Account takeover occurs when attackers gain unauthorized access to a user's account by exploiting weak or stolen credentials. Credential stuffing involves using automated tools to test large volumes of stolen username and password combinations across multiple sites to infiltrate accounts. Both attacks threaten security but credential stuffing relies on breached data sets, while account takeover can include various methods such as phishing or social engineering.
Table of Comparison
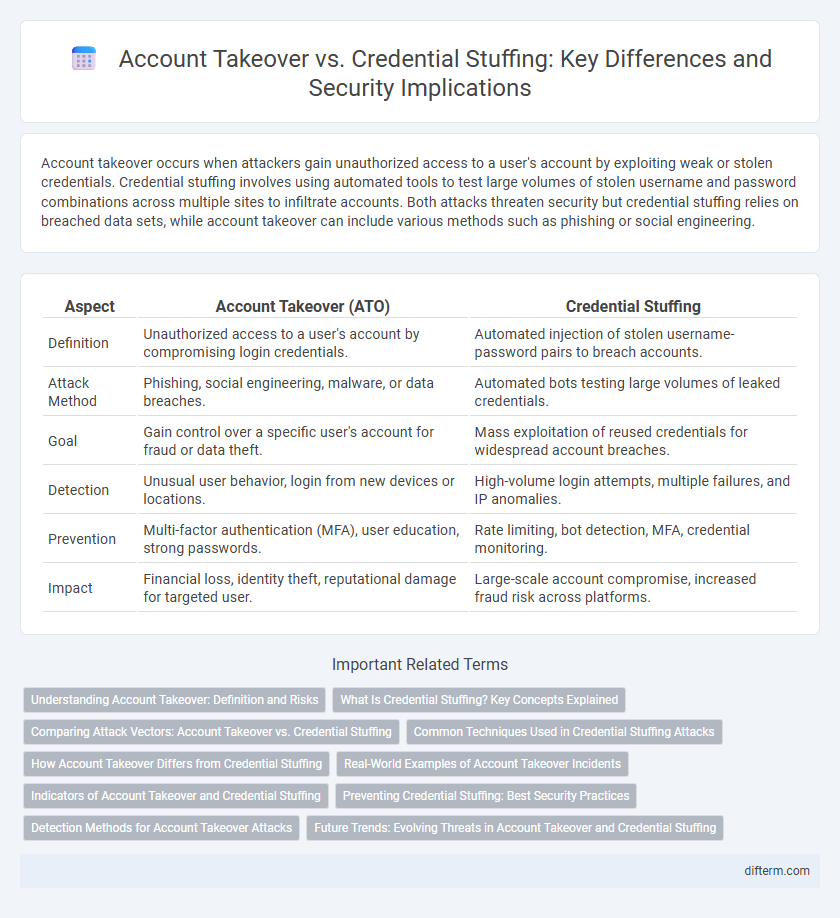
| Aspect | Account Takeover (ATO) | Credential Stuffing |
|---|---|---|
| Definition | Unauthorized access to a user's account by compromising login credentials. | Automated injection of stolen username-password pairs to breach accounts. |
| Attack Method | Phishing, social engineering, malware, or data breaches. | Automated bots testing large volumes of leaked credentials. |
| Goal | Gain control over a specific user's account for fraud or data theft. | Mass exploitation of reused credentials for widespread account breaches. |
| Detection | Unusual user behavior, login from new devices or locations. | High-volume login attempts, multiple failures, and IP anomalies. |
| Prevention | Multi-factor authentication (MFA), user education, strong passwords. | Rate limiting, bot detection, MFA, credential monitoring. |
| Impact | Financial loss, identity theft, reputational damage for targeted user. | Large-scale account compromise, increased fraud risk across platforms. |
Understanding Account Takeover: Definition and Risks
Account takeover occurs when unauthorized individuals gain control of a user's account by exploiting stolen credentials, leading to potential financial loss, data breaches, and identity theft. Unlike credential stuffing, which involves mass automated login attempts using leaked username-password pairs, account takeover is often the result of targeted attacks exploiting weak passwords, phishing, or social engineering. Understanding these risks highlights the importance of strong authentication methods, real-time monitoring, and multi-factor authentication to prevent unauthorized access and ensure data security.
What Is Credential Stuffing? Key Concepts Explained
Credential stuffing is a cyberattack technique where hackers use automated tools to try large volumes of stolen username and password combinations across multiple websites to gain unauthorized access. Unlike account takeover, which involves compromising a single account through various methods, credential stuffing relies on the reuse of credentials from data breaches to exploit weak password practices. Effective defense strategies include multi-factor authentication, monitoring for unusual login activities, and the use of bot detection systems to prevent automated login attempts.
Comparing Attack Vectors: Account Takeover vs. Credential Stuffing
Account takeover (ATO) involves hackers gaining unauthorized access to user accounts through various methods such as phishing, social engineering, or brute force attacks, often targeting high-value accounts with personalized tactics. Credential stuffing specifically exploits large volumes of leaked username-password pairs to automate login attempts, relying on users' password reuse across multiple platforms. While ATO uses diversified attack vectors including manual and automated approaches, credential stuffing is a subset of ATO that primarily depends on compromised credentials from data breaches and automated tools to achieve account compromise.
Common Techniques Used in Credential Stuffing Attacks
Credential stuffing attacks commonly leverage large collections of breached username and password pairs to automate login attempts across multiple websites using botnets and scripts. Attackers employ techniques such as IP rotation, CAPTCHA bypass, and credential stuffing tools to evade detection and increase success rates. These automated methods exploit the tendency of users to reuse passwords, making credential stuffing a significant risk for account takeover incidents.
How Account Takeover Differs from Credential Stuffing
Account takeover (ATO) involves a malicious actor gaining unauthorized access to a user's specific account, often by exploiting stolen credentials combined with additional tactics like phishing or social engineering. Credential stuffing relies on automated tools to rapidly test large volumes of leaked username-password pairs across multiple sites, aiming to identify accounts with reused credentials. The key difference lies in ATO targeting individual accounts with tailored attacks, whereas credential stuffing is a broad, automated attack exploiting credential reuse habits.
Real-World Examples of Account Takeover Incidents
Account takeover incidents often result from cybercriminals exploiting stolen credentials through various methods, including credential stuffing attacks that automate login attempts using breached databases. Real-world examples such as the 2020 Twitter hack demonstrated attackers gaining control by compromising employee credentials, leading to a significant security breach and financial fraud. These incidents highlight the critical need for multi-factor authentication and continuous monitoring to mitigate account compromise risks.
Indicators of Account Takeover and Credential Stuffing
Indicators of account takeover include unusual login locations, sudden changes in account settings, and unexpected password resets. Credential stuffing is characterized by rapid, repeated login attempts from multiple IP addresses using stolen credential pairs. Monitoring IP reputation, login velocity, and abnormal authentication patterns helps detect and differentiate between account takeover and credential stuffing attacks.
Preventing Credential Stuffing: Best Security Practices
Preventing credential stuffing requires implementing multi-factor authentication (MFA) and employing IP reputation monitoring to detect suspicious login attempts. Using rate limiting and CAPTCHA challenges can effectively block automated scripts attempting mass logins. Regularly updating password policies and leveraging threat intelligence feeds enhance defenses against compromised credential use.
Detection Methods for Account Takeover Attacks
Behavioral analytics play a crucial role in detecting account takeover attacks by identifying deviations in user login patterns, such as unusual IP locations or device usage. Machine learning algorithms analyze failed login attempts and rapid successive logins to flag suspicious credential stuffing activities. Multi-factor authentication combined with real-time risk assessment enhances the accuracy of detecting unauthorized access in account takeover scenarios.
Future Trends: Evolving Threats in Account Takeover and Credential Stuffing
Future trends in account takeover and credential stuffing reveal increasing use of advanced machine learning algorithms and AI-driven automation to bypass traditional security measures. Attackers are leveraging biometrics spoofing and multi-factor authentication fatigue to exploit vulnerabilities, intensifying the risk of large-scale breaches. The proliferation of decentralized identity systems and zero-trust architectures offers promising defense mechanisms to mitigate these evolving threats.
Account takeover vs Credential stuffing Infographic
 difterm.com
difterm.com