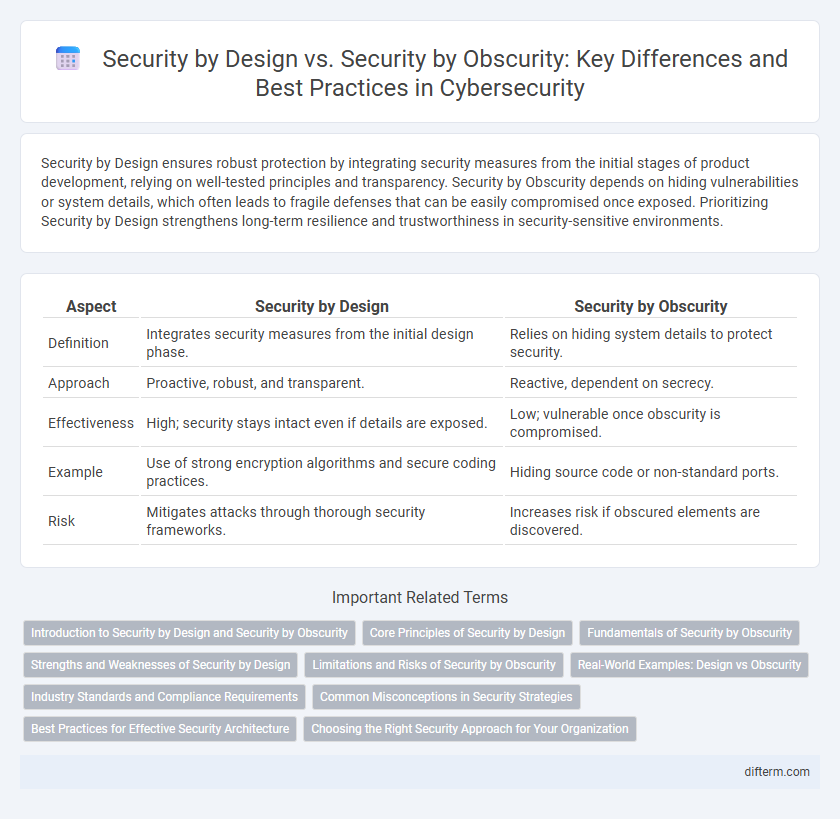
Security by Design ensures robust protection by integrating security measures from the initial stages of product development, relying on well-tested principles and transparency. Security by Obscurity depends on hiding vulnerabilities or system details, which often leads to fragile defenses that can be easily compromised once exposed. Prioritizing Security by Design strengthens long-term resilience and trustworthiness in security-sensitive environments.
Table of Comparison
| Aspect | Security by Design | Security by Obscurity |
|---|---|---|
| Definition | Integrates security measures from the initial design phase. | Relies on hiding system details to protect security. |
| Approach | Proactive, robust, and transparent. | Reactive, dependent on secrecy. |
| Effectiveness | High; security stays intact even if details are exposed. | Low; vulnerable once obscurity is compromised. |
| Example | Use of strong encryption algorithms and secure coding practices. | Hiding source code or non-standard ports. |
| Risk | Mitigates attacks through thorough security frameworks. | Increases risk if obscured elements are discovered. |
Introduction to Security by Design and Security by Obscurity
Security by Design integrates security measures into the development lifecycle, ensuring systems are robust against threats from the outset. It emphasizes proactive risk assessment, encryption, and access controls embedded during architecture and coding phases. In contrast, Security by Obscurity relies on hiding system details or mechanisms, which can lead to vulnerabilities if the obscured information is discovered, making it a less reliable defense strategy.
Core Principles of Security by Design
Security by Design emphasizes proactive integration of core principles such as least privilege, defense in depth, and fail-safe defaults to create inherently secure systems. This approach relies on transparent, well-documented security measures rather than relying on hidden mechanisms or secrecy, which are central to Security by Obscurity. Implementing strong authentication, rigorous access controls, and continuous monitoring ensures resilience against evolving threats through foundational security architecture.
Fundamentals of Security by Obscurity
Security by Obscurity relies on hiding system details to prevent unauthorized access, but it lacks robust protection because it does not address underlying vulnerabilities. The fundamental weakness lies in assuming secrecy alone will secure a system, making it fragile if the obscured information is discovered. Effective security requires transparent, well-designed mechanisms that withstand scrutiny rather than relying solely on concealment.
Strengths and Weaknesses of Security by Design
Security by Design integrates security measures into every phase of system development, ensuring robust protection against vulnerabilities through proactive risk management and thorough testing. Its strengths include enhanced resilience, transparency, and easier maintenance, while weaknesses may arise from increased initial development time and higher upfront costs. Despite these challenges, Security by Design offers a sustainable approach that reduces long-term risks compared to Security by Obscurity, which relies on secrecy and is vulnerable if protections are exposed.
Limitations and Risks of Security by Obscurity
Security by Obscurity relies on hiding system details, which creates a false sense of safety and leaves vulnerabilities unaddressed, increasing the risk of exploitation once the obscurity is uncovered. This approach lacks transparency and does not withstand rigorous testing or public scrutiny, making it inherently fragile and unreliable for long-term protection. Unlike Security by Design, which proactively integrates comprehensive safeguards, Security by Obscurity fails to provide a robust defense against evolving threats and sophisticated attackers.
Real-World Examples: Design vs Obscurity
Security by Design implements fundamental principles such as least privilege, defense in depth, and rigorous access controls, ensuring robust protection exemplified by systems like Google's BeyondCorp, which enforces zero-trust architecture from the ground up. Security by Obscurity relies on hiding vulnerabilities or system details, often exemplified by early Wi-Fi encryption protocols like WEP, which failed catastrophically once the underlying weaknesses were discovered. Real-world failures of security by obscurity highlight the importance of transparency and proactive threat modeling in effective security design.
Industry Standards and Compliance Requirements
Security by Design integrates robust security principles from the initial development phases, aligning with industry standards such as ISO/IEC 27001 and NIST frameworks to ensure compliance and minimize vulnerabilities. Security by Obscurity relies on secrecy of implementation details, which fails to meet regulatory requirements like GDPR and HIPAA, increasing risk of non-compliance and breaches. Regulatory bodies mandate transparent, verifiable security controls, making Security by Design essential for effective risk management and certification adherence.
Common Misconceptions in Security Strategies
Security by Design integrates robust, transparent security measures from the inception of a system, ensuring comprehensive protection through well-defined architecture and rigorous testing. Security by Obscurity relies on secrecy of design or implementation details, which often leads to false confidence and increased vulnerability once the obscurity is compromised. Common misconceptions include assuming Security by Obscurity is sufficient, ignoring its fragility compared to the proactive, systematically embedded practices of Security by Design.
Best Practices for Effective Security Architecture
Security by Design emphasizes embedding robust security measures from the initial stages of software development, ensuring comprehensive protection through principles like least privilege and defense in depth. Security by Obscurity relies on hiding system details or mechanisms, which is ineffective alone since attackers can eventually uncover these secrets. Best practices for effective security architecture prioritize transparent, well-documented controls and continuous risk assessment over relying on secrecy, enabling resilient systems against evolving threats.
Choosing the Right Security Approach for Your Organization
Security by Design integrates robust protection measures at every stage of system development, ensuring long-term resilience against threats through proactive vulnerability management. Security by Obscurity relies on concealing system details, which often fails against skilled adversaries and offers limited protection. Organizations benefit most from prioritizing Security by Design principles, aligning security strategies with industry standards like ISO/IEC 27001 and incorporating continuous risk assessment to safeguard assets effectively.
Security by Design vs Security by Obscurity Infographic
 difterm.com
difterm.com