Data masking and data obfuscation are critical techniques in enhancing security for sensitive information. Data masking replaces real data with fictitious but realistic values to prevent unauthorized access during testing or analysis, ensuring data privacy. Data obfuscation, on the other hand, transforms data into a scrambled and unintelligible format, protecting it from reverse engineering and unauthorized exposure while maintaining usability in specific environments.
Table of Comparison
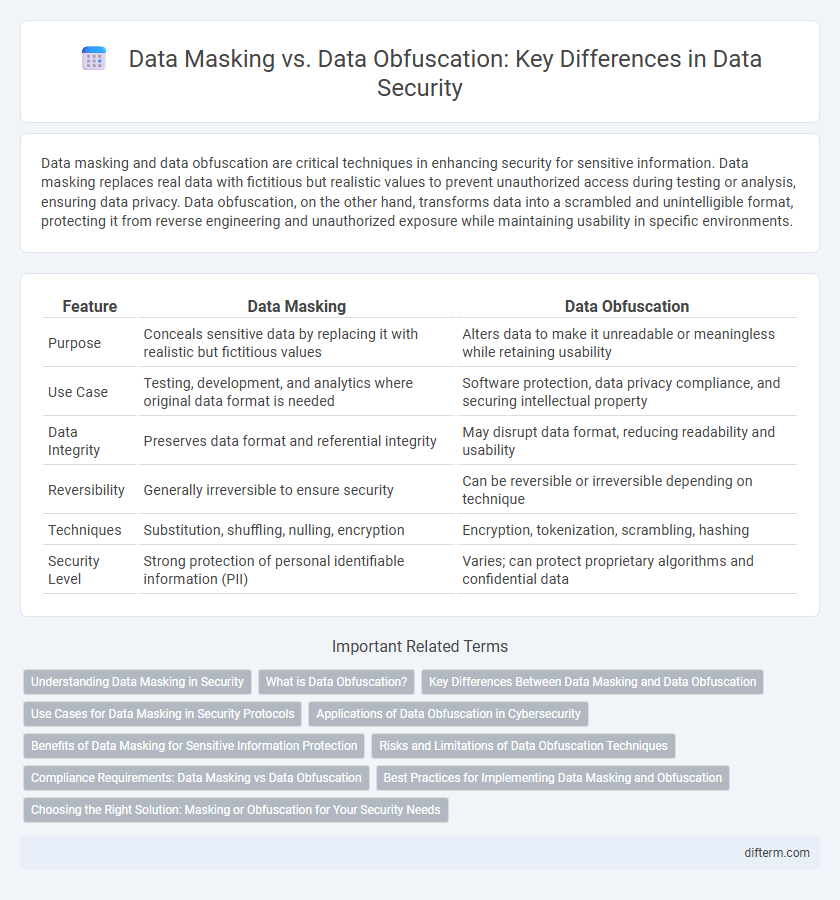
| Feature | Data Masking | Data Obfuscation |
|---|---|---|
| Purpose | Conceals sensitive data by replacing it with realistic but fictitious values | Alters data to make it unreadable or meaningless while retaining usability |
| Use Case | Testing, development, and analytics where original data format is needed | Software protection, data privacy compliance, and securing intellectual property |
| Data Integrity | Preserves data format and referential integrity | May disrupt data format, reducing readability and usability |
| Reversibility | Generally irreversible to ensure security | Can be reversible or irreversible depending on technique |
| Techniques | Substitution, shuffling, nulling, encryption | Encryption, tokenization, scrambling, hashing |
| Security Level | Strong protection of personal identifiable information (PII) | Varies; can protect proprietary algorithms and confidential data |
Understanding Data Masking in Security
Data masking in security involves replacing sensitive information with realistic but fictitious data to protect privacy while maintaining usability in testing or analysis environments. It ensures that original confidential data remains undisclosed by transforming values through techniques such as substitution, shuffling, or encryption. This approach mitigates risks of data breaches by preserving data format and consistency, making it ideal for compliance with regulations like GDPR and HIPAA.
What is Data Obfuscation?
Data obfuscation is a security technique that transforms sensitive data into a scrambled or unreadable format while preserving its original structure and usability for testing or analysis purposes. Unlike data masking, which replaces data with realistic but fictitious values, obfuscation modifies the data through methods such as encryption, tokenization, or character substitution to prevent unauthorized access. This approach ensures that sensitive information remains protected throughout development, testing, or sharing processes without exposing actual data.
Key Differences Between Data Masking and Data Obfuscation
Data masking replaces sensitive data with realistic but fictitious values to protect confidentiality while preserving usability in non-production environments. Data obfuscation alters data to make it unintelligible or ambiguous, often using techniques like encryption or tokenization, primarily to prevent unauthorized access or reverse engineering. The key difference lies in data masking maintaining format and usability for testing, whereas data obfuscation prioritizes security by making the data indecipherable.
Use Cases for Data Masking in Security Protocols
Data masking is essential in security protocols for protecting sensitive information during software testing, development, and user training by replacing original data with realistic but non-identifiable values. It ensures compliance with regulations such as GDPR and HIPAA by preventing the exposure of personal or confidential data in non-production environments. Unlike data obfuscation, which focuses on making data unintelligible, data masking maintains format consistency to enable accurate testing while safeguarding privacy.
Applications of Data Obfuscation in Cybersecurity
Data obfuscation in cybersecurity is commonly applied to protect sensitive application code and algorithms from reverse engineering and tampering. It masks the true logic and structure of software, hindering attackers from exploiting vulnerabilities or extracting confidential information. This technique is crucial for safeguarding intellectual property and preventing unauthorized access in both client-side and server-side environments.
Benefits of Data Masking for Sensitive Information Protection
Data masking enhances sensitive information protection by permanently replacing original data with realistic but non-sensitive substitutes, reducing the risk of unauthorized access during testing or development. It enables organizations to comply with privacy regulations like GDPR and HIPAA by ensuring that personally identifiable information (PII) and confidential data remain concealed. This method minimizes data breach impacts while maintaining data utility for analysis and application functionality.
Risks and Limitations of Data Obfuscation Techniques
Data obfuscation techniques pose risks including incomplete protection as sensitive data can sometimes be reverse-engineered, leaving systems vulnerable to breaches. Limitations also involve performance degradation due to computational overhead and compatibility issues with certain applications or databases. These factors reduce the overall effectiveness of obfuscation, necessitating complementary security measures for robust data protection.
Compliance Requirements: Data Masking vs Data Obfuscation
Data masking and data obfuscation serve distinct roles in meeting compliance requirements such as GDPR, HIPAA, and PCI-DSS by protecting sensitive information from unauthorized access. Data masking replaces original data with realistic but fictional values, ensuring that masked data maintains structural integrity for testing and development environments while complying with strict data privacy laws. Data obfuscation alters data elements to make them unintelligible or unusable, often used to secure data in production environments by preventing reverse engineering or unauthorized data retrieval.
Best Practices for Implementing Data Masking and Obfuscation
Implementing data masking requires identifying sensitive data elements and applying dynamic or static masking techniques to ensure data privacy without compromising usability. Effective data obfuscation involves transforming data into a non-recognizable format while maintaining consistency for testing or development, using methods like tokenization or encryption. Best practices emphasize regular audits, role-based access controls, and continuous monitoring to maintain data security compliance and prevent unauthorized exposure.
Choosing the Right Solution: Masking or Obfuscation for Your Security Needs
Data masking replaces sensitive information with realistic but fictitious data to protect confidentiality in non-production environments, while data obfuscation alters data structure or logic to conceal its true meaning, often used in software development or analytics. Selecting the right security solution depends on the use case: data masking is ideal for compliance with regulations like GDPR or HIPAA during testing or training, whereas data obfuscation is better suited for protecting intellectual property and preventing reverse engineering. Evaluating the sensitivity of data, regulatory requirements, and the intended usage environment ensures optimal protection and operational efficiency.
Data Masking vs Data Obfuscation Infographic
 difterm.com
difterm.com