Bug bounty programs leverage a wide network of ethical hackers to identify security vulnerabilities in real-world scenarios, providing continuous and diverse testing. Penetration testing offers a controlled, comprehensive assessment by skilled professionals simulating specific attack vectors within a fixed timeframe. Combining both approaches enhances overall security posture by covering broad, unexpected threats and in-depth, targeted vulnerabilities.
Table of Comparison
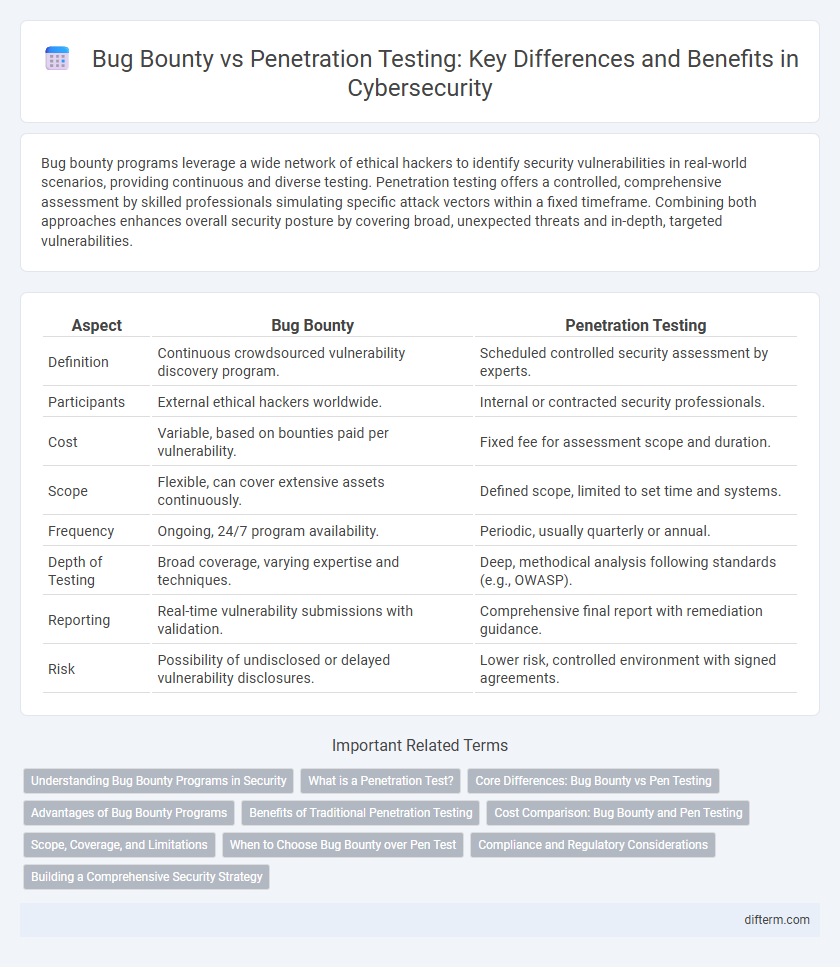
| Aspect | Bug Bounty | Penetration Testing |
|---|---|---|
| Definition | Continuous crowdsourced vulnerability discovery program. | Scheduled controlled security assessment by experts. |
| Participants | External ethical hackers worldwide. | Internal or contracted security professionals. |
| Cost | Variable, based on bounties paid per vulnerability. | Fixed fee for assessment scope and duration. |
| Scope | Flexible, can cover extensive assets continuously. | Defined scope, limited to set time and systems. |
| Frequency | Ongoing, 24/7 program availability. | Periodic, usually quarterly or annual. |
| Depth of Testing | Broad coverage, varying expertise and techniques. | Deep, methodical analysis following standards (e.g., OWASP). |
| Reporting | Real-time vulnerability submissions with validation. | Comprehensive final report with remediation guidance. |
| Risk | Possibility of undisclosed or delayed vulnerability disclosures. | Lower risk, controlled environment with signed agreements. |
Understanding Bug Bounty Programs in Security
Bug bounty programs enable organizations to crowdsource vulnerability detection by rewarding independent security researchers for identifying and responsibly disclosing security flaws. These programs complement traditional penetration testing by providing continuous, real-world testing from diverse perspectives and skill sets. Effective bug bounty initiatives broaden the security landscape coverage and accelerate vulnerability remediation, enhancing overall security posture.
What is a Penetration Test?
A penetration test, or pen test, is a simulated cyberattack against a computer system to identify vulnerabilities before malicious hackers exploit them. It involves authorized professionals systematically probing networks, applications, and devices to assess security weaknesses, providing detailed reports with remediation strategies. Pen tests follow strict methodologies such as OWASP or NIST guidelines to ensure comprehensive evaluation and compliance with industry standards.
Core Differences: Bug Bounty vs Pen Testing
Bug bounty programs leverage a diverse pool of ethical hackers to identify vulnerabilities in real-world environments on an ongoing basis, providing continuous security insights and cost-effective scalability. Penetration testing involves a structured, time-bound engagement by certified professionals who simulate attacks to evaluate specific systems' security posture comprehensively. Core differences include the scope flexibility, with bug bounties often covering broader attack surfaces dynamically, whereas pen tests offer deep, controlled analysis with detailed reporting and compliance alignment.
Advantages of Bug Bounty Programs
Bug bounty programs leverage a diverse global community of ethical hackers to identify vulnerabilities across a wide range of systems and applications, offering continuous, real-time security testing beyond scheduled penetration tests. These programs often result in faster discovery of zero-day exploits and novel attack vectors due to the varied expertise and creativity of participants. Companies benefit from cost-effective, scalable vulnerability detection with payouts linked directly to the severity of identified issues, aligning incentives for thorough and responsible disclosure.
Benefits of Traditional Penetration Testing
Traditional penetration testing offers comprehensive, tailored assessments that simulate real-world cyberattacks to identify vulnerabilities before adversaries exploit them. It provides in-depth analysis of complex systems, enabling organizations to prioritize remediation efforts based on risk severity and business impact. Pen tests deliver actionable insights through expert evaluation, improving overall cybersecurity posture and compliance with industry regulations.
Cost Comparison: Bug Bounty and Pen Testing
Bug bounty programs often provide cost-effective security testing by leveraging a diverse pool of ethical hackers who are paid based on valid findings, reducing upfront expenses compared to traditional penetration testing engagements. Penetration testing typically involves a fixed fee for a predefined scope, resulting in predictable costs but potentially higher prices due to manual, in-depth analysis by specialized security experts. Organizations can optimize their security budget by balancing the variable costs and extensive coverage of bug bounty programs against the structured, comprehensive nature of professional penetration testing.
Scope, Coverage, and Limitations
Bug bounty programs offer a broad and dynamic scope, leveraging a diverse pool of ethical hackers to uncover real-world vulnerabilities across web applications, APIs, and software, often providing ongoing, continuous coverage. Penetration tests have a more defined and limited scope, typically focusing on specific systems or networks for a fixed duration, delivering comprehensive but time-bound assessments. Limitations of bug bounties include unpredictable results and varying quality of findings, while penetration tests may miss emerging threats due to their periodic nature and fixed scope.
When to Choose Bug Bounty over Pen Test
Choose a bug bounty program over a penetration test when seeking continuous, real-world vulnerability discovery by diverse ethical hackers at a scalable cost. Bug bounty platforms provide ongoing security testing with a wider range of techniques and perspectives, ideal for organizations needing dynamic threat exposure rather than point-in-time assessments. This approach is particularly effective for internet-facing applications with high user interaction and evolving attack surfaces.
Compliance and Regulatory Considerations
Bug bounty programs enable continuous vulnerability discovery by crowdsourcing security testing, aligning well with dynamic compliance requirements such as PCI DSS and HIPAA that mandate regular security assessments. Penetration testing offers structured, scheduled evaluations that satisfy regulatory frameworks requiring documented, time-bound security audits, including SOC 2 and ISO 27001 standards. Combining both approaches helps organizations achieve comprehensive compliance by meeting diverse regulatory mandates for proactive and periodic security validation.
Building a Comprehensive Security Strategy
Bug bounty programs leverage diverse external researchers to identify vulnerabilities continuously, uncovering real-world exploits often missed by traditional methods. Penetration testing provides structured, in-depth assessments by certified experts simulating targeted attacks to evaluate security posture at specific points in time. Combining bug bounty initiatives with regular pen tests fosters a comprehensive security strategy, enhancing threat detection, risk mitigation, and overall resilience against evolving cyber threats.
Bug bounty vs Pen test Infographic
 difterm.com
difterm.com