Smishing involves fraudulent text messages that trick users into revealing personal information or clicking on malicious links, while vishing uses phone calls to impersonate legitimate organizations and extract sensitive data. Both attacks exploit social engineering techniques to manipulate victims, but smishing targets mobile messaging platforms whereas vishing relies on voice communication. Awareness of these distinct methods enhances security measures and reduces the risk of falling prey to such scams.
Table of Comparison
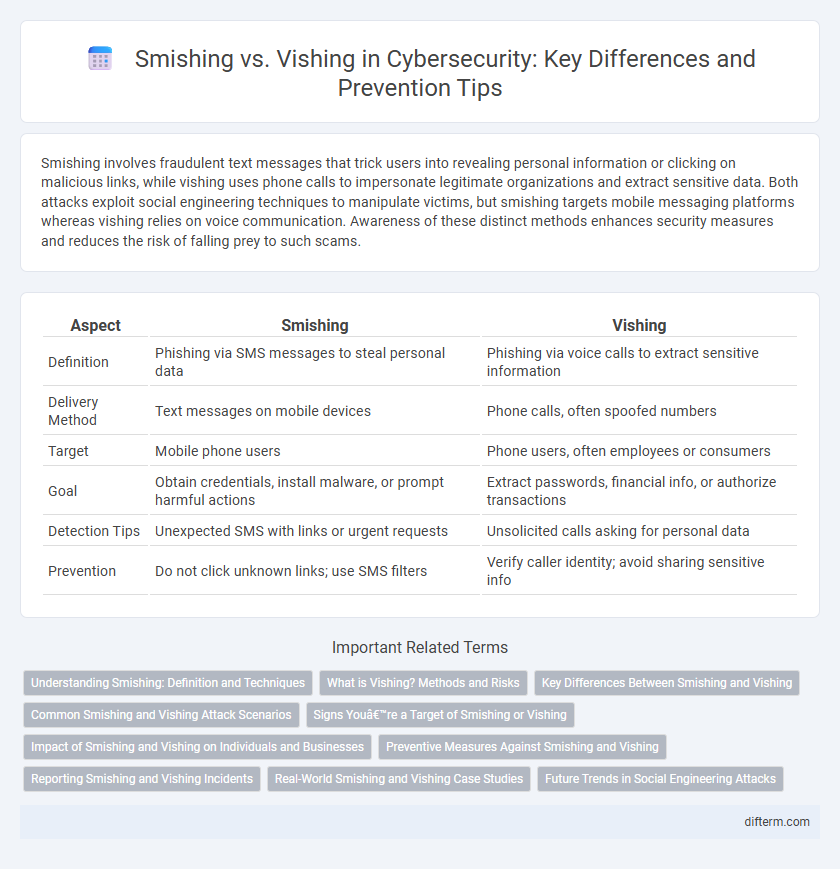
| Aspect | Smishing | Vishing |
|---|---|---|
| Definition | Phishing via SMS messages to steal personal data | Phishing via voice calls to extract sensitive information |
| Delivery Method | Text messages on mobile devices | Phone calls, often spoofed numbers |
| Target | Mobile phone users | Phone users, often employees or consumers |
| Goal | Obtain credentials, install malware, or prompt harmful actions | Extract passwords, financial info, or authorize transactions |
| Detection Tips | Unexpected SMS with links or urgent requests | Unsolicited calls asking for personal data |
| Prevention | Do not click unknown links; use SMS filters | Verify caller identity; avoid sharing sensitive info |
Understanding Smishing: Definition and Techniques
Smishing is a cyberattack leveraging SMS text messages to deceive recipients into revealing personal information or clicking malicious links, exploiting the trust users place in their mobile devices. Common techniques include fake alerts, urgent requests, and disguised URLs that mimic legitimate sources, aiming to steal credentials or install malware. Understanding smishing patterns enhances mobile security by enabling users to recognize and avoid fraudulent messages effectively.
What is Vishing? Methods and Risks
Vishing, or voice phishing, involves cybercriminals using phone calls or voice messages to deceive individuals into revealing sensitive information such as passwords, credit card numbers, or social security details. Common methods include impersonating trusted entities like banks or government agencies, employing social engineering tactics, and using spoofed caller IDs to gain credibility. The risks of vishing encompass financial loss, identity theft, unauthorized account access, and compromised personal security.
Key Differences Between Smishing and Vishing
Smishing involves fraudulent text messages that attempt to trick individuals into revealing personal information or clicking malicious links, while vishing employs phone calls to deceive victims into sharing sensitive data. Smishing typically exploits SMS platforms and often uses automated systems or spoofed numbers, whereas vishing relies on real-time voice interactions, making it more personalized and persuasive. Security professionals must differentiate these attack vectors to implement tailored anti-phishing strategies and enhance user awareness in combating cyber fraud.
Common Smishing and Vishing Attack Scenarios
Smishing attacks often involve fraudulent text messages that trick recipients into clicking malicious links or revealing sensitive information, such as fake delivery alerts or urgent account verification requests. Vishing scams typically use phone calls, where attackers impersonate trustworthy entities like banks or government agencies to extract confidential data or induce financial transactions. Both tactics exploit social engineering techniques to create a sense of urgency and manipulate victims into compromising their security.
Signs You’re a Target of Smishing or Vishing
Unsolicited messages or calls requesting sensitive information such as passwords or credit card details often indicate smishing or vishing attempts. Urgent language pressuring immediate action, unsolicited links, or requests for personal data are clear signs of these phishing tactics. Observing inconsistencies in caller ID or spotting misspelled URLs in messages helps identify fraudulent smishing and vishing schemes targeting your security.
Impact of Smishing and Vishing on Individuals and Businesses
Smishing and vishing pose significant security threats by exploiting social engineering to steal personal data and financial information from individuals and businesses. Smishing uses SMS messages to deliver malicious links or requests, leading to account breaches and financial losses, while vishing employs phone calls to impersonate trusted entities, causing unauthorized access and identity theft. The financial impact includes costly remediation efforts, reputational damage, and regulatory fines for businesses, alongside personal privacy violations and monetary loss for individuals.
Preventive Measures Against Smishing and Vishing
Preventive measures against smishing and vishing include verifying the identity of callers or message senders through official channels before sharing any personal information. Employing multi-factor authentication (MFA) and regularly updating security software enhances protection against these social engineering attacks. Users should be educated on recognizing suspicious links, urgent requests, and unsolicited communications to reduce the risk of falling victim to smishing and vishing scams.
Reporting Smishing and Vishing Incidents
Reporting smishing incidents involves promptly forwarding suspicious SMS messages to your mobile carrier or dedicated cybersecurity teams to analyze and block fraudulent sources. Vishing incident reporting requires documenting details such as caller ID, call time, and content before alerting your organization's security department or calling relevant fraud prevention hotlines. Timely reporting of both smishing and vishing attempts enhances threat intelligence, enabling authorities to detect patterns and prevent widespread cyber fraud.
Real-World Smishing and Vishing Case Studies
Real-world smishing attacks often exploit SMS messages to deliver malicious links or prompt users to provide sensitive information, exemplified by cases where fraudsters impersonate banks to steal credentials. Vishing scams leverage voice calls with spoofed numbers to manipulate victims into revealing personal data or transferring funds, as seen in incidents involving fake IRS or tech support calls. Both attack types highlight the evolving tactics in social engineering, emphasizing the need for robust user education and multi-factor authentication to mitigate risks.
Future Trends in Social Engineering Attacks
Smishing and vishing attacks are increasingly leveraging artificial intelligence to craft more personalized and convincing scams, enhancing the effectiveness of social engineering tactics. Voice deepfake technology is expected to revolutionize vishing by enabling attackers to mimic trusted voices with alarming accuracy, posing significant challenges to traditional verification methods. Emerging trends indicate a shift towards multi-channel attacks that combine SMS, voice, and social media platforms to exploit human vulnerabilities across different communication vectors.
Smishing vs Vishing Infographic
 difterm.com
difterm.com