Application whitelisting enhances security by allowing only pre-approved software to run, effectively preventing unauthorized or malicious applications from executing. Blacklisting, on the other hand, blocks known harmful programs but may fail to catch new or unknown threats, leaving systems vulnerable. Implementing application whitelisting provides a proactive defense mechanism that reduces the attack surface and strengthens overall cybersecurity posture.
Table of Comparison
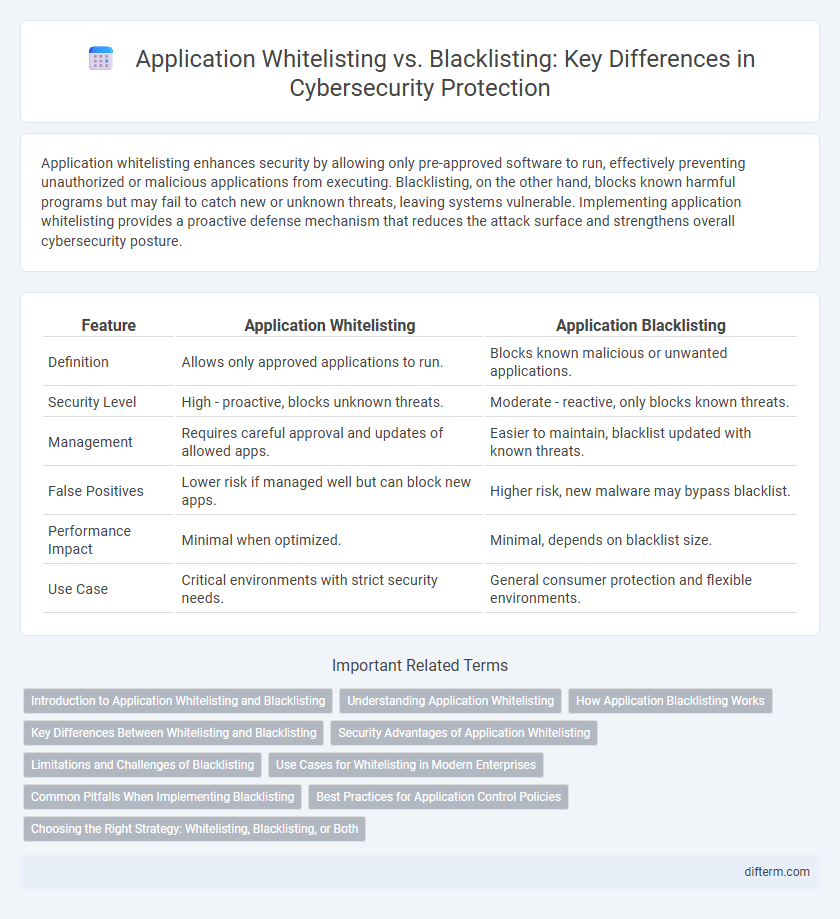
| Feature | Application Whitelisting | Application Blacklisting |
|---|---|---|
| Definition | Allows only approved applications to run. | Blocks known malicious or unwanted applications. |
| Security Level | High - proactive, blocks unknown threats. | Moderate - reactive, only blocks known threats. |
| Management | Requires careful approval and updates of allowed apps. | Easier to maintain, blacklist updated with known threats. |
| False Positives | Lower risk if managed well but can block new apps. | Higher risk, new malware may bypass blacklist. |
| Performance Impact | Minimal when optimized. | Minimal, depends on blacklist size. |
| Use Case | Critical environments with strict security needs. | General consumer protection and flexible environments. |
Introduction to Application Whitelisting and Blacklisting
Application whitelisting enhances security by allowing only pre-approved software to run, effectively blocking unauthorized or malicious programs. In contrast, application blacklisting focuses on identifying and blocking known harmful software but can be less effective against unknown threats. Implementing whitelisting strengthens protection by minimizing the attack surface and reducing the risk of malware infections.
Understanding Application Whitelisting
Application whitelisting enhances security by allowing only pre-approved software to execute, significantly reducing the risk of malware infections and unauthorized programs. Unlike blacklisting, which blocks known threats but can miss new or unknown malicious software, whitelisting provides proactive protection by defaulting to deny unrecognized applications. Implementing application whitelisting helps organizations maintain tighter control over endpoints, ensuring that only trusted applications run within the network environment.
How Application Blacklisting Works
Application blacklisting works by identifying and blocking known malicious or unauthorized software based on a precompiled list of disallowed applications, preventing them from executing on the system. This approach relies on continuously updated threat intelligence databases and signatures to detect harmful programs while allowing all other software to run by default. Blacklisting can effectively reduce the risk of known threats but may struggle against zero-day attacks or new malware variants absent from the list.
Key Differences Between Whitelisting and Blacklisting
Application whitelisting allows only pre-approved software to run, blocking all others by default, while blacklisting blocks known malicious and unwanted applications but permits all others to execute. Whitelisting offers a more proactive security approach with tighter control, reducing the attack surface significantly compared to blacklisting, which relies on constantly updated threat intelligence. The dynamic nature of blacklisting can leave gaps where new or unknown threats bypass filters, whereas whitelisting minimizes this risk by enforcing strict execution policies.
Security Advantages of Application Whitelisting
Application whitelisting enhances security by allowing only pre-approved software to execute, minimizing the risk of malware and unauthorized applications infiltrating the system. This proactive approach reduces attack surfaces by blocking unknown and potentially harmful programs before they run, unlike blacklisting which relies on known threats and can miss zero-day exploits. Enforcing strict application control through whitelisting ensures consistent compliance with security policies and simplifies threat management in enterprise environments.
Limitations and Challenges of Blacklisting
Blacklisting in application security faces significant limitations due to its reactive nature, as it relies on identifying and blocking known malicious software after exposure, often leaving systems vulnerable to zero-day exploits and unknown threats. This method struggles with maintaining comprehensive and up-to-date lists, leading to potential false negatives and allowing harmful applications to run undetected. Additionally, managing extensive blacklists can introduce performance overhead and administrative complexity, impacting overall security efficiency.
Use Cases for Whitelisting in Modern Enterprises
Application whitelisting provides a proactive security measure by allowing only pre-approved software to run, significantly reducing the risk of malware infections and zero-day attacks in modern enterprises. It is especially effective in environments with stringent regulatory requirements, such as finance and healthcare, where ensuring application integrity and compliance is critical. Enterprises leverage whitelisting to enforce endpoint protection, minimize attack surfaces, and maintain consistent application control across diverse IT infrastructures.
Common Pitfalls When Implementing Blacklisting
Implementing blacklisting often leads to incomplete protection due to the inability to anticipate all malicious applications, allowing new or unknown threats to bypass security measures. This method also increases administrative overhead by requiring constant updates and monitoring to maintain up-to-date block lists. Furthermore, blacklisting can cause false negatives, where harmful software is not detected, and false positives, which may disrupt legitimate applications and affect user productivity.
Best Practices for Application Control Policies
Implement strict application whitelisting by allowing only pre-approved, verified software to run, significantly reducing the attack surface from unknown or malicious applications. Blacklisting should be used sparingly and in conjunction with whitelisting to block known threats but is less reliable due to the constant emergence of new malware variants. Enforce continuous policy updates, rigorous testing, and user education to maintain effective application control and minimize security risks.
Choosing the Right Strategy: Whitelisting, Blacklisting, or Both
Application whitelisting restricts software execution to pre-approved programs, offering stronger protection against unknown threats but requiring extensive maintenance and user management. Blacklisting blocks known malicious or unwanted applications, allowing more flexibility yet risking exposure to zero-day attacks and unclassified software. Organizations often adopt a hybrid approach, leveraging whitelisting for high-security environments and blacklisting for general use, optimizing both protection and operational efficiency.
Application Whitelisting vs Blacklisting Infographic
 difterm.com
difterm.com