Role-Based Access Control (RBAC) simplifies security management by assigning permissions based on predefined roles, making it effective for organizations with clear hierarchies. Attribute-Based Access Control (ABAC) offers finer-grained access by evaluating user attributes, environment conditions, and resource characteristics, enhancing flexibility and security in dynamic environments. Choosing between RBAC and ABAC depends on organizational needs for scalability, complexity, and precision in access control policies.
Table of Comparison
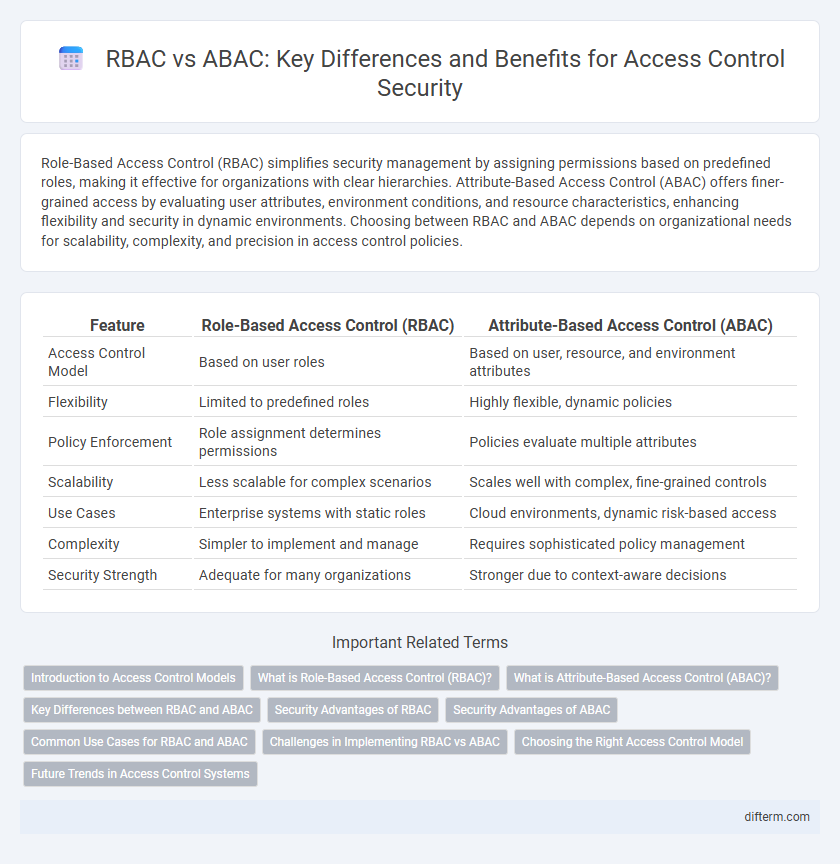
| Feature | Role-Based Access Control (RBAC) | Attribute-Based Access Control (ABAC) |
|---|---|---|
| Access Control Model | Based on user roles | Based on user, resource, and environment attributes |
| Flexibility | Limited to predefined roles | Highly flexible, dynamic policies |
| Policy Enforcement | Role assignment determines permissions | Policies evaluate multiple attributes |
| Scalability | Less scalable for complex scenarios | Scales well with complex, fine-grained controls |
| Use Cases | Enterprise systems with static roles | Cloud environments, dynamic risk-based access |
| Complexity | Simpler to implement and manage | Requires sophisticated policy management |
| Security Strength | Adequate for many organizations | Stronger due to context-aware decisions |
Introduction to Access Control Models
Role-Based Access Control (RBAC) assigns permissions based on predefined user roles, streamlining access management in organizations by grouping users according to job functions. Attribute-Based Access Control (ABAC) evaluates a combination of user attributes, resource characteristics, and environmental conditions to make dynamic access decisions, offering granular and context-aware security enforcement. Both models serve as fundamental frameworks for controlling access in information security, with RBAC emphasizing simplicity and ABAC focusing on flexibility and precision.
What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) is a security mechanism that restricts system access based on users' roles within an organization, defining permissions according to job functions. RBAC simplifies management by assigning predefined roles with specific access rights, ensuring users only access information necessary for their duties. This method enhances security by minimizing unauthorized access and supporting compliance with organizational policies and regulatory requirements.
What is Attribute-Based Access Control (ABAC)?
Attribute-Based Access Control (ABAC) is a dynamic security model that grants access based on user attributes, resource attributes, and environmental conditions, enabling fine-grained and context-aware authorization decisions. It evaluates multiple attributes such as user role, time of access, location, and device type to enforce policies in real-time, enhancing security flexibility and precision. ABAC supports complex policy expressions, making it suitable for cloud environments and organizations requiring scalable, adaptive access control mechanisms.
Key Differences between RBAC and ABAC
Role-Based Access Control (RBAC) assigns permissions to users based on predefined roles, simplifying management but limiting flexibility in dynamic environments. Attribute-Based Access Control (ABAC) evaluates multiple attributes such as user characteristics, resource types, and environmental conditions for granular, context-aware access decisions. ABAC offers higher adaptability for complex security policies, whereas RBAC provides straightforward implementation suitable for static access requirements.
Security Advantages of RBAC
Role-Based Access Control (RBAC) enhances security by restricting system access based on predefined user roles, minimizing the risk of unauthorized data exposure. It simplifies permission management through role assignments, ensuring consistent enforcement of access policies across the organization. RBAC also supports compliance requirements by providing clear audit trails tied to specific roles and responsibilities.
Security Advantages of ABAC
Attribute-Based Access Control (ABAC) enhances security by providing fine-grained access decisions based on multiple attributes such as user role, location, device type, and time of access, allowing dynamic and context-aware policy enforcement. Unlike Role-Based Access Control (RBAC), which relies solely on predefined roles, ABAC reduces the risk of privilege escalation and unauthorized access by evaluating real-time conditions and user attributes. This adaptive approach improves risk management and compliance in complex and heterogeneous security environments.
Common Use Cases for RBAC and ABAC
Role-Based Access Control (RBAC) is commonly used in enterprise environments where access permissions are assigned based on predefined roles, such as employee, manager, or administrator, making it ideal for organizations with clear hierarchical structures. Attribute-Based Access Control (ABAC) excels in dynamic and complex environments by granting access based on user attributes, resource attributes, and environmental conditions, which is essential for healthcare systems and cloud services requiring granular and context-aware access policies. Both models enhance security by controlling user access but are chosen based on organizational needs--RBAC for simplicity and scale, ABAC for flexibility and precision.
Challenges in Implementing RBAC vs ABAC
Implementing Role-Based Access Control (RBAC) faces challenges such as role explosion, where an increasing number of roles complicates management and reduces scalability. Attribute-Based Access Control (ABAC) demands complex policy definitions and requires continuous evaluation of user, resource, and environmental attributes, leading to higher implementation complexity and system overhead. Both models struggle with dynamic access requirements, but ABAC offers finer-grained control at the cost of increased policy administration efforts.
Choosing the Right Access Control Model
Selecting the right access control model depends on organizational complexity and security requirements. Role-Based Access Control (RBAC) simplifies management by assigning permissions to predefined roles, making it ideal for organizations with stable, well-defined job functions. Attribute-Based Access Control (ABAC) offers dynamic, fine-grained access decisions based on user attributes, resource properties, and environmental conditions, suitable for environments demanding contextual and adaptive security policies.
Future Trends in Access Control Systems
Emerging trends in access control systems emphasize integrating AI-driven analytics with Attribute-Based Access Control (ABAC) for dynamic, context-aware permissions, enhancing security in complex environments. Role-Based Access Control (RBAC) remains integral in structured, enterprise settings but is increasingly complemented by ABAC to address granular access needs and real-time risk factors. Hybrid models combining RBAC's simplicity with ABAC's flexibility represent the future, leveraging machine learning to automate policy enforcement and adapt to evolving threat landscapes.
Role-Based Access Control (RBAC) vs Attribute-Based Access Control (ABAC) Infographic
 difterm.com
difterm.com