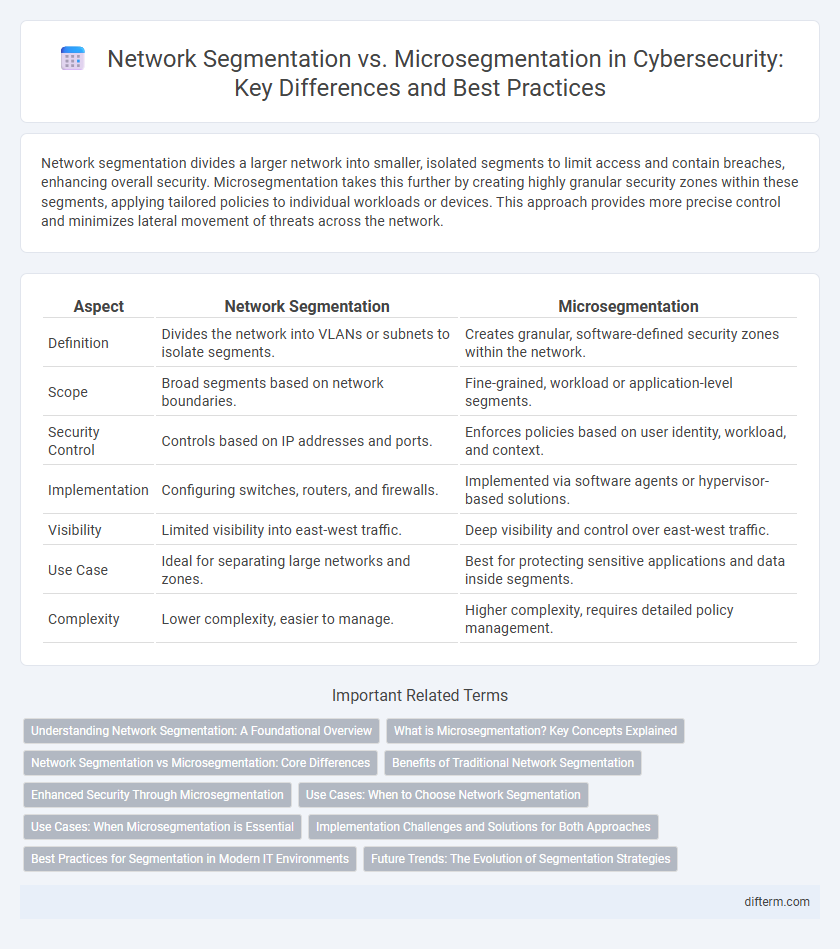
Network segmentation divides a larger network into smaller, isolated segments to limit access and contain breaches, enhancing overall security. Microsegmentation takes this further by creating highly granular security zones within these segments, applying tailored policies to individual workloads or devices. This approach provides more precise control and minimizes lateral movement of threats across the network.
Table of Comparison
| Aspect | Network Segmentation | Microsegmentation |
|---|---|---|
| Definition | Divides the network into VLANs or subnets to isolate segments. | Creates granular, software-defined security zones within the network. |
| Scope | Broad segments based on network boundaries. | Fine-grained, workload or application-level segments. |
| Security Control | Controls based on IP addresses and ports. | Enforces policies based on user identity, workload, and context. |
| Implementation | Configuring switches, routers, and firewalls. | Implemented via software agents or hypervisor-based solutions. |
| Visibility | Limited visibility into east-west traffic. | Deep visibility and control over east-west traffic. |
| Use Case | Ideal for separating large networks and zones. | Best for protecting sensitive applications and data inside segments. |
| Complexity | Lower complexity, easier to manage. | Higher complexity, requires detailed policy management. |
Understanding Network Segmentation: A Foundational Overview
Network segmentation divides a computer network into multiple subnetworks to improve security and performance by containing potential breaches within isolated zones. By limiting access control and traffic flow between segments, it reduces the attack surface and prevents lateral movement of threats across the network. Foundational network segmentation relies on VLANs, firewalls, and access control lists (ACLs) to enforce boundaries and monitor traffic effectively.
What is Microsegmentation? Key Concepts Explained
Microsegmentation is an advanced security technique that divides a network into highly granular segments to enforce strict access controls at the workload or application level. It uses policies based on identity, context, and behavior to isolate resources and prevent lateral movement of threats within the network. By leveraging software-defined networking and automation, microsegmentation enhances visibility, reduces attack surfaces, and improves compliance with security standards.
Network Segmentation vs Microsegmentation: Core Differences
Network segmentation divides a network into larger, distinct zones to contain breaches and improve performance, while microsegmentation applies granular security controls within these zones, isolating individual workloads or devices. Unlike network segmentation, which relies on traditional firewalls and VLANs, microsegmentation uses software-defined policies and identity-based controls for precise access management. This core difference enables microsegmentation to reduce lateral movement of threats more effectively by enforcing strict, context-aware security measures at the workload level.
Benefits of Traditional Network Segmentation
Traditional network segmentation enhances security by dividing a large network into distinct subnetworks, limiting the spread of potential cyber threats and simplifying traffic management. It improves performance by isolating network traffic, reducing congestion, and enabling more efficient resource allocation. Furthermore, segmentation supports regulatory compliance by containing sensitive data within specific zones, minimizing the attack surface and exposure risks.
Enhanced Security Through Microsegmentation
Microsegmentation offers enhanced security by creating granular network segments down to the individual workload or application level, significantly reducing the attack surface compared to traditional network segmentation. This approach enforces strict, context-aware security policies that limit lateral movement of threats within the network, thereby containing breaches more effectively. Implementing microsegmentation ensures tighter access controls and improved visibility into network traffic, which are critical for protecting sensitive data in complex, hybrid cloud environments.
Use Cases: When to Choose Network Segmentation
Network segmentation is ideal for isolating large network zones such as separating guest Wi-Fi from corporate resources, ensuring broad control over traffic flow and reducing attack surfaces in enterprise environments. It is particularly effective for compliance requirements like PCI-DSS or HIPAA, where clear boundaries between network segments simplify auditing and regulatory adherence. Choose network segmentation when managing traffic at a macro level to contain malware outbreaks and enforce broad security policies across distinct business units or departments.
Use Cases: When Microsegmentation is Essential
Microsegmentation is essential in environments requiring granular security controls, such as cloud-native applications and zero-trust architectures, where isolating workloads at the individual workload or container level prevents lateral movement of threats. Unlike traditional network segmentation that divides networks into larger zones, microsegmentation enforces policies based on user identity, application, or data sensitivity, providing superior protection for sensitive assets in highly dynamic and distributed IT infrastructures. Use cases include protecting critical financial data, securing multi-tenant data centers, and enforcing compliance in healthcare environments with strict regulatory requirements.
Implementation Challenges and Solutions for Both Approaches
Network segmentation implementation faces challenges such as managing complex VLAN configurations and ensuring proper access controls across physical devices, which can be mitigated by automated network management tools and clear policy enforcement. Microsegmentation involves granular workload-level controls, leading to difficulties in visibility and consistent policy application, addressed through software-defined security platforms and continuous monitoring using endpoint detection and response (EDR) solutions. Both approaches require careful integration with existing infrastructure and ongoing adjustment to evolving threat landscapes to maintain robust security posture.
Best Practices for Segmentation in Modern IT Environments
Effective network segmentation involves dividing a large network into smaller, isolated segments to limit lateral movement of threats and enhance security posture. Microsegmentation takes this approach further by creating granular, software-defined segments around individual workloads or applications, offering precise control and reducing attack surfaces. Best practices emphasize implementing zero-trust principles, continuous monitoring, and automation to adapt dynamically to changing environments while maintaining strict access controls and minimizing risks in modern IT infrastructures.
Future Trends: The Evolution of Segmentation Strategies
Network segmentation is evolving beyond traditional perimeter-based models, adopting microsegmentation to enhance security granularity within data centers and cloud environments. Future trends emphasize AI-driven automation and real-time analytics to dynamically adjust segmentation policies based on threat intelligence and traffic behavior. This shift supports zero-trust architectures by isolating workloads and minimizing lateral movement risks in increasingly complex hybrid networks.
Network Segmentation vs Microsegmentation Infographic
 difterm.com
difterm.com