TLS termination offloads the encryption and decryption process from backend servers to a dedicated proxy, improving server performance by handling secure connections at the edge. SSL passthrough allows encrypted traffic to be forwarded directly to backend servers without decryption, maintaining end-to-end encryption but requiring servers to manage the computational load. Choosing between TLS termination and SSL passthrough depends on the balance between security requirements and server resource optimization.
Table of Comparison
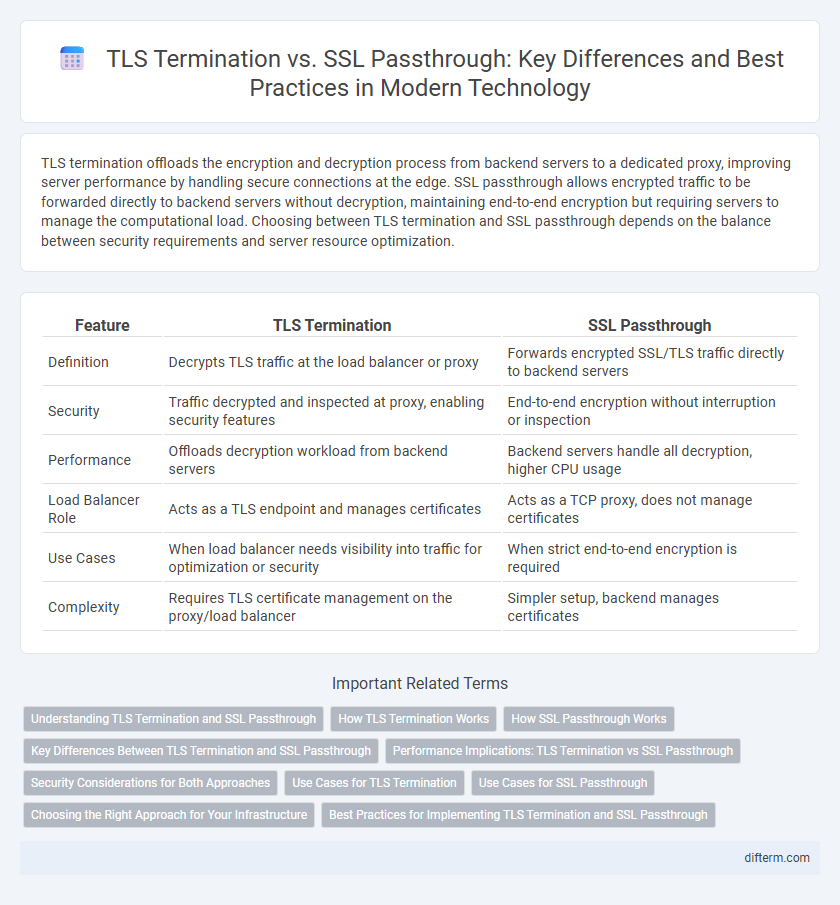
| Feature | TLS Termination | SSL Passthrough |
|---|---|---|
| Definition | Decrypts TLS traffic at the load balancer or proxy | Forwards encrypted SSL/TLS traffic directly to backend servers |
| Security | Traffic decrypted and inspected at proxy, enabling security features | End-to-end encryption without interruption or inspection |
| Performance | Offloads decryption workload from backend servers | Backend servers handle all decryption, higher CPU usage |
| Load Balancer Role | Acts as a TLS endpoint and manages certificates | Acts as a TCP proxy, does not manage certificates |
| Use Cases | When load balancer needs visibility into traffic for optimization or security | When strict end-to-end encryption is required |
| Complexity | Requires TLS certificate management on the proxy/load balancer | Simpler setup, backend manages certificates |
Understanding TLS Termination and SSL Passthrough
TLS termination involves decrypting encrypted traffic at the load balancer or proxy server, enabling inspection and routing based on application-level data, while SSL passthrough forwards encrypted data directly to the backend server without decryption. TLS termination reduces server load and simplifies certificate management but requires trust in the intermediary device handling decryption. SSL passthrough preserves end-to-end encryption, enhancing security for sensitive applications but limits traffic inspection and load balancing capabilities.
How TLS Termination Works
TLS termination involves decrypting encrypted traffic at the load balancer or proxy server, which offloads the decryption workload from backend servers and enables inspection of plaintext data for security or routing decisions. This process requires the load balancer to have the TLS certificates and private keys to establish secure connections with clients while forwarding unencrypted data to internal servers. By handling encryption and decryption at the edge, TLS termination improves backend server performance and simplifies certificate management.
How SSL Passthrough Works
SSL Passthrough works by allowing encrypted traffic to pass directly from the client to the backend server without decryption at the load balancer, preserving end-to-end encryption. This method relies on the backend server to handle the SSL/TLS handshake and decryption, ensuring that sensitive data remains secure throughout the network. It is commonly used in environments where maintaining encryption integrity and minimizing latency are critical.
Key Differences Between TLS Termination and SSL Passthrough
TLS termination decrypts incoming encrypted traffic at the load balancer or proxy, allowing inspection and routing based on unencrypted data, whereas SSL passthrough forwards encrypted traffic directly to the backend server without decryption. TLS termination improves performance and enables advanced features like content-based routing and security scanning, while SSL passthrough maintains end-to-end encryption for sensitive data. The choice between TLS termination and SSL passthrough impacts security posture, resource utilization, and the complexity of backend server configuration.
Performance Implications: TLS Termination vs SSL Passthrough
TLS termination offloads encryption and decryption processes to a dedicated proxy or load balancer, reducing the computational load on backend servers and improving overall response times. SSL passthrough maintains end-to-end encryption by forwarding encrypted traffic directly to backend servers, which can increase CPU usage on those servers and potentially introduce latency. Choosing TLS termination enhances performance in high-traffic environments, while SSL passthrough prioritizes security at the cost of greater backend resource consumption.
Security Considerations for Both Approaches
TLS termination decrypts traffic at the load balancer, enabling detailed inspection and threat detection but increasing the attack surface by exposing plaintext internally. SSL passthrough preserves end-to-end encryption, maintaining data confidentiality but limiting the ability to inspect or filter malicious content. Choosing between these methods requires balancing security needs: TLS termination offers enhanced visibility while SSL passthrough prioritizes encrypted data integrity and protection against man-in-the-middle attacks.
Use Cases for TLS Termination
TLS termination is ideal for applications requiring deep packet inspection, caching, or load balancing, as it decrypts traffic at the edge before forwarding it internally. Common use cases include web application firewalls, content delivery networks, and reverse proxies where security policies must be enforced. This approach reduces CPU overhead on backend servers by offloading the encryption and decryption process.
Use Cases for SSL Passthrough
SSL Passthrough is ideal for applications requiring end-to-end encryption, ensuring that encrypted traffic remains intact from the client to the backend server without decryption at the load balancer. This approach is particularly useful for backend systems handling sensitive data, such as banking platforms or healthcare applications, where regulatory compliance mandates strict encryption standards. It also simplifies certificate management by offloading SSL termination to the backend servers, reducing the attack surface on intermediate network devices.
Choosing the Right Approach for Your Infrastructure
Selecting between TLS termination and SSL passthrough depends on your infrastructure's security requirements and performance goals. TLS termination offloads encryption tasks to the load balancer, improving backend efficiency and enabling advanced traffic inspection, while SSL passthrough maintains end-to-end encryption by forwarding encrypted traffic directly to backend servers. Analyzing factors such as certificate management complexity, latency sensitivity, and compliance needs ensures you choose the optimal approach for secure and scalable network architecture.
Best Practices for Implementing TLS Termination and SSL Passthrough
Implementing TLS termination involves decrypting SSL/TLS traffic at the load balancer or proxy to inspect and route requests efficiently, enhancing performance and enabling advanced security features like HTTP/2 and Web Application Firewall integration. SSL passthrough maintains end-to-end encryption by forwarding encrypted traffic directly to backend servers, ideal for environments requiring strict data privacy and compliance, but it limits load balancer visibility into traffic. Best practices recommend choosing TLS termination for centralized security management and SSL passthrough when backend server security policies or certificate management dictate, ensuring proper certificate renewal processes and strong cipher suites configurations in both cases.
TLS termination vs SSL passthrough Infographic
 difterm.com
difterm.com