaller, controlled zones, enabling granular access control and reducing the attack surface for enterprise environments with complex connectivity needs. Best practices recommend assessing threat models, data sensitivity, operational requirements, and compliance mandates to determine the appropriate balance between air gapping's isolation and segmentation's flexibility.
Air gapping vs Network segmentation Infographic
 difterm.com
difterm.com