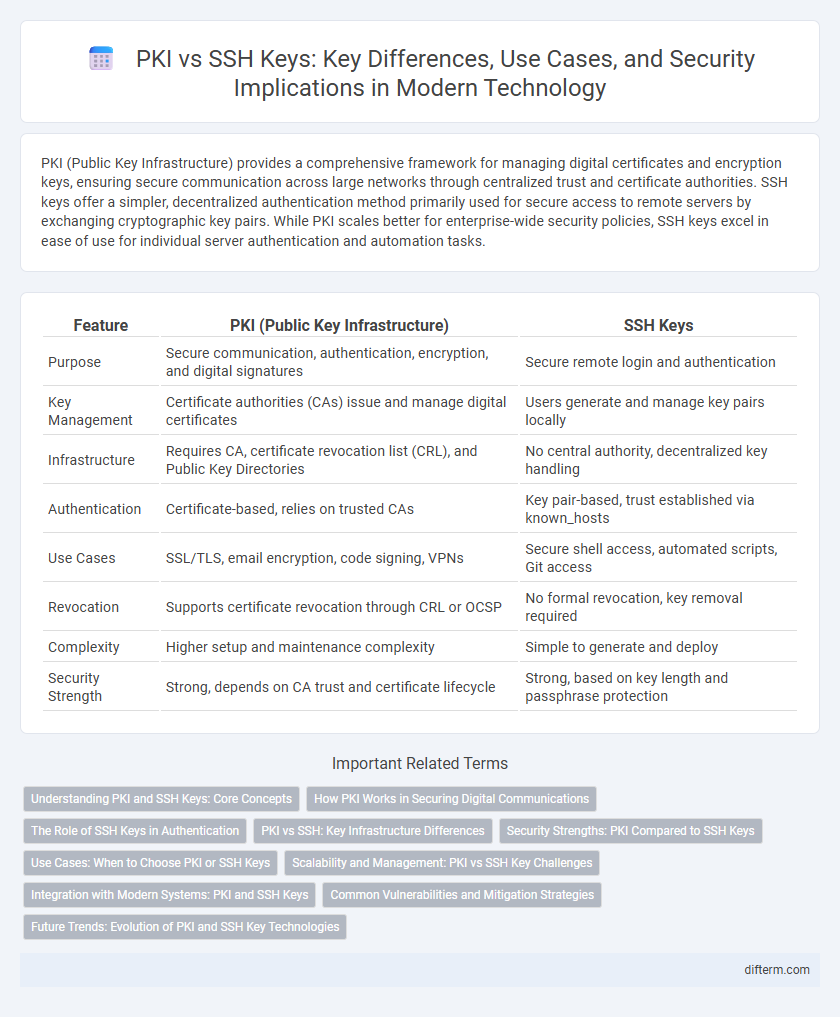
PKI (Public Key Infrastructure) provides a comprehensive framework for managing digital certificates and encryption keys, ensuring secure communication across large networks through centralized trust and certificate authorities. SSH keys offer a simpler, decentralized authentication method primarily used for secure access to remote servers by exchanging cryptographic key pairs. While PKI scales better for enterprise-wide security policies, SSH keys excel in ease of use for individual server authentication and automation tasks.
Table of Comparison
| Feature | PKI (Public Key Infrastructure) | SSH Keys |
|---|---|---|
| Purpose | Secure communication, authentication, encryption, and digital signatures | Secure remote login and authentication |
| Key Management | Certificate authorities (CAs) issue and manage digital certificates | Users generate and manage key pairs locally |
| Infrastructure | Requires CA, certificate revocation list (CRL), and Public Key Directories | No central authority, decentralized key handling |
| Authentication | Certificate-based, relies on trusted CAs | Key pair-based, trust established via known_hosts |
| Use Cases | SSL/TLS, email encryption, code signing, VPNs | Secure shell access, automated scripts, Git access |
| Revocation | Supports certificate revocation through CRL or OCSP | No formal revocation, key removal required |
| Complexity | Higher setup and maintenance complexity | Simple to generate and deploy |
| Security Strength | Strong, depends on CA trust and certificate lifecycle | Strong, based on key length and passphrase protection |
Understanding PKI and SSH Keys: Core Concepts
Public Key Infrastructure (PKI) establishes a trusted framework for managing digital certificates and encryption keys, ensuring secure communication through a centralized Certificate Authority (CA). SSH keys utilize asymmetric cryptography for secure remote access, relying on a pair of cryptographic keys--public and private--to authenticate users without transmitting passwords. Understanding the core concepts of PKI's certificate-based trust model versus SSH key's direct keypair authentication is essential for implementing robust security protocols in technology environments.
How PKI Works in Securing Digital Communications
Public Key Infrastructure (PKI) secures digital communications by using a hierarchical system of digital certificates issued by trusted Certificate Authorities (CAs) to verify the identity of entities. PKI employs asymmetric cryptography, generating a pair of keys: a public key for encryption and a private key for decryption, ensuring confidentiality and authentication. This framework enables secure data exchange, digital signatures, and certificate revocation management, providing robust trust and integrity across networks.
The Role of SSH Keys in Authentication
SSH keys play a critical role in authentication by providing a secure, encrypted method for verifying user identities without relying on passwords. Unlike traditional Public Key Infrastructure (PKI), SSH keys are specifically designed for secure shell access to remote systems, enabling efficient, password-less login through asymmetric cryptography. This approach enhances security and convenience in managing access to servers, making SSH keys a preferred authentication method in modern IT environments.
PKI vs SSH: Key Infrastructure Differences
Public Key Infrastructure (PKI) relies on a hierarchical, certificate-based system managed by trusted Certificate Authorities (CAs) to issue, validate, and revoke digital certificates, enabling scalable and centralized authentication. SSH keys operate primarily on a decentralized model, where users generate key pairs locally, and public keys are manually distributed and stored on individual servers, focusing on specific secure shell access. PKI's structured certificate management offers enhanced control and trust verification compared to the simpler, direct public key exchange inherent in SSH key-based authentication.
Security Strengths: PKI Compared to SSH Keys
Public Key Infrastructure (PKI) offers enhanced security strengths over SSH keys by providing a scalable framework for managing digital certificates and revocation processes, ensuring robust authentication and data integrity. PKI supports hierarchical trust models with Certificate Authorities (CAs) that validate identities, reducing the risk of man-in-the-middle attacks compared to standalone SSH keys. Its use of X.509 certificates and centralized management enables stronger encryption standards and lifecycle control, making it ideal for enterprise-level security requirements.
Use Cases: When to Choose PKI or SSH Keys
PKI is ideal for large-scale environments requiring centralized management and strong authentication across diverse services, such as enterprise VPNs, secure email, and web servers. SSH keys provide a streamlined solution for secure, direct access to individual servers and systems, commonly used by developers and system administrators for efficient remote management. Choosing between PKI and SSH keys depends on the need for scalability, complexity of infrastructure, and the intended use case for secure communication or access control.
Scalability and Management: PKI vs SSH Key Challenges
PKI systems offer superior scalability through centralized certificate authorities that simplify key issuance, renewal, and revocation across large enterprises, reducing administrative overhead significantly. In contrast, SSH key management becomes cumbersome as the number of users and devices grows, often requiring manual key distribution and periodic rotation to maintain security. The centralized nature of PKI enables automated lifecycle management and robust policy enforcement, whereas SSH key solutions frequently struggle with decentralized key storage and inconsistent access controls.
Integration with Modern Systems: PKI and SSH Keys
PKI (Public Key Infrastructure) and SSH keys both provide secure authentication mechanisms, but PKI excels in integration with modern systems through its standardized certificate management, scalability, and compatibility with enterprise environments such as Active Directory and cloud platforms. SSH keys offer simplicity and direct access control, primarily suited for secure shell access on individual servers or small-scale environments without the overhead of certificate authorities. Enterprises increasingly favor PKI for its centralized policy enforcement, automated certificate lifecycle management, and interoperability with DevOps tools, while SSH keys remain essential for lightweight, server-specific authentication.
Common Vulnerabilities and Mitigation Strategies
PKI systems often face vulnerabilities such as certificate authority compromise, certificate spoofing, and man-in-the-middle attacks, mitigated by stringent CA management, certificate pinning, and regular key rotation. SSH keys are susceptible to unauthorized access due to weak key storage, stolen private keys, and lack of passphrase protection; implementing hardware security modules (HSMs), enforcing passphrase policies, and using key revocation lists can significantly reduce these risks. Both frameworks require continuous monitoring, timely updates, and adherence to best practices to maintain robust security postures against evolving cyber threats.
Future Trends: Evolution of PKI and SSH Key Technologies
Future trends in technology emphasize the integration of quantum-resistant algorithms into PKI infrastructures to enhance security against emerging quantum computing threats. SSH key technologies are evolving with automated key rotation and machine learning-based anomaly detection to mitigate unauthorized access risks. Both PKI and SSH systems increasingly adopt blockchain for decentralized trust management, improving transparency and resilience in digital identity verification.
PKI vs SSH keys Infographic
 difterm.com
difterm.com