SYN Flood attacks exploit the TCP handshake process by sending numerous incomplete connection requests, overwhelming the target system's resources. UDP Flood attacks bombard a target with large volumes of UDP packets, causing network congestion and making services unavailable. Both attacks disrupt network availability but differ in protocols targeted and the attack methods employed.
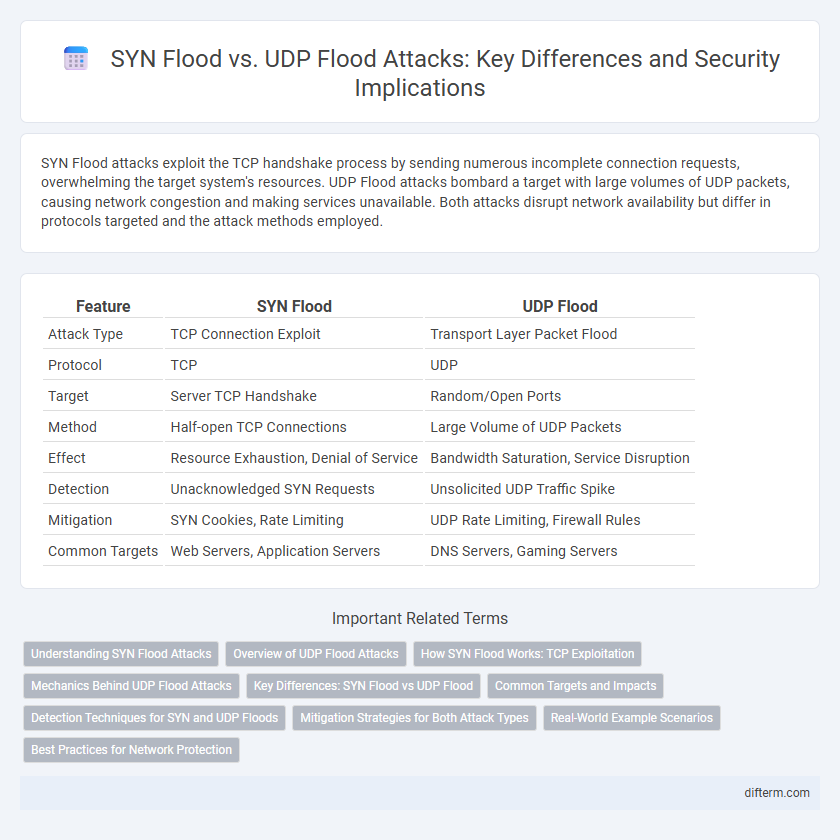
Table of Comparison
| Feature | SYN Flood | UDP Flood |
|---|---|---|
| Attack Type | TCP Connection Exploit | Transport Layer Packet Flood |
| Protocol | TCP | UDP |
| Target | Server TCP Handshake | Random/Open Ports |
| Method | Half-open TCP Connections | Large Volume of UDP Packets |
| Effect | Resource Exhaustion, Denial of Service | Bandwidth Saturation, Service Disruption |
| Detection | Unacknowledged SYN Requests | Unsolicited UDP Traffic Spike |
| Mitigation | SYN Cookies, Rate Limiting | UDP Rate Limiting, Firewall Rules |
| Common Targets | Web Servers, Application Servers | DNS Servers, Gaming Servers |
Understanding SYN Flood Attacks
SYN flood attacks exploit the TCP handshake by sending numerous SYN requests to a target server, overwhelming its ability to allocate resources for legitimate connections. Unlike UDP flood attacks, which saturate the network with UDP packets to consume bandwidth, SYN floods specifically target server-side connection management, causing service disruptions. Effective mitigation requires techniques such as SYN cookies, rate limiting, and firewall filtering to preserve server performance and prevent resource exhaustion.
Overview of UDP Flood Attacks
UDP flood attacks overwhelm a target system by flooding it with User Datagram Protocol packets, exploiting the connectionless nature of UDP to consume bandwidth and processing resources. Attackers typically send large volumes of UDP packets to random or specific ports, causing the target to respond with ICMP Destination Unreachable messages or become saturated with traffic. This type of denial-of-service attack disrupts normal network functionality by exhausting the victim's capacity to manage legitimate traffic effectively.
How SYN Flood Works: TCP Exploitation
SYN Flood attacks exploit the TCP three-way handshake by sending numerous SYN requests without completing the connection, overwhelming the target's server with half-open connections. This tactic depletes server resources, leading to denial of service by preventing legitimate users from establishing connections. Unlike UDP Floods that rely on amplification, SYN Floods specifically target TCP protocol vulnerabilities to disrupt communication.
Mechanics Behind UDP Flood Attacks
UDP flood attacks overwhelm target systems by exploiting the connectionless nature of the User Datagram Protocol, sending vast volumes of UDP packets to random or specified ports. This flood forces the target to repeatedly process incoming packets and generate ICMP Destination Unreachable messages, consuming bandwidth and processing resources. Unlike SYN floods that exploit TCP handshake mechanisms, UDP floods capitalize on UDP's stateless design to create denial-of-service conditions without requiring session initiation.
Key Differences: SYN Flood vs UDP Flood
SYN Flood attacks exploit the TCP handshake by sending numerous SYN requests without completing the connection, overwhelming a target server's resources. UDP Flood attacks bombard the target with large volumes of UDP packets, causing bandwidth saturation and service disruption without requiring connection establishment. Key differences include the protocol exploited--TCP for SYN Floods and UDP for UDP Floods--and the method of resource exhaustion, with SYN Floods targeting connection tables and UDP Floods targeting network bandwidth.
Common Targets and Impacts
SYN Flood attacks commonly target web servers and network infrastructure, overwhelming them with half-open TCP connections that exhaust server resources and disrupt legitimate traffic. UDP Flood attacks focus on consuming bandwidth and processing power by flooding network devices with large volumes of UDP packets, often targeting DNS servers and gaming servers to cause service degradation or outages. Both attack types impair availability but differ in protocol exploitation, with SYN Floods stressing connection tables and UDP Floods saturating network capacity.
Detection Techniques for SYN and UDP Floods
Effective detection of SYN flood attacks leverages techniques such as monitoring abnormal TCP handshake failures, analyzing SYN packet rate anomalies, and employing SYN cookies to mitigate resource exhaustion. UDP flood detection involves monitoring unusually high volumes of UDP packets targeting specific ports, utilizing rate limiting, and implementing flow-based anomaly detection to identify irregular traffic patterns. Combining statistical analysis with real-time traffic monitoring enhances the accuracy of distinguishing legitimate traffic from SYN and UDP flood attack vectors.
Mitigation Strategies for Both Attack Types
SYN Flood mitigation strategies include implementing SYN cookies, increasing backlog queue size, and deploying rate limiting on incoming SYN packets to prevent resource exhaustion. For UDP Flood attacks, effectiveness is achieved through traffic filtering, application of rate limiting on UDP traffic, and using anomaly detection systems to identify and block abnormal traffic patterns. Employing robust firewall rules and intrusion prevention systems enhances resilience against both SYN and UDP flood attacks by monitoring and controlling malicious traffic at the network perimeter.
Real-World Example Scenarios
SYN Flood attacks overwhelm server resources by exploiting the TCP handshake process, often targeting web servers during high-traffic events like product launches or major sales, exemplified by the 2016 Dyn DDoS attack. UDP Flood attacks saturate network bandwidth by sending excessive UDP packets, frequently affecting gaming servers and streaming platforms as seen in the 2018 GitHub DDoS incident. Both attack types disrupt service availability but differ in protocol exploitation and typical target environments.
Best Practices for Network Protection
Implement robust firewall configurations to detect and block SYN flood and UDP flood attacks by limiting half-open TCP connections and filtering anomalous UDP traffic patterns. Employ rate limiting and intrusion prevention systems (IPS) to mitigate excessive traffic volumes that characterize SYN and UDP flood attacks. Regularly update network devices and utilize behavior-based anomaly detection to enhance responsiveness against evolving distributed denial-of-service (DDoS) threats.
SYN Flood vs UDP Flood Infographic
 difterm.com
difterm.com