Cyber Threat Intelligence involves gathering and analyzing data about potential cyber threats to proactively protect systems and networks. Threat Hunting is a proactive security practice where analysts actively search for hidden threats within an organization's environment, often using insights from Cyber Threat Intelligence. Combining both approaches enhances the ability to detect, respond to, and mitigate advanced cyber attacks effectively.
Table of Comparison
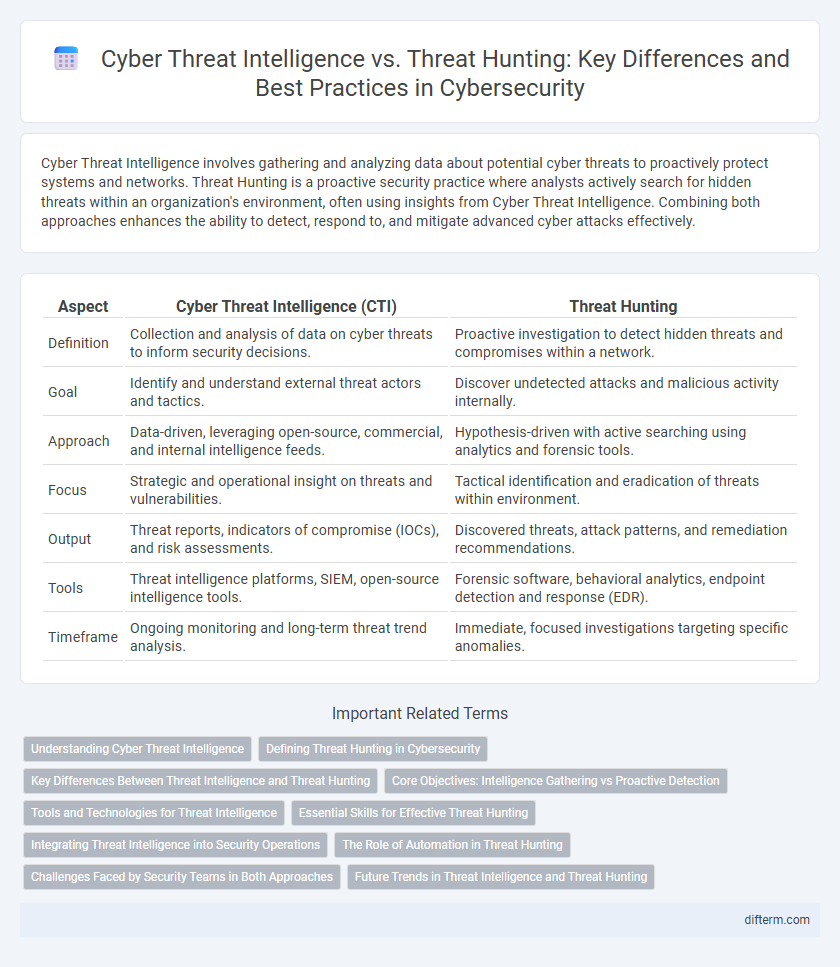
| Aspect | Cyber Threat Intelligence (CTI) | Threat Hunting |
|---|---|---|
| Definition | Collection and analysis of data on cyber threats to inform security decisions. | Proactive investigation to detect hidden threats and compromises within a network. |
| Goal | Identify and understand external threat actors and tactics. | Discover undetected attacks and malicious activity internally. |
| Approach | Data-driven, leveraging open-source, commercial, and internal intelligence feeds. | Hypothesis-driven with active searching using analytics and forensic tools. |
| Focus | Strategic and operational insight on threats and vulnerabilities. | Tactical identification and eradication of threats within environment. |
| Output | Threat reports, indicators of compromise (IOCs), and risk assessments. | Discovered threats, attack patterns, and remediation recommendations. |
| Tools | Threat intelligence platforms, SIEM, open-source intelligence tools. | Forensic software, behavioral analytics, endpoint detection and response (EDR). |
| Timeframe | Ongoing monitoring and long-term threat trend analysis. | Immediate, focused investigations targeting specific anomalies. |
Understanding Cyber Threat Intelligence
Cyber Threat Intelligence involves the systematic collection and analysis of data related to cyber threats, enabling organizations to predict, identify, and mitigate potential attacks before they occur. It focuses on gathering actionable insights from various sources such as malware analysis, threat actor profiles, and attack vectors to strengthen cybersecurity defenses. Understanding Cyber Threat Intelligence empowers security teams to prioritize vulnerabilities and allocate resources effectively to prevent future breaches.
Defining Threat Hunting in Cybersecurity
Threat hunting in cybersecurity involves proactively searching through networks and systems to detect advanced threats that evade automated defenses. It complements cyber threat intelligence by using insights and data to identify hidden indicators of compromise or anomalous activities. This hands-on approach enables organizations to uncover stealthy and sophisticated cyber attacks before they result in significant damage.
Key Differences Between Threat Intelligence and Threat Hunting
Cyber Threat Intelligence involves the systematic collection and analysis of data on emerging cyber threats, focusing on identifying indicators of compromise, threat actor tactics, and potential vulnerabilities to enhance proactive defense strategies. Threat Hunting is a proactive, iterative process where security teams actively search within networks to detect and mitigate hidden threats and anomalies that have bypassed existing security measures. The key difference lies in Cyber Threat Intelligence providing contextual, external threat data for informed decision-making, while Threat Hunting emphasizes direct, internal investigation to uncover real-time threats undetected by automated systems.
Core Objectives: Intelligence Gathering vs Proactive Detection
Cyber Threat Intelligence focuses on intelligence gathering by collecting, analyzing, and disseminating data about existing and emerging cyber threats to inform strategic defense decisions. Threat Hunting prioritizes proactive detection through the systematic search for hidden threats and adversaries within networks before they cause harm. The core objective of intelligence gathering is to provide actionable insights, while proactive detection aims to identify and mitigate threats in real-time.
Tools and Technologies for Threat Intelligence
Cyber Threat Intelligence relies on platforms such as Recorded Future, Anomali, and ThreatConnect to aggregate, analyze, and disseminate real-time data from multiple sources, enabling proactive identification of emerging cyber threats. These tools utilize machine learning algorithms, indicator of compromise (IoC) databases, and natural language processing to enhance contextual understanding and predictive capabilities. Threat hunting complements these technologies by using advanced endpoint detection and response (EDR) solutions like CrowdStrike Falcon or Carbon Black to proactively search for stealthy threats within network environments.
Essential Skills for Effective Threat Hunting
Effective threat hunting requires advanced analytical skills and deep knowledge of network protocols, malware behavior, and attack vectors to proactively identify hidden threats. Mastery of data analysis tools like SIEM (Security Information and Event Management) and proficiency in scripting languages such as Python enable hunters to automate detection and uncover anomalies across large datasets. Continuous learning in adversary tactics, techniques, and procedures (TTPs) combined with strong incident response capabilities ensures timely and precise threat identification beyond conventional cyber threat intelligence feeds.
Integrating Threat Intelligence into Security Operations
Integrating Cyber Threat Intelligence into Security Operations enhances threat hunting by providing actionable data on adversary tactics, techniques, and procedures (TTPs). Threat intelligence feeds enable security analysts to prioritize alerts and focus on relevant indicators of compromise (IOCs), reducing detection time. Leveraging real-time intelligence improves the accuracy of threat hunting engagements and strengthens overall incident response capabilities.
The Role of Automation in Threat Hunting
Automation in threat hunting significantly enhances the speed and accuracy of detecting cyber threats by continuously analyzing vast amounts of data and identifying anomalous behavior patterns. Integrating machine learning algorithms and automated tools reduces manual efforts, enabling security teams to proactively uncover sophisticated threats before they cause harm. This role of automation bridges gaps between Cyber Threat Intelligence gathering and hands-on threat hunting, improving overall cyber defense effectiveness.
Challenges Faced by Security Teams in Both Approaches
Security teams encounter significant challenges with Cyber Threat Intelligence and Threat Hunting, including the complexity of analyzing vast amounts of data to identify relevant threats and the need for continuous updating of threat databases in response to evolving cyberattack techniques. Cyber Threat Intelligence struggles with timely validation of intelligence and integration into existing security frameworks, while Threat Hunting faces difficulties in detecting sophisticated, hidden threats without clear indicators of compromise. Both approaches demand highly skilled professionals and advanced analytical tools to mitigate risks effectively in an increasingly complex threat landscape.
Future Trends in Threat Intelligence and Threat Hunting
Emerging trends in Cyber Threat Intelligence emphasize the integration of artificial intelligence and machine learning to predict and analyze threat actor behavior with greater accuracy. Threat Hunting is evolving towards real-time data analytics and automated detection frameworks to proactively identify sophisticated and previously unknown threats. Combining these advancements enables security teams to shift from reactive responses to adaptive, predictive defense strategies against evolving cyber threats.
Cyber Threat Intelligence vs Threat Hunting Infographic
 difterm.com
difterm.com