A Security Operations Center (SOC) focuses on monitoring, detecting, and responding to cybersecurity threats, ensuring the protection of digital assets and sensitive data. In contrast, a Network Operations Center (NOC) manages network infrastructure, maintaining optimal performance and troubleshooting connectivity issues. Both SOC and NOC are essential, but the SOC specializes in security incident handling while the NOC prioritizes network stability and uptime.
Table of Comparison
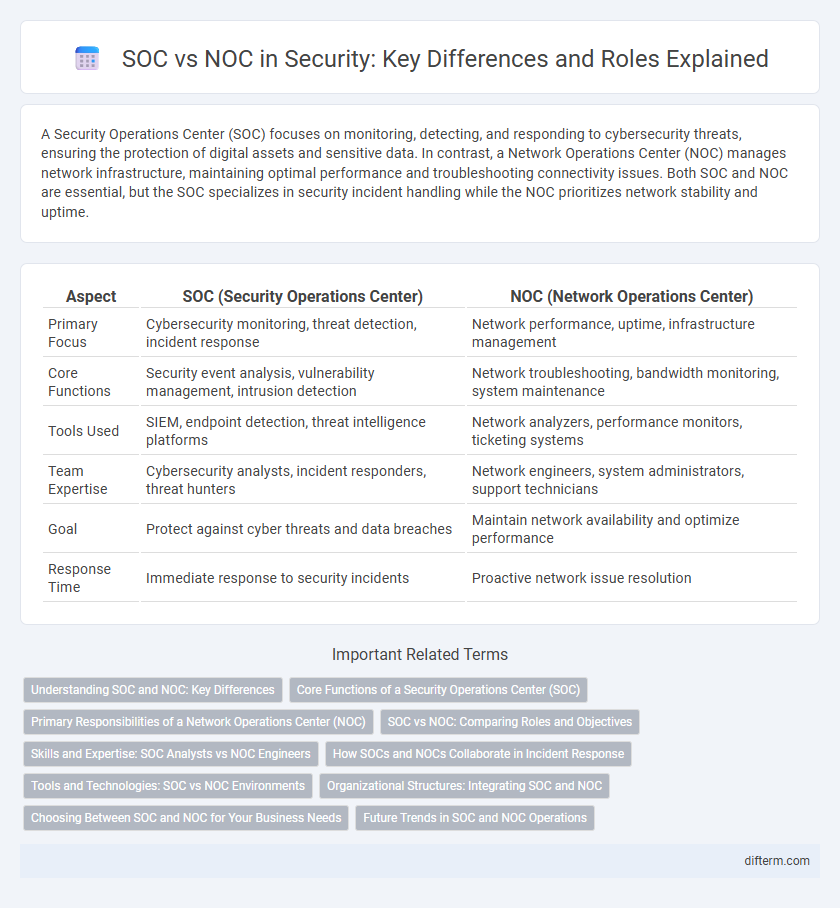
| Aspect | SOC (Security Operations Center) | NOC (Network Operations Center) |
|---|---|---|
| Primary Focus | Cybersecurity monitoring, threat detection, incident response | Network performance, uptime, infrastructure management |
| Core Functions | Security event analysis, vulnerability management, intrusion detection | Network troubleshooting, bandwidth monitoring, system maintenance |
| Tools Used | SIEM, endpoint detection, threat intelligence platforms | Network analyzers, performance monitors, ticketing systems |
| Team Expertise | Cybersecurity analysts, incident responders, threat hunters | Network engineers, system administrators, support technicians |
| Goal | Protect against cyber threats and data breaches | Maintain network availability and optimize performance |
| Response Time | Immediate response to security incidents | Proactive network issue resolution |
Understanding SOC and NOC: Key Differences
A Security Operations Center (SOC) specializes in monitoring, detecting, and responding to cybersecurity threats, utilizing advanced tools like SIEM and threat intelligence platforms. In contrast, a Network Operations Center (NOC) focuses on network performance, ensuring uptime, fault management, and infrastructure maintenance. While SOC centers on security incident management, NOC prioritizes network availability and operational efficiency.
Core Functions of a Security Operations Center (SOC)
A Security Operations Center (SOC) primarily focuses on continuous monitoring, incident detection, and response to cybersecurity threats using advanced security information and event management (SIEM) systems. The SOC team conducts threat analysis, vulnerability assessments, and mitigation to protect organizational assets from cyber attacks such as malware, ransomware, and phishing. Unlike a Network Operations Center (NOC), which manages network performance and uptime, the SOC specializes in proactive defense and forensic analysis to minimize security risks.
Primary Responsibilities of a Network Operations Center (NOC)
A Network Operations Center (NOC) is primarily responsible for monitoring, managing, and maintaining an organization's network infrastructure to ensure optimal performance and uptime. Key duties include real-time network traffic analysis, incident detection, troubleshooting connectivity issues, and coordinating maintenance activities. NOC teams also handle network configuration, firmware updates, and performance optimization, ensuring the reliability and stability of enterprise networks.
SOC vs NOC: Comparing Roles and Objectives
SOC (Security Operations Center) focuses on proactive threat detection, incident response, and cybersecurity monitoring to protect an organization's digital assets. NOC (Network Operations Center) is responsible for maintaining optimal network performance, availability, and infrastructure troubleshooting. While SOC emphasizes security threat mitigation, NOC ensures network reliability and operational continuity.
Skills and Expertise: SOC Analysts vs NOC Engineers
SOC analysts specialize in cybersecurity threat detection, incident response, and vulnerability assessment, leveraging skills in malware analysis, intrusion detection systems, and forensic investigation. NOC engineers concentrate on network performance, infrastructure monitoring, and system uptime, with expertise in network protocols, server management, and hardware troubleshooting. Both roles require analytical thinking and problem-solving but differ fundamentally in their focus on security event management versus network reliability and operational continuity.
How SOCs and NOCs Collaborate in Incident Response
Security Operations Centers (SOCs) and Network Operations Centers (NOCs) collaborate closely in incident response by combining their expertise to detect, analyze, and mitigate cyber threats and network issues. SOCs focus on identifying security breaches and managing cybersecurity incidents, while NOCs ensure network stability and performance, enabling rapid containment and resolution of incidents. This coordinated effort enhances real-time threat detection, accelerates incident investigation, and optimizes recovery processes to maintain organizational security and uptime.
Tools and Technologies: SOC vs NOC Environments
SOC environments leverage advanced security information and event management (SIEM) systems, threat intelligence platforms, and intrusion detection/prevention systems (IDPS) to monitor and respond to cyber threats in real-time. NOC environments utilize network monitoring tools such as SolarWinds, Nagios, and network performance analyzers to ensure infrastructure uptime and optimize network traffic flow. Both environments employ automation and orchestration technologies, but SOC tools emphasize threat detection and incident response, whereas NOC tools focus on network health and operational continuity.
Organizational Structures: Integrating SOC and NOC
Integrating Security Operations Centers (SOC) and Network Operations Centers (NOC) enhances organizational resilience by fostering real-time collaboration between cybersecurity and network management teams. Shared dashboards, unified incident response protocols, and cross-trained personnel improve threat detection, reduce downtime, and streamline communication across IT infrastructures. This alignment optimizes resource allocation, accelerates remediation times, and strengthens overall security posture within modern enterprise environments.
Choosing Between SOC and NOC for Your Business Needs
Choosing between a Security Operations Center (SOC) and a Network Operations Center (NOC) depends on your business priorities: SOC focuses on proactive cybersecurity threat detection, incident response, and compliance monitoring, while NOC manages network performance, uptime, and infrastructure maintenance. For organizations facing complex cyber threats or regulatory requirements, investing in a SOC enhances threat intelligence and rapid mitigation capabilities. Businesses prioritizing network reliability and performance benefit more from a NOC's continuous monitoring and network health management.
Future Trends in SOC and NOC Operations
Future trends in SOC (Security Operations Center) emphasize the integration of AI-powered threat detection and automated incident response to enhance cybersecurity resilience. NOC (Network Operations Center) operations are increasingly adopting advanced network analytics and real-time monitoring to manage complex infrastructure and prevent outages. Converging SOC and NOC functions through unified platforms drives efficiency, reduces response times, and strengthens overall organizational security posture.
SOC vs NOC Infographic
 difterm.com
difterm.com