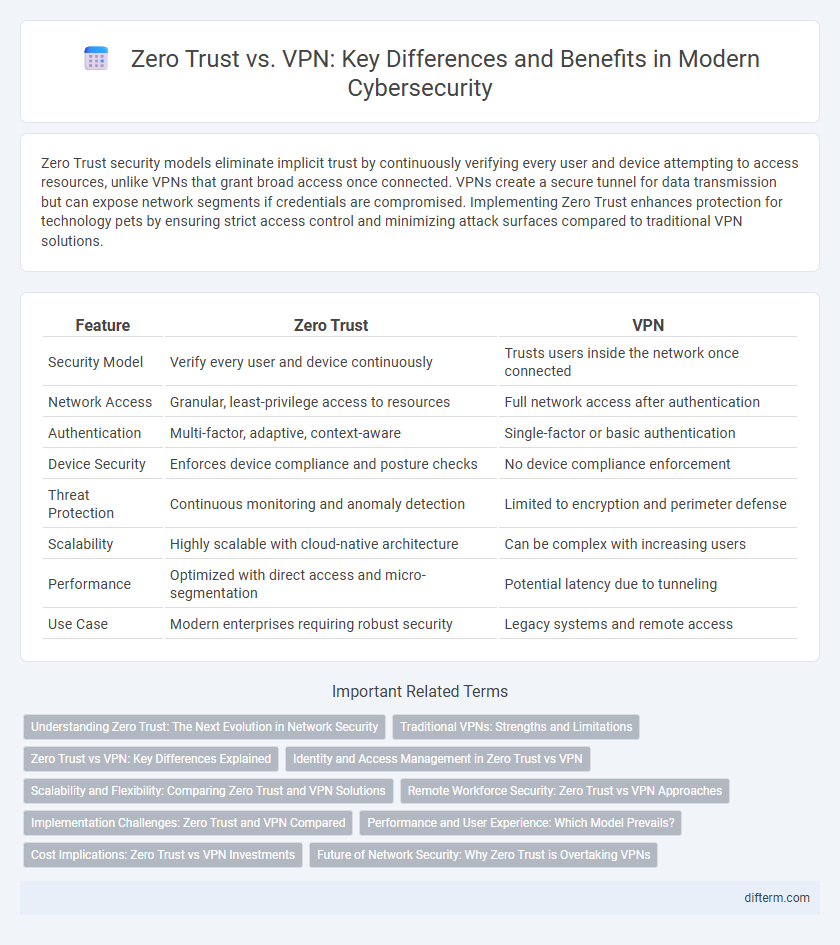
Zero Trust security models eliminate implicit trust by continuously verifying every user and device attempting to access resources, unlike VPNs that grant broad access once connected. VPNs create a secure tunnel for data transmission but can expose network segments if credentials are compromised. Implementing Zero Trust enhances protection for technology pets by ensuring strict access control and minimizing attack surfaces compared to traditional VPN solutions.
Table of Comparison
| Feature | Zero Trust | VPN |
|---|---|---|
| Security Model | Verify every user and device continuously | Trusts users inside the network once connected |
| Network Access | Granular, least-privilege access to resources | Full network access after authentication |
| Authentication | Multi-factor, adaptive, context-aware | Single-factor or basic authentication |
| Device Security | Enforces device compliance and posture checks | No device compliance enforcement |
| Threat Protection | Continuous monitoring and anomaly detection | Limited to encryption and perimeter defense |
| Scalability | Highly scalable with cloud-native architecture | Can be complex with increasing users |
| Performance | Optimized with direct access and micro-segmentation | Potential latency due to tunneling |
| Use Case | Modern enterprises requiring robust security | Legacy systems and remote access |
Understanding Zero Trust: The Next Evolution in Network Security
Zero Trust architecture redefines network security by eliminating implicit trust and continuously verifying every access request, unlike traditional VPNs that grant broad network access once connected. This model uses granular access controls and real-time analytics to minimize attack surfaces and prevent lateral movement within networks. As cyber threats evolve, Zero Trust provides a robust framework to safeguard sensitive data and applications beyond the perimeter-based approach of VPNs.
Traditional VPNs: Strengths and Limitations
Traditional VPNs offer secure remote access by encrypting data traffic between users and the corporate network, providing a reliable shield against eavesdropping and unauthorized interception. However, VPNs inherently trust devices once connected, which creates vulnerabilities if endpoints are compromised, leading to potential lateral movement within the network. Their dependence on perimeter-based security models limits visibility and control over internal traffic, making them less effective against modern, sophisticated cyber threats compared to zero trust architectures.
Zero Trust vs VPN: Key Differences Explained
Zero Trust architecture eliminates implicit trust by continuously verifying every access request based on user identity, device health, and context, whereas VPNs primarily create secure tunnels for remote access without granular verification. Zero Trust enforces least privilege access and segmented network policies to minimize attack surfaces, contrasting with VPNs that often grant broader network access once connected. The fundamental difference lies in Zero Trust's proactive security posture compared to VPN's perimeter-based security model.
Identity and Access Management in Zero Trust vs VPN
Zero Trust architecture enhances Identity and Access Management (IAM) by continuously verifying user identities and enforcing least-privilege access regardless of network location, unlike traditional VPNs that grant broad network access after initial authentication. VPNs rely on perimeter-based security, often leading to over-privileged access once inside the network, whereas Zero Trust uses multifactor authentication, adaptive access controls, and real-time monitoring to secure resources granularly. The shift to Zero Trust IAM reduces insider threats and simplifies compliance by ensuring that access is dynamically aligned with user roles and contextual risk factors.
Scalability and Flexibility: Comparing Zero Trust and VPN Solutions
Zero Trust architecture offers superior scalability by allowing seamless expansion without compromising security, unlike traditional VPNs that often suffer from bandwidth and performance bottlenecks as user numbers grow. Flexible policy enforcement in Zero Trust enables tailored access controls based on user identity, device health, and context, while VPNs typically grant broad network access once connected, increasing security risks. As enterprises prioritize agile and secure remote access, Zero Trust frameworks provide dynamic adaptability that better accommodates evolving IT environments compared to static VPN solutions.
Remote Workforce Security: Zero Trust vs VPN Approaches
Zero Trust architecture enforces strict identity verification for every user and device attempting to access resources, significantly reducing the risk of unauthorized access in remote workforce scenarios. VPNs create secure tunnels for remote connections but often grant broader network access once connected, increasing potential exposure. Implementing Zero Trust principles enhances remote workforce security by minimizing attack surfaces and ensuring continuous risk assessment compared to traditional VPN solutions.
Implementation Challenges: Zero Trust and VPN Compared
Zero Trust architecture demands continuous verification of user identity and device security posture, complicating its implementation with the need for advanced authentication methods and granular access controls. VPNs often pose challenges related to scalability, network performance bottlenecks, and increased attack surfaces due to broad access granted once a connection is established. Enterprises adopting Zero Trust must invest in comprehensive monitoring and policy enforcement tools, while VPN implementations struggle with legacy infrastructure compatibility and managing encrypted traffic.
Performance and User Experience: Which Model Prevails?
Zero Trust architecture enhances performance by minimizing network exposure and continuously validating user access, reducing latency compared to traditional VPNs that route all traffic through central servers. Users experience seamless, faster connectivity with Zero Trust due to localized access controls and dynamic authentication, while VPNs often cause slower speeds and connection drops. Businesses adopting Zero Trust report improved productivity and security posture, highlighting its superiority in performance and user experience over VPN models.
Cost Implications: Zero Trust vs VPN Investments
Zero Trust architecture typically requires higher upfront investments due to continuous authentication, micro-segmentation, and advanced monitoring tools, whereas VPN solutions generally incur lower initial costs but may lead to increased long-term expenses in managing vulnerabilities and scalability. Operational expenses for Zero Trust can be optimized by reducing breach risks and streamlining access management, while VPNs often demand ongoing maintenance and infrastructure upgrades to support expanding remote workforces. The total cost of ownership favors Zero Trust for organizations prioritizing security resilience and regulatory compliance despite the steeper initial outlay.
Future of Network Security: Why Zero Trust is Overtaking VPNs
Zero Trust architecture is rapidly overtaking VPNs as the future of network security due to its principle of "never trust, always verify," which minimizes the attack surface by enforcing strict access controls regardless of user location. Unlike traditional VPNs that provide broad network access once connected, Zero Trust continuously authenticates and authorizes every transaction, significantly reducing risks associated with compromised credentials. Emerging cybersecurity trends highlight that organizations adopting Zero Trust frameworks experience lower breach rates and enhanced protection against sophisticated threats, making it the preferred choice for securing modern hybrid and cloud environments.
Zero trust vs VPN Infographic
 difterm.com
difterm.com