MAC address filtering enhances security by allowing only recognized hardware devices to connect to the network, offering precise access control based on unique device identifiers. IP filtering restricts network access by permitting or blocking devices based on their IP addresses, providing flexibility for managing traffic but potentially less accuracy due to IP address changes. Combining both methods can strengthen perimeter defense, ensuring that only authorized devices with specific IP addresses communicate on the network.
Table of Comparison
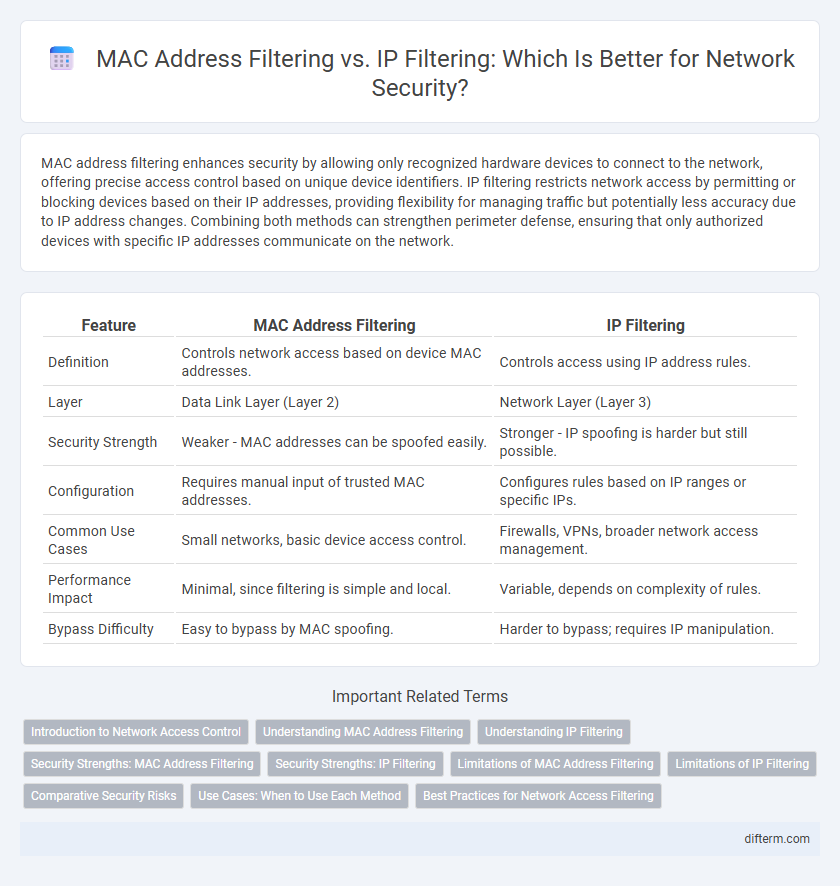
| Feature | MAC Address Filtering | IP Filtering |
|---|---|---|
| Definition | Controls network access based on device MAC addresses. | Controls access using IP address rules. |
| Layer | Data Link Layer (Layer 2) | Network Layer (Layer 3) |
| Security Strength | Weaker - MAC addresses can be spoofed easily. | Stronger - IP spoofing is harder but still possible. |
| Configuration | Requires manual input of trusted MAC addresses. | Configures rules based on IP ranges or specific IPs. |
| Common Use Cases | Small networks, basic device access control. | Firewalls, VPNs, broader network access management. |
| Performance Impact | Minimal, since filtering is simple and local. | Variable, depends on complexity of rules. |
| Bypass Difficulty | Easy to bypass by MAC spoofing. | Harder to bypass; requires IP manipulation. |
Introduction to Network Access Control
MAC address filtering enhances network access control by permitting or denying devices based on their unique hardware identifiers, effectively preventing unauthorized physical connections. IP filtering manages access by allowing or blocking traffic from specific IP addresses, offering a more flexible but potentially less secure method due to IP spoofing risks. Both methods serve as foundational mechanisms in implementing layered network security policies to control device connectivity and mitigate unauthorized access.
Understanding MAC Address Filtering
MAC address filtering enhances network security by restricting device access based on unique hardware identifiers, ensuring only authorized devices connect to the network. Unlike IP filtering, which limits access using IP addresses subject to change, MAC address filtering provides a more stable layer of defense against unauthorized entry. This method is particularly effective in environments requiring strict device-level control and monitoring.
Understanding IP Filtering
IP filtering controls network access by examining packets based on their IP addresses, enabling administrators to allow or block traffic from specific IP ranges or subnets. This technique enhances network security by preventing unauthorized devices from communicating within the network, reducing the risk of attacks such as IP spoofing and unauthorized access. Unlike MAC address filtering, which targets hardware addresses at the data link layer, IP filtering operates at the network layer, providing more scalable and flexible traffic management.
Security Strengths: MAC Address Filtering
MAC address filtering enhances network security by allowing only devices with authorized hardware addresses to access the network, effectively preventing unauthorized connections. It provides a layer of control that is difficult to bypass because MAC addresses are unique to each network interface card. While vulnerable to spoofing in some cases, MAC filtering significantly reduces random or casual access attempts, making it a robust security measure in controlled environments.
Security Strengths: IP Filtering
IP filtering enhances network security by controlling access based on IP addresses, allowing precise identification and management of devices attempting to connect. Unlike MAC address filtering, IP filtering can be more effective against spoofing attacks since IP addresses are harder to falsify within certain network environments. This method integrates smoothly with firewalls and intrusion detection systems to establish comprehensive security policies.
Limitations of MAC Address Filtering
MAC address filtering is limited by its vulnerability to spoofing, as attackers can easily mimic authorized MAC addresses to bypass restrictions. It also lacks scalability in large networks due to the manual effort required in maintaining the MAC address list. Unlike IP filtering, MAC filtering does not provide comprehensive control over network traffic, making it less effective in preventing unauthorized access.
Limitations of IP Filtering
IP filtering faces limitations such as vulnerability to IP spoofing, where attackers manipulate IP addresses to bypass restrictions, compromising network security. It struggles to effectively control access in dynamic IP environments due to frequent IP address changes, reducing its reliability. Furthermore, IP filtering cannot enforce granular device-level policies, limiting its effectiveness against sophisticated threats targeting specific hardware.
Comparative Security Risks
MAC address filtering offers basic network access control by allowing devices based on hardware addresses, but it is vulnerable since MAC addresses can be easily spoofed by attackers. IP filtering provides more granular control by blocking or allowing traffic based on IP addresses, though it can be bypassed through IP spoofing or tunneling techniques. Combining both methods strengthens security by addressing unique vulnerabilities associated with each filtering type, reducing the overall risk of unauthorized network access.
Use Cases: When to Use Each Method
MAC address filtering is ideal for securing small, controlled networks where specific devices need to be granted or denied access based on hardware identifiers, such as in home or small office setups. IP filtering suits environments requiring broader network management and dynamic policies, like enterprise networks or public Wi-Fi, where access control is based on IP address ranges or subnets. Combining both methods enhances security by ensuring device-level validation and network-level access control, effectively mitigating unauthorized access.
Best Practices for Network Access Filtering
MAC address filtering controls network access by allowing devices with specific hardware addresses, providing granular device-level security but is susceptible to spoofing. IP filtering manages traffic based on IP addresses, offering broader network-level control but may be less effective against dynamic or spoofed IPs. Best practices combine both methods with strong authentication protocols and regular updates to access control lists, enhancing overall network security and minimizing unauthorized access risks.
MAC Address Filtering vs IP Filtering Infographic
 difterm.com
difterm.com