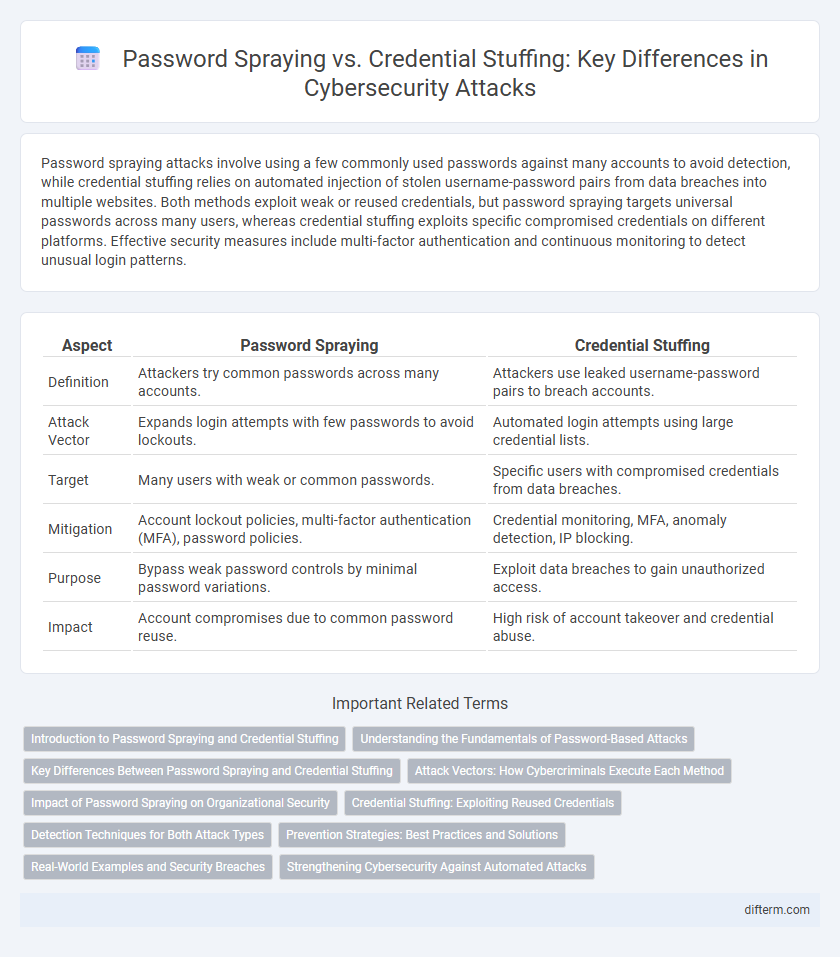
Password spraying attacks involve using a few commonly used passwords against many accounts to avoid detection, while credential stuffing relies on automated injection of stolen username-password pairs from data breaches into multiple websites. Both methods exploit weak or reused credentials, but password spraying targets universal passwords across many users, whereas credential stuffing exploits specific compromised credentials on different platforms. Effective security measures include multi-factor authentication and continuous monitoring to detect unusual login patterns.
Table of Comparison
| Aspect | Password Spraying | Credential Stuffing |
|---|---|---|
| Definition | Attackers try common passwords across many accounts. | Attackers use leaked username-password pairs to breach accounts. |
| Attack Vector | Expands login attempts with few passwords to avoid lockouts. | Automated login attempts using large credential lists. |
| Target | Many users with weak or common passwords. | Specific users with compromised credentials from data breaches. |
| Mitigation | Account lockout policies, multi-factor authentication (MFA), password policies. | Credential monitoring, MFA, anomaly detection, IP blocking. |
| Purpose | Bypass weak password controls by minimal password variations. | Exploit data breaches to gain unauthorized access. |
| Impact | Account compromises due to common password reuse. | High risk of account takeover and credential abuse. |
Introduction to Password Spraying and Credential Stuffing
Password spraying involves attackers using a limited set of common passwords against many user accounts to avoid detection by lockout mechanisms. Credential stuffing exploits leaked username-password pairs from data breaches to automate login attempts across multiple sites, often leveraging large-scale botnets. Both techniques target account access but differ fundamentally in their approach and the data they utilize.
Understanding the Fundamentals of Password-Based Attacks
Password spraying involves attackers attempting a small set of commonly used passwords across many user accounts to evade lockout policies, while credential stuffing uses breached username-password pairs to automate login attempts on multiple sites. Both attack methods exploit weak password practices and lack of multi-factor authentication, significantly increasing the risk of unauthorized access. Implementing adaptive security measures, such as anomaly detection and rate limiting, is essential to mitigate password-based threats effectively.
Key Differences Between Password Spraying and Credential Stuffing
Password spraying involves attackers using a few common passwords across many accounts to avoid detection, while credential stuffing relies on automated injection of large volumes of stolen username-password pairs into login portals. Password spraying targets weak passwords and exploits account lockout policies, whereas credential stuffing capitalizes on reused credentials from data breaches. Both attacks threaten account security but differ in methodology, scale, and defender mitigation strategies.
Attack Vectors: How Cybercriminals Execute Each Method
Password spraying attacks exploit common passwords across many accounts by systematically trying a single password on multiple usernames, leveraging weak password policies and user reuse. Credential stuffing relies on previously compromised credential databases, automating login attempts to validate stolen username-password pairs against targeted services. Both attack vectors exploit authentication processes but differ in source data and attack scale, making multi-factor authentication and anomaly detection critical defenses.
Impact of Password Spraying on Organizational Security
Password spraying poses a significant threat to organizational security by exploiting commonly used passwords across multiple accounts, often bypassing traditional brute-force detection systems. This attack method can lead to unauthorized access and lateral movement within networks, resulting in data breaches and compromised sensitive information. Implementing multi-factor authentication and continuous monitoring is essential to mitigate the high-risk impact of password spraying on enterprise environments.
Credential Stuffing: Exploiting Reused Credentials
Credential stuffing attacks leverage reused credentials obtained from previous breaches, enabling attackers to automate login attempts across multiple websites with high success rates. This tactic exploits the common user behavior of password reuse, bypassing traditional security measures like CAPTCHA and two-factor authentication when poorly implemented. Effective defense strategies include monitoring for unusual login patterns, enforcing strong password policies, and employing multi-factor authentication to mitigate the risks associated with credential stuffing.
Detection Techniques for Both Attack Types
Password spraying detection techniques analyze login attempts for repeated use of common passwords across multiple accounts, leveraging anomaly detection and IP reputation analysis to identify patterns indicative of mass attacks. Credential stuffing detection employs behavioral analytics and device fingerprinting to spot automated login attempts using leaked credential databases, focusing on unusual access patterns and velocity checks. Both methods benefit from integrating machine learning models that correlate failed login metrics with known threat intelligence for enhanced security response.
Prevention Strategies: Best Practices and Solutions
Implement multifactor authentication (MFA) and enforce strong, unique passwords to effectively mitigate password spraying and credential stuffing attacks. Employ continuous monitoring and anomaly detection systems to identify unusual login patterns and quickly respond to potential breaches. Regularly update threat intelligence and educate users on phishing risks to strengthen overall credential security.
Real-World Examples and Security Breaches
Password spraying attacks were responsible for high-profile breaches such as the Microsoft Exchange Server compromise in 2021, where attackers used common passwords to exploit multiple accounts without triggering lockouts. Credential stuffing led to significant incidents like the 2019 Twitter data breach, leveraging leaked username-password pairs to gain unauthorized access on multiple platforms. Security teams must analyze these attack patterns, noting that password spraying targets weak passwords across many accounts, while credential stuffing exploits reused credentials from previous breaches.
Strengthening Cybersecurity Against Automated Attacks
Password spraying targets many accounts with a few common passwords, while credential stuffing leverages leaked username-password pairs to breach specific accounts. Implementing multi-factor authentication (MFA), deploying behavior-based anomaly detection systems, and enforcing strict password policies significantly reduce the risk posed by these automated attacks. Continuous monitoring and real-time threat intelligence allow organizations to swiftly identify and respond to suspicious login attempts, strengthening overall cybersecurity posture.
password spraying vs credential stuffing Infographic
 difterm.com
difterm.com