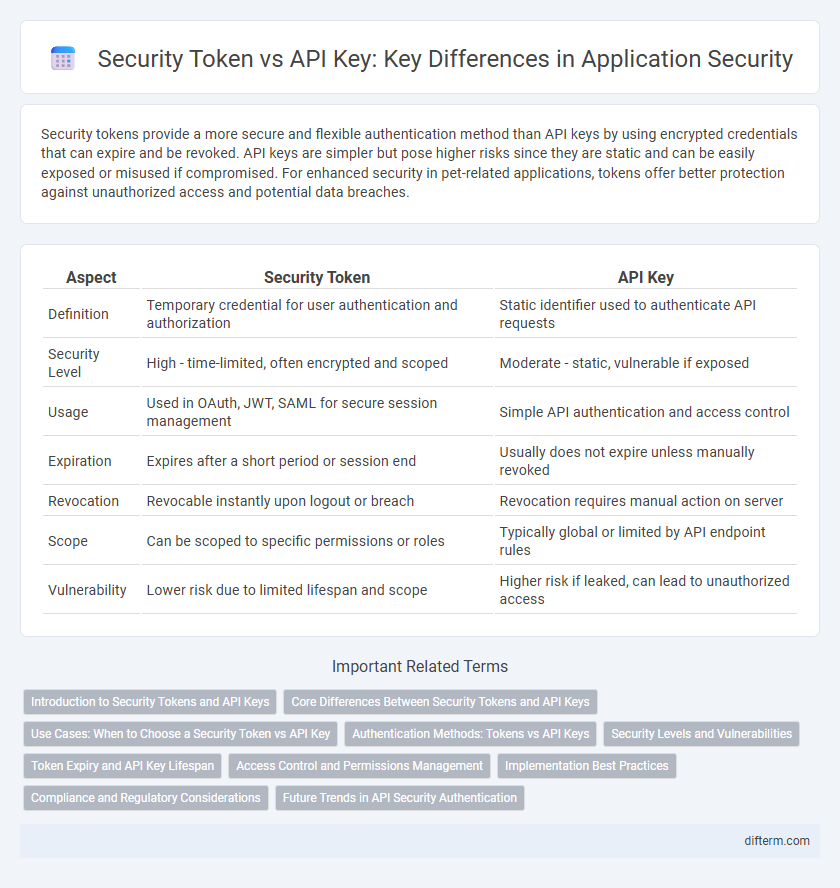
Security tokens provide a more secure and flexible authentication method than API keys by using encrypted credentials that can expire and be revoked. API keys are simpler but pose higher risks since they are static and can be easily exposed or misused if compromised. For enhanced security in pet-related applications, tokens offer better protection against unauthorized access and potential data breaches.
Table of Comparison
| Aspect | Security Token | API Key |
|---|---|---|
| Definition | Temporary credential for user authentication and authorization | Static identifier used to authenticate API requests |
| Security Level | High - time-limited, often encrypted and scoped | Moderate - static, vulnerable if exposed |
| Usage | Used in OAuth, JWT, SAML for secure session management | Simple API authentication and access control |
| Expiration | Expires after a short period or session end | Usually does not expire unless manually revoked |
| Revocation | Revocable instantly upon logout or breach | Revocation requires manual action on server |
| Scope | Can be scoped to specific permissions or roles | Typically global or limited by API endpoint rules |
| Vulnerability | Lower risk due to limited lifespan and scope | Higher risk if leaked, can lead to unauthorized access |
Introduction to Security Tokens and API Keys
Security tokens are cryptographic credentials designed to authenticate users or devices by securely transmitting identity information, providing enhanced protection against unauthorized access. API keys serve as simple unique identifiers for applications to access APIs but offer limited security compared to security tokens, as they can be more easily intercepted or compromised. Employing security tokens over API keys significantly improves authentication robustness in modern security architectures.
Core Differences Between Security Tokens and API Keys
Security tokens provide dynamic, time-limited authentication based on cryptographic protocols, enhancing security by reducing the risk of interception and misuse. API keys offer static, simple access credentials tied to specific applications or users, which can be more vulnerable if exposed due to their longevity and lack of inherent encryption. Unlike API keys, security tokens support granular permissions and expiration, enabling finer control over resource access and improving threat mitigation.
Use Cases: When to Choose a Security Token vs API Key
Security tokens are ideal for applications requiring strong user authentication and granular access control, such as financial services or healthcare systems. API keys suit scenarios involving simple, server-to-server communication or basic project integrations with limited permissions. Selecting between a security token and an API key depends on the need for enhanced security measures versus ease of implementation and scalability.
Authentication Methods: Tokens vs API Keys
Security tokens provide a more robust authentication method by enabling fine-grained access control and short-lived sessions, reducing the risk of credential theft and replay attacks. API keys are simpler to implement but often lack expiration and scope limitations, making them more vulnerable to misuse if exposed. Implementing tokens supports dynamic authentication workflows such as OAuth and JWT, enhancing security in modern APIs compared to static API keys.
Security Levels and Vulnerabilities
Security tokens offer higher security levels than API keys by using encrypted, time-limited credentials that reduce the risk of interception and unauthorized access. API keys are static and vulnerable to leakage through client-side exposure or inadequate storage, making them easier targets for attackers. Implementing security tokens helps in enforcing fine-grained access control and expiration policies, enhancing overall system security.
Token Expiry and API Key Lifespan
Security tokens typically feature a limited lifespan with automatic expiration to reduce the risk of unauthorized access, often ranging from minutes to hours depending on the system's configuration. In contrast, API keys generally have longer or indefinite lifespans unless manually revoked, posing a higher security risk if compromised. Implementing token expiry enforces frequent re-authentication and enhances security by minimizing the window of vulnerability compared to static API keys.
Access Control and Permissions Management
Security tokens provide granular access control and dynamic permissions management by embedding user roles and scopes within encrypted tokens, allowing systems to verify identity and restrict resource access efficiently. API keys, while simpler to implement, lack inherent permission granularity and are typically static, posing higher risks if exposed due to their broad access capabilities. Implementing security tokens enhances security posture by enabling fine-tuned permissions adjustments and reducing unauthorized access compared to traditional API key-based authentication.
Implementation Best Practices
Security tokens should be implemented using strong cryptographic standards such as JWT with proper expiration times and signature validation to ensure secure authentication and authorization. API keys must be stored securely, rotated regularly, and scoped with minimal permissions to limit access and reduce risk. Implement granular access controls and monitor usage patterns to detect anomalies and prevent unauthorized access effectively.
Compliance and Regulatory Considerations
Security tokens offer enhanced compliance capabilities by supporting multifactor authentication and fine-grained access controls, aligning with regulations such as GDPR and HIPAA. API keys, while simpler to implement, often lack robust auditing and revocation features, making them less suitable for environments with stringent regulatory requirements. Organizations must evaluate these differences to ensure adherence to industry standards and protect sensitive data effectively.
Future Trends in API Security Authentication
Security tokens are evolving to offer dynamic, context-aware authentication with granular access controls, significantly enhancing API security compared to static API keys. Future trends emphasize the adoption of decentralized identity frameworks and biometric integration to reduce reliance on traditional API keys and minimize risks of credential theft. Advances in machine learning-driven anomaly detection and zero-trust architectures further bolster protection by continuously validating security tokens during API interactions.
Security Token vs API Key Infographic
 difterm.com
difterm.com