Runtime Application Self-Protection (RASP) integrates security within the application, providing real-time threat detection and mitigation by monitoring application behavior from inside. Web Application Firewall (WAF) protects web applications by filtering and monitoring HTTP traffic at the network edge, blocking malicious requests before they reach the application. RASP offers more precise threat responses by understanding application context, while WAF excels at blocking broad attack patterns and reducing the attack surface externally.
Table of Comparison
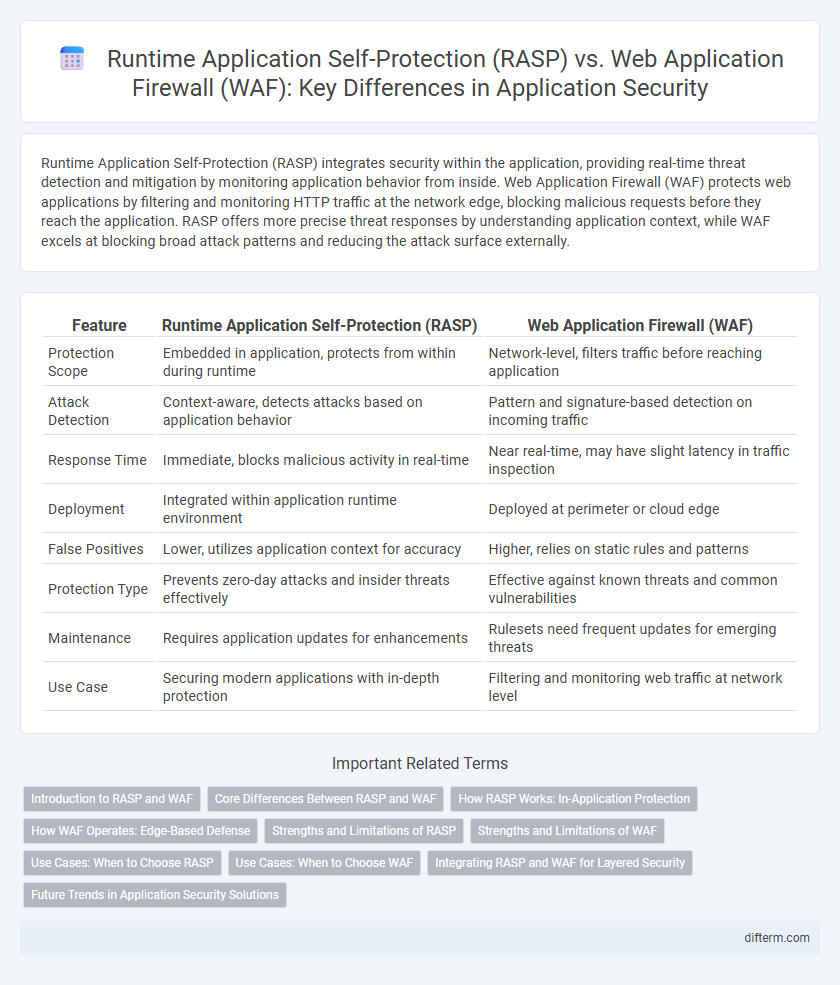
| Feature | Runtime Application Self-Protection (RASP) | Web Application Firewall (WAF) |
|---|---|---|
| Protection Scope | Embedded in application, protects from within during runtime | Network-level, filters traffic before reaching application |
| Attack Detection | Context-aware, detects attacks based on application behavior | Pattern and signature-based detection on incoming traffic |
| Response Time | Immediate, blocks malicious activity in real-time | Near real-time, may have slight latency in traffic inspection |
| Deployment | Integrated within application runtime environment | Deployed at perimeter or cloud edge |
| False Positives | Lower, utilizes application context for accuracy | Higher, relies on static rules and patterns |
| Protection Type | Prevents zero-day attacks and insider threats effectively | Effective against known threats and common vulnerabilities |
| Maintenance | Requires application updates for enhancements | Rulesets need frequent updates for emerging threats |
| Use Case | Securing modern applications with in-depth protection | Filtering and monitoring web traffic at network level |
Introduction to RASP and WAF
Runtime Application Self-Protection (RASP) integrates security directly into the application runtime environment, enabling real-time detection and prevention of threats from within the app. Web Application Firewall (WAF) operates at the network perimeter, filtering and monitoring HTTP traffic to block malicious requests before they reach the application. Both RASP and WAF serve critical roles in web security, with RASP providing in-depth internal protection and WAF offering external threat filtering.
Core Differences Between RASP and WAF
Runtime Application Self-Protection (RASP) integrates directly into the application runtime environment to monitor and block threats in real-time based on the application's own logic, providing granular protection against zero-day attacks and insider threats. Web Application Firewalls (WAF) operate at the network perimeter, filtering and monitoring HTTP traffic to block common web attacks like SQL injection and cross-site scripting using predefined rules and signatures. Unlike WAFs, which rely on external traffic analysis, RASP offers improved accuracy by understanding the internal state of the application, enabling contextual threat detection and mitigation.
How RASP Works: In-Application Protection
Runtime Application Self-Protection (RASP) operates by integrating security measures directly into the application, monitoring and analyzing real-time behavior to detect and block threats from within the software environment. Unlike Web Application Firewalls (WAFs) that filter traffic externally, RASP leverages in-application instrumentation to identify vulnerabilities such as injection attacks and unauthorized data access as execution occurs. This internal defense mechanism enables precise threat detection with minimal false positives, improving overall application security through continuous contextual analysis during runtime.
How WAF Operates: Edge-Based Defense
A Web Application Firewall (WAF) operates as an edge-based defense by filtering and monitoring HTTP traffic between a web application and the internet, blocking malicious requests before they reach the server. It uses predefined security rules and behavioral analysis to detect and prevent attacks like SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks at the network perimeter. By handling threats at the edge, WAFs reduce the attack surface and minimize the risk of exploitation, complementing runtime application self-protection (RASP) which works internally during code execution.
Strengths and Limitations of RASP
Runtime Application Self-Protection (RASP) strengthens security by integrating directly into an application, enabling real-time detection and prevention of attacks from within the runtime environment, effectively stopping threats such as SQL injection, cross-site scripting, and zero-day attacks. However, RASP's effectiveness can be limited by potential performance overhead, complexity of integration with existing applications, and its scope confined to application-level threats, lacking protection against network-level attacks. Unlike Web Application Firewalls (WAFs), RASP operates with deeper contextual awareness of the application logic but may require ongoing tuning to minimize false positives and ensure comprehensive coverage across diverse application architectures.
Strengths and Limitations of WAF
Web Application Firewalls (WAFs) effectively protect web applications by filtering and monitoring HTTP traffic to block common attacks such as SQL injection and cross-site scripting. Their strength lies in deploying predefined rules and signatures to prevent known threats without modifying application code. Limitations include difficulty handling complex or zero-day attacks and potential false positives that may disrupt legitimate user traffic.
Use Cases: When to Choose RASP
Runtime Application Self-Protection (RASP) excels in providing real-time, in-app security by detecting and preventing threats during application execution, making it ideal for complex, dynamic environments with frequent code changes. Unlike Web Application Firewalls (WAFs) that filter traffic at the perimeter, RASP integrates within the application, offering granular protection against zero-day attacks and insider threats. Organizations prioritize RASP when needing precise vulnerability mitigation, continuous monitoring, and protection tailored to specific application logic.
Use Cases: When to Choose WAF
Web Application Firewalls (WAF) are ideal for protecting web applications against common threats like SQL injection, cross-site scripting (XSS), and automated bot attacks by filtering and monitoring HTTP traffic at the network edge. They are most effective for organizations seeking immediate defense against external threats, regulatory compliance, and protection of legacy applications without modifying the application code. WAFs complement Runtime Application Self-Protection (RASP) by providing perimeter-level security, especially in scenarios where rapid deployment and broad coverage of web traffic are critical.
Integrating RASP and WAF for Layered Security
Integrating Runtime Application Self-Protection (RASP) and Web Application Firewall (WAF) enhances layered security by combining real-time threat detection with perimeter filtering to protect web applications from a broad range of attacks. RASP operates within the application runtime environment, providing immediate, context-aware defenses against vulnerabilities such as SQL injection and cross-site scripting, while WAF inspects incoming traffic at the network edge to block known malicious patterns. This integrated approach improves overall security posture by addressing both external threats and internal application-level risks, enabling comprehensive protection across different attack vectors.
Future Trends in Application Security Solutions
Runtime Application Self-Protection (RASP) leverages real-time monitoring and AI-driven behavioral analysis to detect and mitigate threats within the application, offering granular protection beyond perimeter defenses. Web Application Firewalls (WAFs) continue evolving with enhanced machine learning algorithms and cloud-native integration to provide scalable traffic filtering and attack signature updates. Future trends emphasize the convergence of RASP and WAF technologies into unified platforms, incorporating zero-trust principles and automated response capabilities to address increasingly sophisticated cyber threats in dynamic environments.
runtime application self-protection vs web application firewall Infographic
 difterm.com
difterm.com