Red Team and Blue Team exercises are essential components of security pet strategies, simulating real-world cyber attacks and defenses to enhance organizational resilience. The Red Team adopts an adversarial role, employing offensive tactics to identify vulnerabilities and exploit weaknesses within the security infrastructure. In contrast, the Blue Team focuses on defense, continuously monitoring, detecting, and responding to threats to protect systems and maintain robust security posture.
Table of Comparison
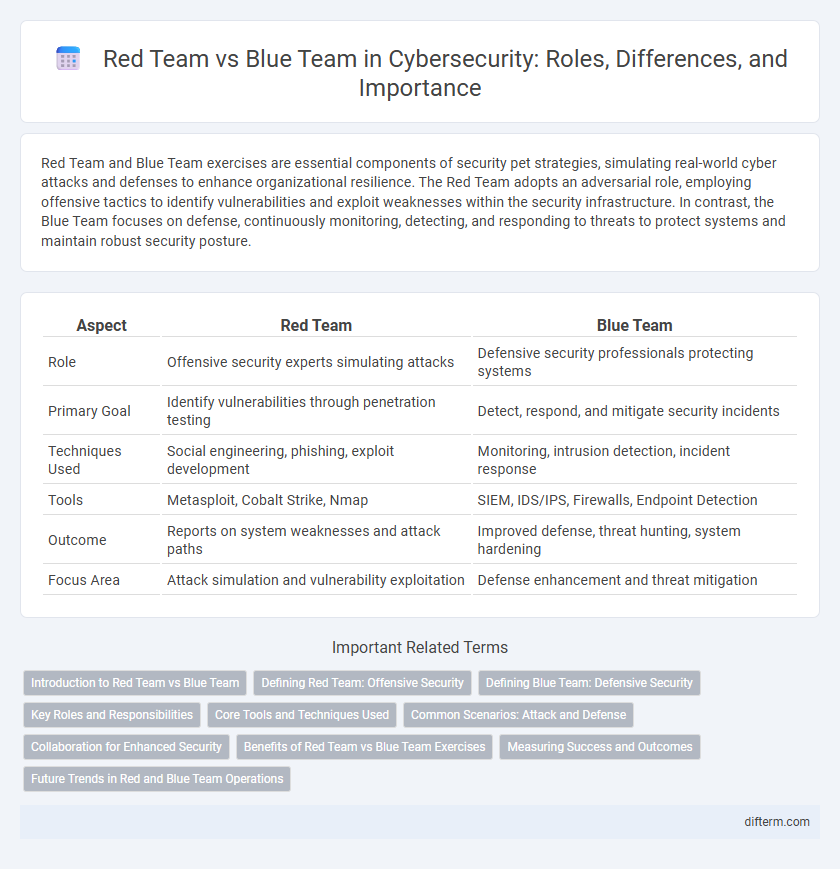
| Aspect | Red Team | Blue Team |
|---|---|---|
| Role | Offensive security experts simulating attacks | Defensive security professionals protecting systems |
| Primary Goal | Identify vulnerabilities through penetration testing | Detect, respond, and mitigate security incidents |
| Techniques Used | Social engineering, phishing, exploit development | Monitoring, intrusion detection, incident response |
| Tools | Metasploit, Cobalt Strike, Nmap | SIEM, IDS/IPS, Firewalls, Endpoint Detection |
| Outcome | Reports on system weaknesses and attack paths | Improved defense, threat hunting, system hardening |
| Focus Area | Attack simulation and vulnerability exploitation | Defense enhancement and threat mitigation |
Introduction to Red Team vs Blue Team
Red Team and Blue Team are critical components in cybersecurity defense strategies, serving distinct but complementary roles. The Red Team acts as ethical hackers simulating real-world attacks to identify vulnerabilities, while the Blue Team focuses on defending systems by detecting, responding to, and mitigating threats. This adversarial approach enhances organizational security posture by continuously testing and improving defensive capabilities against cyber threats.
Defining Red Team: Offensive Security
Red Team refers to a group of cybersecurity professionals specializing in offensive security tactics, simulating real-world cyberattacks to identify vulnerabilities in systems and networks. Their primary objective is to mimic adversaries' techniques, tools, and procedures to test an organization's defenses effectively. By uncovering security weaknesses, Red Teams provide critical insights that enable proactive risk mitigation and enhancement of overall cyber resilience.
Defining Blue Team: Defensive Security
The Blue Team specializes in defensive security measures by continuously monitoring, detecting, and responding to cyber threats within an organization's network infrastructure. Utilizing advanced tools such as intrusion detection systems (IDS), security information and event management (SIEM) solutions, and endpoint protection platforms, the Blue Team ensures real-time threat mitigation and incident response. Their strategic focus on vulnerability management, threat intelligence analysis, and system hardening strengthens the organization's resilience against cyber attacks.
Key Roles and Responsibilities
Red Team specializes in simulating cyberattacks to identify and exploit security vulnerabilities, focusing on penetration testing, social engineering, and threat simulation. Blue Team is responsible for monitoring, detecting, and responding to security incidents, maintaining defensive mechanisms such as intrusion detection systems, firewalls, and incident response protocols. The collaboration between Red Team's offensive tactics and Blue Team's defensive strategies strengthens an organization's overall cybersecurity posture.
Core Tools and Techniques Used
Red Teams utilize tools like Metasploit, Cobalt Strike, and custom exploits to simulate cyberattacks, focusing on penetration testing, social engineering, and vulnerability exploitation. Blue Teams deploy security information and event management (SIEM) systems, intrusion detection systems (IDS), endpoint detection and response (EDR) tools, and conduct log analysis to monitor, detect, and respond to threats. Both teams depend on threat intelligence platforms and sandbox environments to refine their tactics and improve organizational defense mechanisms.
Common Scenarios: Attack and Defense
Red Team exercises simulate real-world cyberattack scenarios such as phishing, social engineering, and network infiltration to identify vulnerabilities within an organization's security posture. Blue Team responds by detecting, analyzing, and mitigating these threats using tools like intrusion detection systems, security information and event management (SIEM), and incident response protocols. Common scenarios include ransomware attacks, insider threats, and advanced persistent threats (APTs) where continuous collaboration improves overall cybersecurity resilience.
Collaboration for Enhanced Security
Red Team and Blue Team collaboration drives enhanced security by simulating realistic cyberattack scenarios and improving defense mechanisms. Red Team's offensive insights combined with Blue Team's defensive strategies identify vulnerabilities, allowing organizations to strengthen their security posture. Continuous communication and knowledge sharing between teams foster proactive threat detection and rapid incident response, reducing overall risk.
Benefits of Red Team vs Blue Team Exercises
Red Team vs Blue Team exercises enhance cybersecurity by simulating real-world attacks to identify vulnerabilities and improve defensive strategies. Red Team tactics expose weaknesses that Blue Team defenders then analyze and fortify, fostering continuous learning and resilience. This dynamic interaction strengthens organizational security posture through proactive threat identification and rapid incident response.
Measuring Success and Outcomes
Red Team exercises measure success by identifying vulnerabilities through simulated attacks, emphasizing breach detection and exploitation efficiency. Blue Team effectiveness is gauged by response time, incident containment, and minimizing damage during security events. Metrics such as mean time to detect (MTTD), mean time to respond (MTTR), and vulnerability remediation rates provide quantitative insights into overall security posture.
Future Trends in Red and Blue Team Operations
Emerging trends in Red and Blue Team operations emphasize the integration of artificial intelligence and machine learning to enhance attack simulation and defense mechanisms. Automation of threat detection and response enables Blue Teams to swiftly neutralize sophisticated cyber threats, while Red Teams leverage AI-driven adversarial techniques to identify vulnerabilities in complex systems. Collaboration through continuous purple teaming fosters real-time intelligence sharing, improving overall cybersecurity resilience against evolving attack vectors.
Red Team vs Blue Team Infographic
 difterm.com
difterm.com