Static Application Security Testing (SAST) analyzes source code at rest to identify vulnerabilities early in the development lifecycle, offering precise detection of coding errors without executing the program. Dynamic Application Security Testing (DAST) evaluates running applications by simulating attacks to uncover security weaknesses in real-time environments, providing insights into runtime behavior and exposure to external threats. Combining both approaches enhances overall security posture by addressing flaws from code origin to active deployment.
Table of Comparison
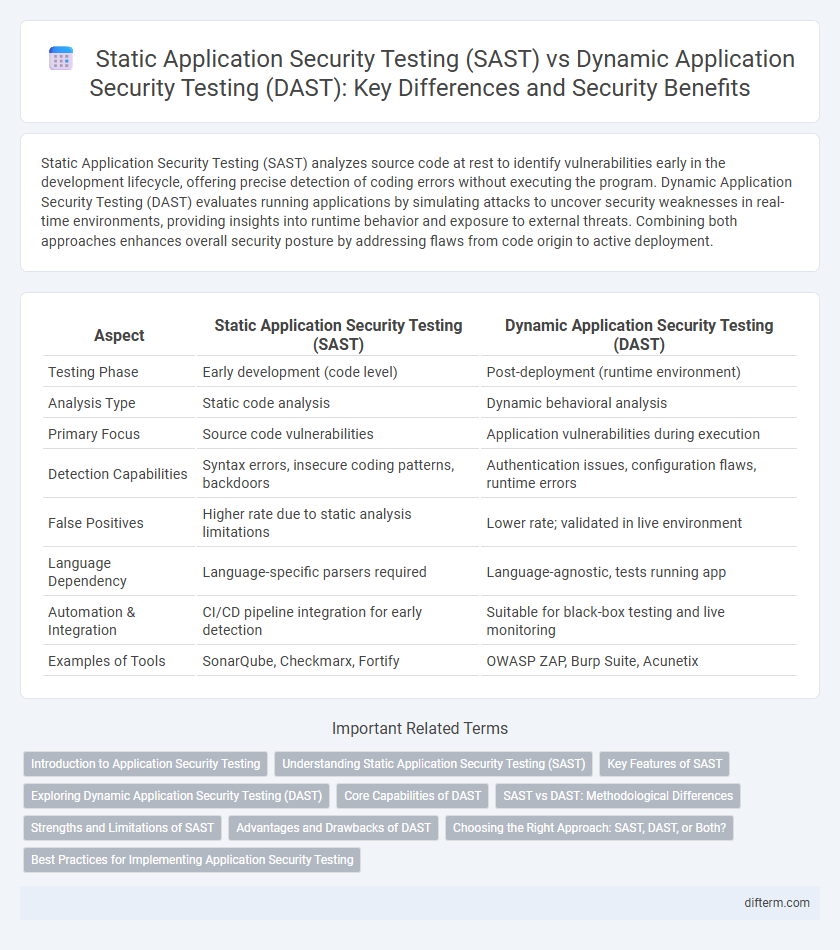
| Aspect | Static Application Security Testing (SAST) | Dynamic Application Security Testing (DAST) |
|---|---|---|
| Testing Phase | Early development (code level) | Post-deployment (runtime environment) |
| Analysis Type | Static code analysis | Dynamic behavioral analysis |
| Primary Focus | Source code vulnerabilities | Application vulnerabilities during execution |
| Detection Capabilities | Syntax errors, insecure coding patterns, backdoors | Authentication issues, configuration flaws, runtime errors |
| False Positives | Higher rate due to static analysis limitations | Lower rate; validated in live environment |
| Language Dependency | Language-specific parsers required | Language-agnostic, tests running app |
| Automation & Integration | CI/CD pipeline integration for early detection | Suitable for black-box testing and live monitoring |
| Examples of Tools | SonarQube, Checkmarx, Fortify | OWASP ZAP, Burp Suite, Acunetix |
Introduction to Application Security Testing
Static Application Security Testing (SAST) analyzes source code or binaries for vulnerabilities without executing the program, enabling early detection of security flaws during development. Dynamic Application Security Testing (DAST) examines running applications in real-time to identify runtime vulnerabilities and behavioral issues. Both SAST and DAST are essential components of a comprehensive application security testing strategy, ensuring robust protection against potential threats.
Understanding Static Application Security Testing (SAST)
Static Application Security Testing (SAST) analyzes source code, bytecode, or binary files to identify vulnerabilities without executing the program, enabling early detection of security flaws during the development cycle. It employs techniques like pattern matching, data flow analysis, and control flow analysis to uncover coding errors, injection flaws, and insecure configurations. Integrating SAST tools into Continuous Integration/Continuous Deployment (CI/CD) pipelines enhances code quality and compliance by providing real-time feedback to developers before deployment.
Key Features of SAST
Static Application Security Testing (SAST) examines source code, bytecode, or binary files early in the software development lifecycle to identify vulnerabilities such as SQL injection, cross-site scripting, and buffer overflows. Key features of SAST include its ability to provide detailed insights into code quality, support for multiple programming languages, and integration with IDEs and CI/CD pipelines for continuous security feedback. It performs thorough code analysis without executing the application, enabling developers to detect security flaws before runtime and reduce remediation costs.
Exploring Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) analyzes running applications by simulating external attacks to identify vulnerabilities such as SQL injection, cross-site scripting, and authentication issues. Unlike Static Application Security Testing (SAST), which examines source code, DAST evaluates the application's behavior during execution, offering real-time detection of security flaws in a production-like environment. This approach enables security teams to discover runtime vulnerabilities that static analysis might miss, enhancing overall application security posture.
Core Capabilities of DAST
Dynamic Application Security Testing (DAST) excels in identifying runtime vulnerabilities by simulating external attacks on live applications, enabling detection of issues like SQL injection, cross-site scripting, and authentication flaws. DAST tools analyze application behavior and responses in real-time, providing insights into security weaknesses that occur during execution. This core capability allows security teams to uncover vulnerabilities that static analysis might miss, particularly those related to runtime environment and interactions.
SAST vs DAST: Methodological Differences
Static Application Security Testing (SAST) analyzes source code, bytecode, or binaries early in the software development lifecycle to identify vulnerabilities such as SQL injection and buffer overflows without executing the program. Dynamic Application Security Testing (DAST) evaluates running applications by simulating external attacks to detect runtime issues like authentication failures and session management flaws. SAST emphasizes code-level security during development, while DAST focuses on identifying exploitable vulnerabilities in live environments through black-box testing techniques.
Strengths and Limitations of SAST
Static Application Security Testing (SAST) excels at identifying vulnerabilities early in the software development lifecycle by analyzing source code for security flaws such as SQL injection, cross-site scripting, and buffer overflows without executing the program. It offers comprehensive coverage of all code paths but can produce false positives and struggle with detecting runtime-specific issues like authentication or session management flaws. SAST is most effective for enforcing coding standards and improving code quality, though it requires access to source code and may miss vulnerabilities exposed only during application execution.
Advantages and Drawbacks of DAST
Dynamic Application Security Testing (DAST) identifies vulnerabilities in running applications by simulating external attacks, offering real-time detection of runtime issues and security flaws that static analysis might miss. Advantages include the ability to test the application in its operational environment without access to source code, providing insights into authentication, server configuration, and runtime behavior. However, DAST has drawbacks such as limited code coverage, potential false positives, and challenges in scanning complex or highly dynamic web applications effectively.
Choosing the Right Approach: SAST, DAST, or Both?
Choosing the right approach between Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) depends on the development lifecycle and security requirements. SAST analyzes source code early to detect vulnerabilities before deployment, while DAST tests running applications to identify runtime issues. Combining both SAST and DAST provides comprehensive coverage by addressing code flaws and runtime threats, enhancing overall application security.
Best Practices for Implementing Application Security Testing
Static Application Security Testing (SAST) involves analyzing source code early in the development lifecycle to identify vulnerabilities before deployment, enabling developers to fix issues promptly. Dynamic Application Security Testing (DAST) assesses the running application in a runtime environment, simulating attacks to detect security flaws that manifest during execution. Best practices for implementing application security testing include integrating SAST tools within continuous integration pipelines for early detection, complementing with regular DAST scans for runtime analysis, and ensuring robust collaboration between development and security teams to promptly address identified vulnerabilities.
Static Application Security Testing vs Dynamic Application Security Testing Infographic
 difterm.com
difterm.com