A security posture represents an organization's overall security status, encompassing policies, controls, and measures in place to protect assets against threats. In contrast, a security baseline establishes the minimum security standards and settings required to ensure consistent protection across systems and networks. Understanding the distinction between security posture and security baseline is crucial for maintaining effective risk management and compliance.
Table of Comparison
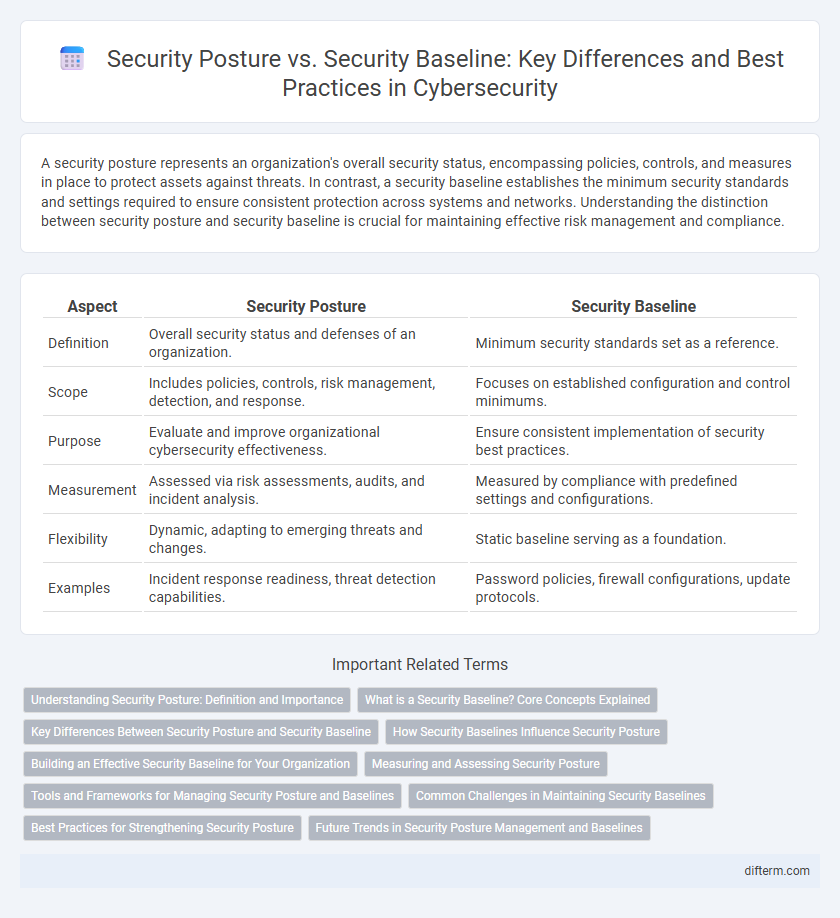
| Aspect | Security Posture | Security Baseline |
|---|---|---|
| Definition | Overall security status and defenses of an organization. | Minimum security standards set as a reference. |
| Scope | Includes policies, controls, risk management, detection, and response. | Focuses on established configuration and control minimums. |
| Purpose | Evaluate and improve organizational cybersecurity effectiveness. | Ensure consistent implementation of security best practices. |
| Measurement | Assessed via risk assessments, audits, and incident analysis. | Measured by compliance with predefined settings and configurations. |
| Flexibility | Dynamic, adapting to emerging threats and changes. | Static baseline serving as a foundation. |
| Examples | Incident response readiness, threat detection capabilities. | Password policies, firewall configurations, update protocols. |
Understanding Security Posture: Definition and Importance
Security posture refers to the overall cybersecurity strength and readiness of an organization, encompassing policies, controls, and response capabilities. It provides a comprehensive view of how effectively an organization can defend against and respond to cyber threats. Understanding security posture is critical for identifying vulnerabilities, prioritizing risk management efforts, and improving incident response strategies.
What is a Security Baseline? Core Concepts Explained
A Security Baseline is a set of minimum security controls and configurations established to ensure consistent protection across systems and networks, serving as a foundation for measuring security effectiveness. It defines standard policies and practices to prevent vulnerabilities and enforce compliance with regulatory requirements. Organizations use security baselines to benchmark their environment, detect deviations, and implement necessary improvements for maintaining a robust security posture.
Key Differences Between Security Posture and Security Baseline
Security posture defines an organization's overall cybersecurity strength, encompassing policies, controls, and response strategies, while a security baseline establishes specific minimum security standards and configurations for systems and devices. The key difference lies in scope; security posture reflects the dynamic state of security readiness and risk exposure, whereas security basement provides fixed, foundational requirements to ensure consistent protection. Organizations continuously assess security posture to adapt to threats, using security baselines as benchmarks for compliance and system hardening.
How Security Baselines Influence Security Posture
Security baselines establish minimum acceptable configurations and controls that create a consistent foundation across systems, directly influencing an organization's overall security posture by reducing vulnerabilities and ensuring compliance with policies. By adhering to these baselines, organizations can measure deviations and assess risks more accurately, thus enhancing threat detection and response capabilities. Regular updates to security baselines reflect evolving threats and regulatory requirements, strengthening the security posture through continuous improvement and risk mitigation.
Building an Effective Security Baseline for Your Organization
Building an effective security baseline involves establishing a minimum set of security controls and configurations that align with industry standards and organizational risk tolerance to ensure consistent defense mechanisms across systems. This baseline serves as a foundation for measuring and improving an organization's overall security posture, enabling proactive identification and remediation of vulnerabilities. Regular audits and updates to the security baseline help maintain compliance and adapt to evolving threat landscapes, strengthening the organization's resilience against cyberattacks.
Measuring and Assessing Security Posture
Measuring security posture involves evaluating an organization's overall cybersecurity effectiveness through continuous monitoring and comprehensive risk assessments, incorporating metrics such as incident response times and vulnerability management. Security baselines provide a set of standardized configurations and controls that serve as a benchmark for maintaining consistent security settings across systems and devices. Comparing current security posture against established security baselines enables organizations to identify deviations, assess potential risks, and prioritize remediation efforts to strengthen defenses.
Tools and Frameworks for Managing Security Posture and Baselines
Security posture management leverages advanced tools such as SIEM (Security Information and Event Management) systems, vulnerability scanners, and endpoint detection platforms to continuously assess and enhance an organization's defense mechanisms. Security baselines are enforced and monitored through frameworks like CIS Controls, NIST Cybersecurity Framework, and ISO/IEC 27001, which provide standardized configurations and compliance criteria to maintain minimal acceptable security standards. Integration of automated compliance tools and configuration management databases (CMDB) ensures consistent alignment between dynamically evolving security postures and established baselines.
Common Challenges in Maintaining Security Baselines
Maintaining security baselines often faces challenges such as inconsistent implementation across diverse systems and difficulty in keeping baselines updated with evolving threats. Organizations struggle with balancing strict baseline enforcement while allowing necessary operational flexibility, leading to potential gaps in security posture. Inadequate monitoring and limited visibility into baseline compliance further increase the risk of undetected vulnerabilities and policy drift.
Best Practices for Strengthening Security Posture
Implementing a robust security posture involves continuous monitoring, threat intelligence integration, and proactive risk management, which surpasses the foundational requirements of a security baseline. Security baselines establish minimum acceptable controls such as firewalls, encryption standards, and access policies, but best practices for strengthening security posture include dynamic vulnerability assessments, adaptive incident response, and employee cybersecurity training. Prioritizing these advanced measures enhances the organization's ability to detect, prevent, and mitigate sophisticated cyber threats effectively.
Future Trends in Security Posture Management and Baselines
Future trends in security posture management emphasize automation and continuous monitoring to adapt to evolving cyber threats, leveraging AI-driven analytics for real-time risk assessment. Security baselines are increasingly defined through dynamic, adaptive frameworks that integrate cloud-native capabilities and compliance standards, enabling organizations to maintain robust defenses amid rapidly changing environments. The convergence of security posture management with baseline enforcement tools fosters proactive threat mitigation and streamlined incident response across hybrid infrastructures.
Security Posture vs Security Baseline Infographic
 difterm.com
difterm.com