Secure Boot verifies the authenticity of the firmware and operating system during the initial startup process to prevent unauthorized code execution. Trusted Boot extends this verification by measuring and recording the integrity of each component throughout the boot sequence, enabling detection of any tampering or anomalies. Both methods enhance device security by ensuring only trusted software is loaded, with Trusted Boot providing a more comprehensive integrity verification.
Table of Comparison
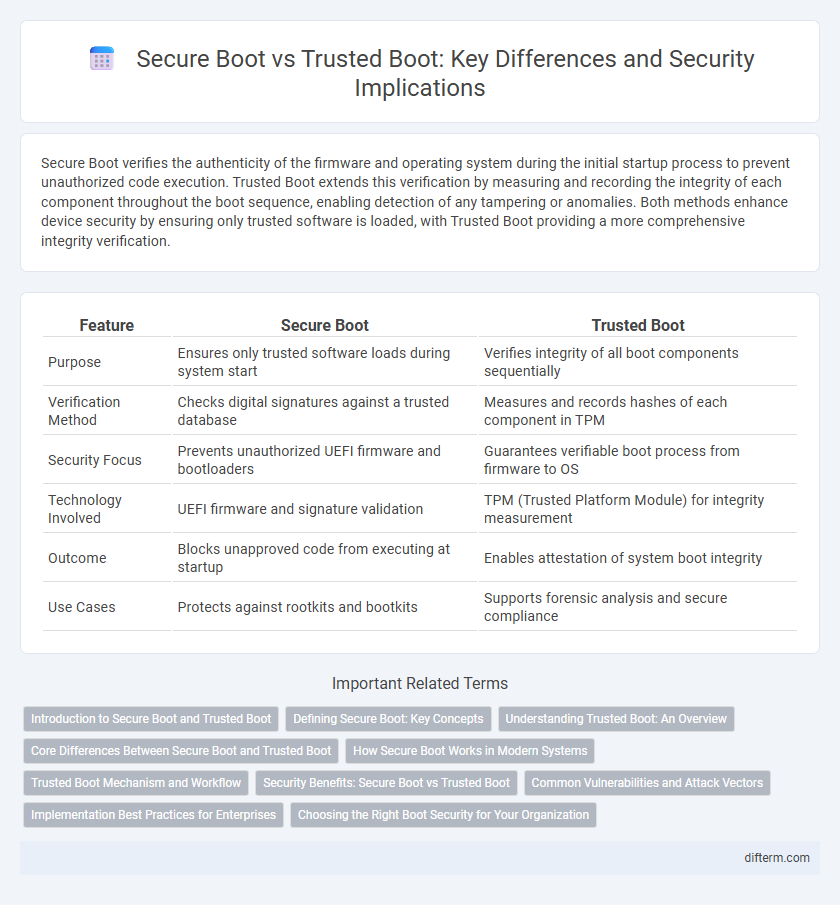
| Feature | Secure Boot | Trusted Boot |
|---|---|---|
| Purpose | Ensures only trusted software loads during system start | Verifies integrity of all boot components sequentially |
| Verification Method | Checks digital signatures against a trusted database | Measures and records hashes of each component in TPM |
| Security Focus | Prevents unauthorized UEFI firmware and bootloaders | Guarantees verifiable boot process from firmware to OS |
| Technology Involved | UEFI firmware and signature validation | TPM (Trusted Platform Module) for integrity measurement |
| Outcome | Blocks unapproved code from executing at startup | Enables attestation of system boot integrity |
| Use Cases | Protects against rootkits and bootkits | Supports forensic analysis and secure compliance |
Introduction to Secure Boot and Trusted Boot
Secure Boot is a security standard that ensures a device boots using only software authorized by the Original Equipment Manufacturer (OEM), preventing unauthorized firmware or OS loaders from executing during startup. Trusted Boot extends this concept by verifying each phase of the boot process, using measurements stored in a trusted platform module (TPM) to detect any tampering or unauthorized changes to the boot sequence. Both technologies reinforce system integrity but focus on different stages and methods of securing the boot chain.
Defining Secure Boot: Key Concepts
Secure Boot is a security standard implemented in modern firmware to ensure that only trusted software with verified digital signatures can execute during the system startup process. It prevents unauthorized or malicious code, such as rootkits or bootkits, from loading by validating the authenticity and integrity of the bootloader and operating system components. This mechanism is integral to protecting the system's firmware from tampering and maintaining a trusted computing environment.
Understanding Trusted Boot: An Overview
Trusted Boot verifies the integrity of the system by measuring and logging each component during the boot process, starting from the firmware. It builds a chain of trust that ensures only trusted software loads, enhancing protection against rootkits and bootkits. Trusted Boot complements Secure Boot by providing detailed attestation and continuous verification beyond signature checks.
Core Differences Between Secure Boot and Trusted Boot
Secure Boot verifies the digital signatures of firmware and bootloaders to ensure only trusted software executes during the system start-up, protecting against unauthorized code injection. Trusted Boot extends this by measuring each component's integrity at every boot stage, recording these measurements in a TPM (Trusted Platform Module) to provide a verifiable audit trail for system trustworthiness. While Secure Boot focuses on authenticity, Trusted Boot emphasizes continuous validation and attestation of the boot process to detect and prevent tampering effectively.
How Secure Boot Works in Modern Systems
Secure Boot leverages a hardware root of trust embedded in the firmware to verify each component of the boot process, ensuring that only signed and trusted software loads. The system's UEFI firmware checks the digital signature of bootloaders, drivers, and operating systems against a stored database of trusted certificates before execution. This cryptographic verification prevents unauthorized or malicious code from compromising the system during startup, enhancing overall device integrity.
Trusted Boot Mechanism and Workflow
Trusted Boot leverages a hardware root of trust to verify each stage of the boot process, ensuring the integrity of the firmware, bootloader, and operating system before execution. It measures and stores hashes of each component in a secure TPM (Trusted Platform Module), enabling attestation and detection of unauthorized modifications. This mechanism creates a chain of trust from the hardware to the OS, preventing bootkits and persistent malware from compromising system security.
Security Benefits: Secure Boot vs Trusted Boot
Secure Boot ensures that only digitally signed and authorized firmware, bootloaders, and operating systems run during startup, preventing unauthorized code execution and rootkits. Trusted Boot extends this by measuring and recording the integrity of each component loaded, creating a chain of trust that enables detection of tampering and unauthorized modifications. This combination enhances system security by both blocking malicious code at boot time and providing forensic evidence for ongoing integrity verification.
Common Vulnerabilities and Attack Vectors
Secure Boot protects the device by verifying the digital signature of the firmware and preventing unauthorized code from executing during the boot process, but it is vulnerable to attacks like bootloader tampering and key extraction. Trusted Boot extends this by measuring and recording each component loaded to establish a chain of trust, yet it faces threats such as replay attacks and measurement manipulation. Both methods require robust key management and secure hardware roots of trust to mitigate vulnerabilities and resist sophisticated attack vectors targeting firmware integrity.
Implementation Best Practices for Enterprises
Implementing Secure Boot requires configuring firmware to verify the digital signature of the bootloader, ensuring only trusted software loads during system startup, which prevents unauthorized code execution. Trusted Boot extends this by measuring and recording each component in the boot sequence using a Trusted Platform Module (TPM), enabling enterprises to verify system integrity remotely and detect tampering. Best practices for enterprises include regularly updating firmware signatures, integrating TPM-based attestation with security monitoring tools, and enforcing strict access controls to prevent boot configuration modification.
Choosing the Right Boot Security for Your Organization
Secure Boot verifies the digital signature of firmware and operating system loaders to prevent unauthorized code from running during system startup, ensuring a trusted software stack from the initial stages. Trusted Boot extends this process by measuring each component during the boot sequence, creating a chain of trust and enabling integrity assessment through a trusted platform module (TPM). Organizations should evaluate the criticality of system integrity and regulatory requirements to determine whether Secure Boot's code authentication or Trusted Boot's continuous integrity verification best aligns with their security posture.
Secure Boot vs Trusted Boot Infographic
 difterm.com
difterm.com