White Hat Hackers use their skills ethically to identify security vulnerabilities and protect systems from cyber threats, working within legal boundaries to strengthen digital defenses. Black Hat Hackers exploit these vulnerabilities maliciously, aiming to steal data, cause damage, or disrupt services for personal gain or malicious intent. Understanding the distinction between these two types of hackers is crucial for enhancing cybersecurity and safeguarding sensitive information.
Table of Comparison
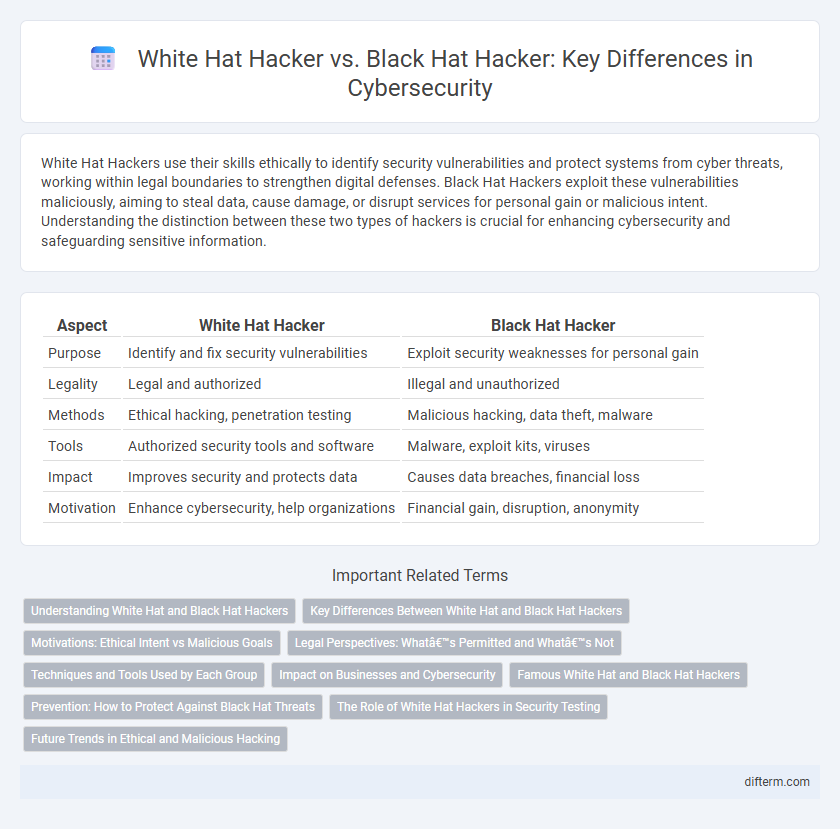
| Aspect | White Hat Hacker | Black Hat Hacker |
|---|---|---|
| Purpose | Identify and fix security vulnerabilities | Exploit security weaknesses for personal gain |
| Legality | Legal and authorized | Illegal and unauthorized |
| Methods | Ethical hacking, penetration testing | Malicious hacking, data theft, malware |
| Tools | Authorized security tools and software | Malware, exploit kits, viruses |
| Impact | Improves security and protects data | Causes data breaches, financial loss |
| Motivation | Enhance cybersecurity, help organizations | Financial gain, disruption, anonymity |
Understanding White Hat and Black Hat Hackers
White hat hackers, also known as ethical hackers, use their advanced cybersecurity skills to identify vulnerabilities and strengthen system defenses legally and with permission. Black hat hackers exploit these same weaknesses for malicious purposes such as data theft, financial gain, or disrupting services without authorization. Understanding the key differences between these hacker types is crucial for developing effective security strategies and protecting digital assets.
Key Differences Between White Hat and Black Hat Hackers
White Hat hackers use their skills to identify security vulnerabilities and protect systems from cyber threats, operating within legal and ethical boundaries. Black Hat hackers exploit weaknesses for personal gain, causing damage or stealing sensitive information without authorization. The key differences lie in intent, legality, and impact on cybersecurity: White Hats aim to improve security, while Black Hats seek to compromise it.
Motivations: Ethical Intent vs Malicious Goals
White hat hackers are driven by ethical intent, aiming to identify and fix security vulnerabilities to protect organizations and users from cyber threats. In contrast, black hat hackers pursue malicious goals such as data theft, system disruption, and unauthorized access for personal gain or harm. The fundamental difference lies in their motivations: white hats enhance cybersecurity, while black hats exploit weaknesses for criminal purposes.
Legal Perspectives: What’s Permitted and What’s Not
White hat hackers operate within legal boundaries by obtaining explicit authorization to identify and fix security vulnerabilities, ensuring compliance with cybersecurity laws and regulations such as the Computer Fraud and Abuse Act (CFAA). In contrast, black hat hackers engage in unauthorized access, data theft, and system damage, actions that are criminal offenses under laws like the CFAA and various international cybercrime statutes. Legal frameworks strictly differentiate white hat activities, often protected under employment contracts or bug bounty programs, from black hat intrusions that face prosecution and severe penalties.
Techniques and Tools Used by Each Group
White Hat hackers utilize authorized penetration testing tools such as Metasploit, Nmap, and Wireshark to identify and fix security vulnerabilities while adhering to ethical guidelines. Black Hat hackers exploit malware, ransomware, keyloggers, and zero-day vulnerabilities to breach systems, steal data, and cause damage for financial or political gain. The contrasting techniques emphasize ethical hacking versus malicious exploitation within cybersecurity frameworks.
Impact on Businesses and Cybersecurity
White hat hackers enhance business cybersecurity by identifying system vulnerabilities and implementing preventative measures that protect sensitive data and maintain operational integrity. Black hat hackers exploit these vulnerabilities to steal information, cause financial loss, and damage company reputation, often resulting in costly recovery efforts and regulatory penalties. Investing in white hat expertise strengthens a business's defense against cyber threats, reducing the risk of breaches and ensuring compliance with security standards.
Famous White Hat and Black Hat Hackers
Famous white hat hackers such as Kevin Mitnick and Joanna Rutkowska have made significant contributions to cybersecurity by identifying vulnerabilities and improving system defenses ethically. In contrast, notorious black hat hackers like Adrian Lamo and Gary McKinnon exploited security flaws for unauthorized access, often causing substantial damage or data breaches. These contrasting figures highlight the critical roles played by ethical hackers in protecting digital infrastructure against malicious cyber threats.
Prevention: How to Protect Against Black Hat Threats
Preventing Black Hat threats requires implementing multi-layered cybersecurity measures, including regular software updates, strong firewalls, and continuous network monitoring. Employing White Hat hackers for ethical penetration testing helps identify vulnerabilities before criminals exploit them. Employee training on phishing and social engineering attacks further strengthens defenses against unauthorized access and data breaches.
The Role of White Hat Hackers in Security Testing
White hat hackers play a critical role in security testing by identifying vulnerabilities within systems before malicious actors can exploit them. Their ethical hacking practices involve authorized penetration testing, vulnerability assessments, and continuous monitoring to strengthen an organization's cybersecurity posture. By simulating real-world attacks, white hat hackers help prevent data breaches and protect sensitive information from black hat hackers.
Future Trends in Ethical and Malicious Hacking
Future trends in ethical hacking emphasize the integration of artificial intelligence and machine learning to proactively identify vulnerabilities and strengthen cybersecurity defenses. Conversely, black hat hackers increasingly exploit advanced technologies such as deepfake tools and autonomous malware to launch sophisticated cyberattacks, challenging traditional security measures. The evolving landscape demands continuous innovation in white hat strategies and regulatory frameworks to mitigate the escalating risks posed by malicious hacking activities.
White Hat Hacker vs Black Hat Hacker Infographic
 difterm.com
difterm.com