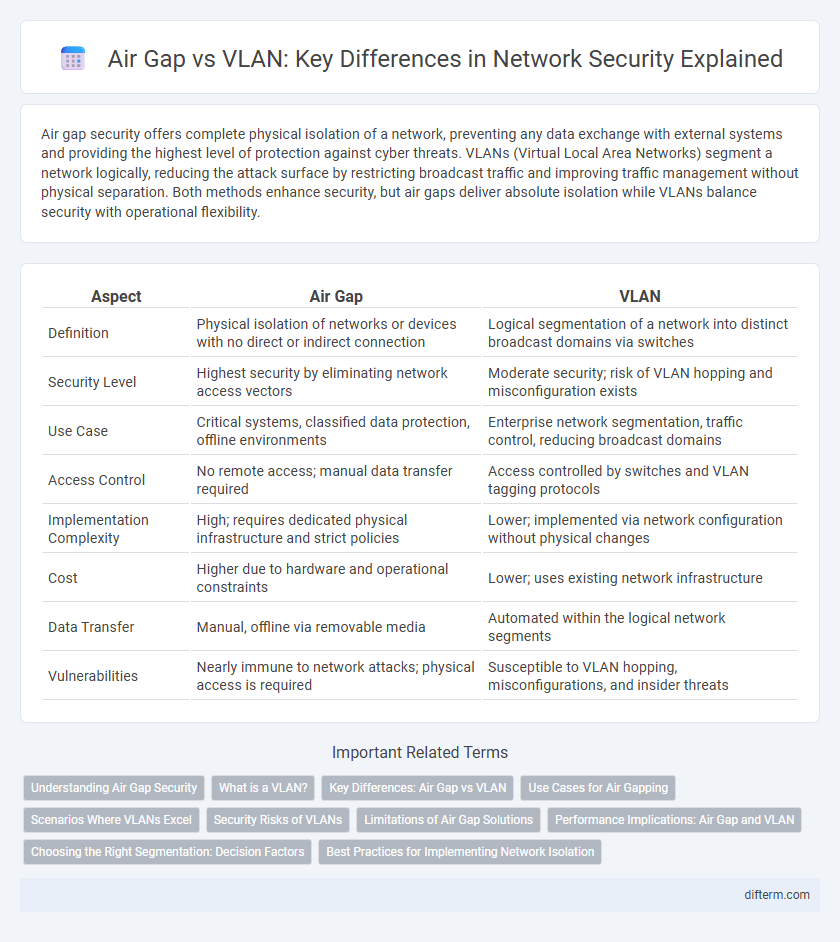
Air gap security offers complete physical isolation of a network, preventing any data exchange with external systems and providing the highest level of protection against cyber threats. VLANs (Virtual Local Area Networks) segment a network logically, reducing the attack surface by restricting broadcast traffic and improving traffic management without physical separation. Both methods enhance security, but air gaps deliver absolute isolation while VLANs balance security with operational flexibility.
Table of Comparison
| Aspect | Air Gap | VLAN |
|---|---|---|
| Definition | Physical isolation of networks or devices with no direct or indirect connection | Logical segmentation of a network into distinct broadcast domains via switches |
| Security Level | Highest security by eliminating network access vectors | Moderate security; risk of VLAN hopping and misconfiguration exists |
| Use Case | Critical systems, classified data protection, offline environments | Enterprise network segmentation, traffic control, reducing broadcast domains |
| Access Control | No remote access; manual data transfer required | Access controlled by switches and VLAN tagging protocols |
| Implementation Complexity | High; requires dedicated physical infrastructure and strict policies | Lower; implemented via network configuration without physical changes |
| Cost | Higher due to hardware and operational constraints | Lower; uses existing network infrastructure |
| Data Transfer | Manual, offline via removable media | Automated within the logical network segments |
| Vulnerabilities | Nearly immune to network attacks; physical access is required | Susceptible to VLAN hopping, misconfigurations, and insider threats |
Understanding Air Gap Security
Air gap security isolates critical systems by physically disconnecting them from unsecured networks, eliminating remote access risks and preventing cyberattacks that traverse network segments. Unlike VLANs, which segment traffic within a connected network to control access and limit exposure, air gaps create an absolute barrier, ensuring no digital communication between secured and unsecured environments. This approach is essential for protecting highly sensitive data in environments like industrial control systems, military networks, and critical infrastructure.
What is a VLAN?
A VLAN (Virtual Local Area Network) is a network segmentation technology that logically divides a physical network into multiple distinct broadcast domains to enhance security and performance. By isolating groups of devices within the same physical infrastructure, VLANs restrict unauthorized access and reduce the risk of broadcast storms. VLANs enable granular control over network traffic, supporting secure communication between devices based on policies rather than physical location.
Key Differences: Air Gap vs VLAN
Air Gap security isolates systems physically, preventing any network connection and eliminating digital attack vectors, while VLAN (Virtual Local Area Network) segments a network logically to control traffic within the same physical infrastructure. Air Gaps provide ultimate protection by completely severing communication between secure and non-secure environments, whereas VLANs rely on software-based segmentation and can be vulnerable to misconfigurations or advanced network attacks. Key differences include the physical separation of Air Gap versus the virtual separation of VLAN, impacting the level of security and complexity in network management.
Use Cases for Air Gapping
Air gapping is essential for isolating critical systems from unsecured networks, especially in high-security environments like military and financial institutions to prevent cyber breaches. It provides physical separation that ensures sensitive data remains offline, effectively protecting against remote hacking attempts and malware infiltration. Compared to VLANs, air gaps are preferred for safeguarding classified information and controlling access to industrial control systems where network connectivity poses unacceptable risks.
Scenarios Where VLANs Excel
VLANs excel in scenarios requiring segmented network traffic within the same physical infrastructure, enabling efficient resource sharing while maintaining security boundaries. They support dynamic and scalable environments like large enterprises where flexible user group isolation and traffic management are essential. VLANs also facilitate streamlined network access control, allowing administrators to enforce policies without physical separation.
Security Risks of VLANs
VLANs, while useful for network segmentation, present significant security risks due to their reliance on shared physical infrastructure, making them vulnerable to VLAN hopping attacks and misconfigurations that can lead to unauthorized access. Unlike air gaps, which provide physical isolation between networks, VLANs depend on protocols that can be exploited, allowing attackers to bypass segmentation controls. The complexity of VLAN management increases the risk of human error, potentially exposing sensitive data to internal and external threats within the same physical network environment.
Limitations of Air Gap Solutions
Air gap solutions provide physical isolation by disconnecting networks from external connections, significantly reducing exposure to remote cyberattacks. However, their limitations include operational complexity, as data transfer requires manual intervention via removable media, increasing risks of human error and introducing potential malware infections. Air gaps also hinder real-time data monitoring and automated security updates, limiting responsiveness to emerging threats compared to VLAN segmentation.
Performance Implications: Air Gap and VLAN
Air gap networks deliver superior security by physically isolating systems, eliminating data transfer risks but often resulting in limited real-time communication and slower operational workflows. VLANs offer flexible segmentation within a shared infrastructure, enabling faster data exchange and streamlined performance but potentially exposing networks to lateral movement if security controls fail. Optimal security designs balance air gap isolation for critical assets with VLAN efficiency, minimizing performance bottlenecks while maintaining robust threat containment.
Choosing the Right Segmentation: Decision Factors
Choosing between air gap and VLAN segmentation depends on the security requirements and network complexity of an organization. Air gap provides complete physical isolation, ideal for highly sensitive or critical systems that require maximum protection against cyber threats. VLANs offer logical segmentation with ease of management and scalability, suitable for environments needing flexible access controls and efficient traffic management without compromising overall network performance.
Best Practices for Implementing Network Isolation
Air gap implementation provides the highest level of network isolation by physically separating secure systems from unsecured networks, effectively eliminating any direct digital communication paths. VLAN segmentation enhances security by logically isolating network traffic within the same physical infrastructure, employing access control lists (ACLs) and strict policy enforcement to minimize lateral movement and reduce attack surfaces. Best practices for network isolation include comprehensive access control, rigorous monitoring, regular patching, and adherence to least privilege principles to ensure robust defense-in-depth strategies.
Air Gap vs VLAN Infographic
 difterm.com
difterm.com